Use Case:
Enrich slack notifications with Wazuh FIM & Vulnerability alerts details.
Painless scripts (Mustache templates):
- Wazuh File Integrity Monitoring alerts information:
Wazuh File Integrity Monitoring
{{#ctx.results.0.hits.hits}}
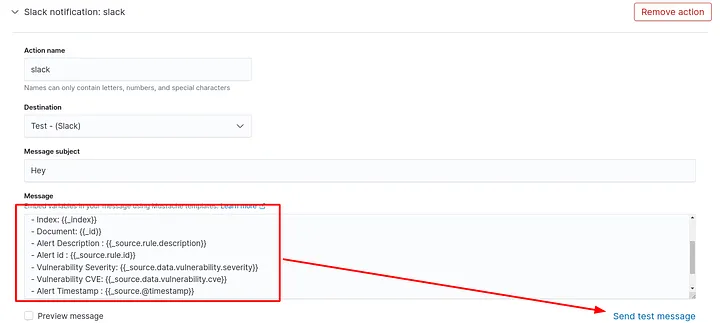
- Index: {{_index}}
- Document: {{_id}}
- Alert Description : {{_source.rule.description}}
- Alert id : {{_source.rule.id}}
- FIM path : {{_source.syscheck.path}}
- FIM event: {{_source.syscheck.event}}
- Alert Timestamp : {{_source.@timestamp}}
{{/ctx.results.0.hits.hits}}- Wazuh Vulnerability alerts information:
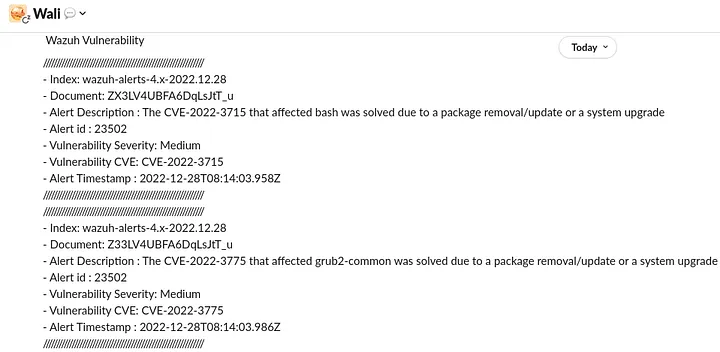
Wazuh Vulnerability
{{#ctx.results.0.hits.hits}}
- Index: {{_index}}
- Document: {{_id}}
- Alert Description : {{_source.rule.description}}
- Alert id : {{_source.rule.id}}
- Vulnerability Severity: {{_source.data.vulnerability.severity}}
- Vulnerability CVE: {{_source.data.vulnerability.cve}}
- Alert Timestamp : {{_source.@timestamp}}
{{/ctx.results.0.hits.hits}}Opensearch/Wazuh Monitor Queries:
- FIM:
{
"query": {
"bool": {
"must": [],
"filter": [
{
"match_all": {}
},
{
"match_phrase": {
"rule.groups": "syscheck"
}
},
{
"range": {
"timestamp": {
"gt": "now-5m",
"lte": "now",
"format": "strict_date_optional_time"
}
}
}
]
}
}
}- Vulnerability:
{
"query": {
"bool": {
"must": [],
"filter": [
{
"match_all": {}
},
{
"match_phrase": {
"rule.groups": "vulnerability-detector"
}
},
{
"range": {
"timestamp": {
"gt": "now-5m",
"lte": "now",
"format": "strict_date_optional_time"
}
}
}
]
}
}
}Alerting Module Configuration:
The monitor must be configured using Extraction query editor. Then add & test the query:
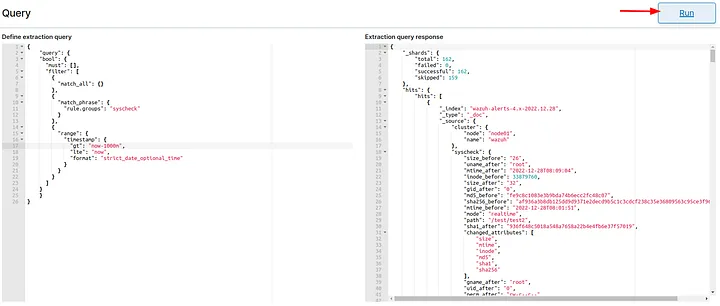
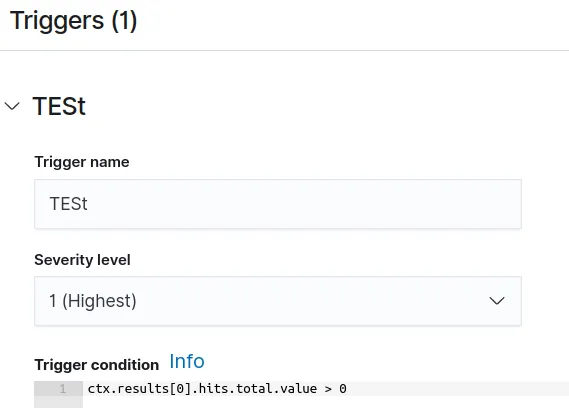
Define a simple trigger whenever the query return values higher than 0:
Add your painless script, then send a test message:
Slack notification result:
DEMO:
Hope you find it useful 🙂
51 responses to “Enrich Opensearch/Wazuh Alerting module notification using Painless Scripts (Mustache templates)”
Normally I don’t read post on blogs, but I would like to say that this write-up very compelled me to check out and do it! Your writing taste has been amazed me. Thanks, quite great article.
stromectol for sale – candesartan pills order generic tegretol 400mg
order isotretinoin 20mg sale – buy zyvox 600mg pill order linezolid 600 mg without prescription
amoxil online – order combivent 100 mcg for sale buy ipratropium cheap
omnacortil 40mg tablet – azipro 500mg ca progesterone price
cheap gabapentin for sale – clomipramine over the counter sporanox cheap
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
purchase augmentin online cheap – augmentin buy online purchase cymbalta generic
buy vibra-tabs pill – doxycycline generic glipizide 5mg for sale
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
buy augmentin 375mg pills – augmentin pills cymbalta 40mg cost
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
semaglutide 14mg sale – cheap semaglutide periactin pills
I don’t think the title of your enticle matches the content lol. Just kidding, mainly because I had some doubts after reading the enticle.
order tizanidine sale – buy cheap microzide buy hydrochlorothiazide 25 mg sale
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Your article helped me a lot, is there any more related content? Thanks!
cialis 5mg brand – overnight delivery for cialis sildenafil for women
buy viagra 50mg online – order generic cialis 40mg otc cialis
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Men Over 50, Read THIS Before Using TRT Testosterone Therapy
Section 1: History
Testosterone Replacement Therapy (TRT) has evolved significantly since
its inception in the early 20th century. Originally developed for individuals with severe testosterone deficiencies, TRT gained traction in the 1930s and 1940s as a treatment for various conditions, including infertility and hypogonadism.
Over time, its applications expanded to include age-related declines in testosterone levels, particularly in men over 50.
While early use of TRT was often controversial, due to concerns about eugenic practices and the potential for misuse, it has
since become a more widely accepted medical intervention when prescribed appropriately.
Section 2: The Present Consensus
Today, TRT is considered a viable treatment option for men with abnormally low
testosterone levels, as defined by diagnostic criteria.
These criteria include low bioavailable testosterone levels, which can be measured
through blood tests. Beyond just addressing hypogonadism, TRT
is also used to counteract the natural decline in testosterone
that occurs with aging, often improving symptoms like muscle loss, bone density reduction,
and sexual dysfunction.
Who Is an Appropriate Candidate?
Men over 50 considering TRT should consult with their healthcare provider to determine if their testosterone levels fall outside the
normal range. While lower testosterone is a
natural part of aging, significant declines may warrant intervention.
However, it’s important to differentiate between men with genuinely low testosterone and those experiencing age-related dips, as
the latter may not necessarily require treatment.
What If Testosterone Levels Aren’t Abnormally Low?
If test results show normal or high testosterone levels, TRT is not recommended.
In such cases, lifestyle modifications, dietary adjustments,
and exercise programs are often more effective for addressing age-related declines.
Additionally, psychological factors like depression or
metabolic conditions may contribute to symptoms that mimic those of low testosterone.
Risks of Testosterone Therapy
While TRT can offer benefits, it is not without risks.
Side effects may include cardiovascular issues, such as increased blood pressure and cholesterol levels, as well as potential
complications like testicular atrophy. Long-term
use has also been linked to a higher risk of prostate cancer, though this association is still being studied.
Section 3: The Controversy
The debate surrounding TRT continues to rage, particularly in light of
recent clinical trials. The TRAVERSE trial, for example, has sparked discussions
about the appropriateness of TRT for older men with mild testosterone deficits.
Proponents argue that TRT can enhance quality of life
and maintain physical function, while critics caution against its overuse
and the potential for misuse.
A Closer Look at the TRAVERSE Trial
The TRAVERSE trial, published in 2022, investigated the
effects of TRT on men over 50 with testosterone
levels in the lower range but not abnormally low. The study
found that TRT could improve muscle strength and sexual function, though these benefits were modest and not universally
observed. Critics argue that the trial downplayed risks and may have
conflated age-related declines with true deficiency.
Section 4: Takeaways
For men over 50 considering TRT, it’s crucial to weigh potential
benefits against risks. While TRT can be an effective treatment for certain conditions, such
as hypogonadism and age-related decline, it is not a one-size-fits-all solution. Men should work closely with
their healthcare providers to determine if treatment is appropriate based on individual circumstances.
Close
References
1. National Institute on Aging (2023). Testosterone Replacement Therapy: What You Need to Know.
Retrieved from NIA website.
2. Journal of Clinical Endocrinology & Metabolism
(2022). TRAVERSE Trial Results. Retrieved from Journal website.
Introducing MicroVitamin
MicroVitamin is a leading provider of premium vitamins and supplements tailored to meet the unique needs of men over 50.
Our products are designed with scientific precision to support aging gracefully, including optimal testosterone levels and overall health.
Explore our collection today!
Related Posts
– The Truth About Testosterone Replacement Therapy: What You Should Know
– Maintaining Male Health in the Golden Years
– How to Keep Your Energy Levels Up as You Age
About Dr. Brad Stanfield
Dr. Brad Stanfield is a leading expert in endocrinology and
male health, with over 25 years of experience in treating
men over 50. He has contributed to numerous studies
on testosterone replacement therapy and its impact on aging males.
Follow him on social media for the latest updates
in male health!
comment
Leave a comment below to share your thoughts on this article or ask
questions about TRT for men over 50. Your input helps
us better serve the community!
My webpage: Corticosteroids Side Effects Long Term
lipitor 20mg cost – atorvastatin 80mg sale zestril 5mg drug
order cenforce pill – buy generic glucophage online metformin 500mg oral
lipitor 20mg cheap – lipitor without prescription zestril 10mg tablet
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Hello! I could have sworn I’ve visited this site before but after going through some of the posts I realized it’s new to me. Anyhow, I’m definitely delighted I found it and I’ll be book-marking it and checking back regularly!
mostbet.com rasmiy sayt mostbet3019.ru .
hoiwln
lipitor pills – buy lisinopril 2.5mg sale zestril 10mg uk
Generally I do not read post on blogs, but I wish to say that this write-up very forced me to try and do so! Your writing style has been amazed me. Thanks, quite nice post.
Your content always manages to captivate and educate me. Keep up the fantastic work!
Wonderful web site. A lot of useful info here. I’m sending it to several friends ans also sharing in delicious. And certainly, thank you to your effort!
buy prilosec 20mg generic – atenolol sale order atenolol generic
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/uk-UA/register?ref=W0BCQMF1
Good Morning Blessings. For he hath made Him to be sin for us, who knew no sin; that we could be made the righteousness of God in Him.
AJION PpB VkXXI
depo-medrol buy online – methylprednisolone cost aristocort 4mg pill
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://www.binance.com/pt-PT/join?ref=DB40ITMB
вывод из запоя дешево краснодар вывод из запоя дешево краснодар .
Your confidence in us is our top priority. That’s why we operate with absolutehonesty and dedication to your case.Experience the relief of recovering your QIWI wallet balance with our specialized services.
I like this post, enjoyed this one thanks for posting.
clarinex 5mg drug – claritin cheap buy dapoxetine 90mg pill
cytotec 200mcg generic – misoprostol drug diltiazem 180mg cost
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.