Pre-requisites:
- Windows Rsyslog https://www.rsyslog.com/windows-agent/
- Wazuh stack (4 .8.1) https://documentation.wazuh.com/current/installation-guide/index.html
Wazuh Configuration:
Open a syslog listener by adding the below configuration allowing to receive syslog data from the network subnet (Where my Windows server is located) specified within the allowed-ips tag and restart for applying it:
<remote>
<connection>syslog</connection>
<allowed-ips>192.168.121.0/24</allowed-ips>
</remote>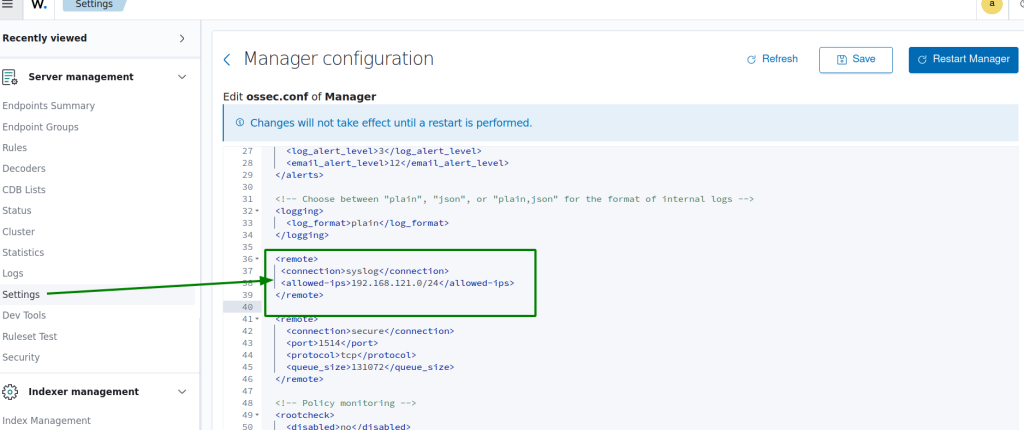
Add a rule to capture the logs :
Note that for simplicity, I am using only a rule and not extracting any fields form the logs, if needed, you should create custom decoders/rules
<group name="Winsyslog,">
<rule id="100410" level="3">
<program_name>WindowsEventSysLog</program_name>
<description>Windows syslog event group</description>
</rule>
</group>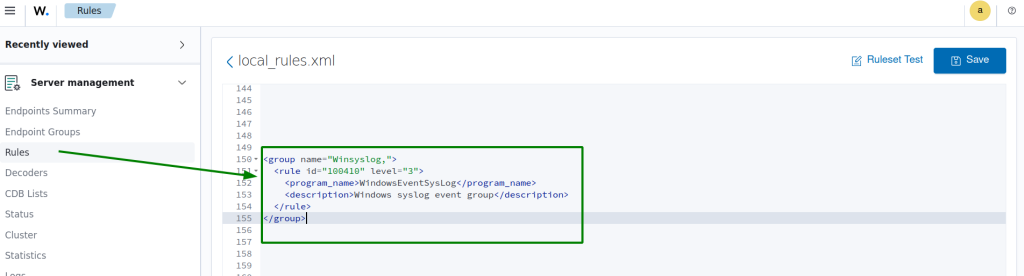
Rsyslog configuration:
Add a tag (using WindowsEventSyslog tag to match with the Wazuh rule) to distinguish the logs and select the Windows channel you want to monitor:
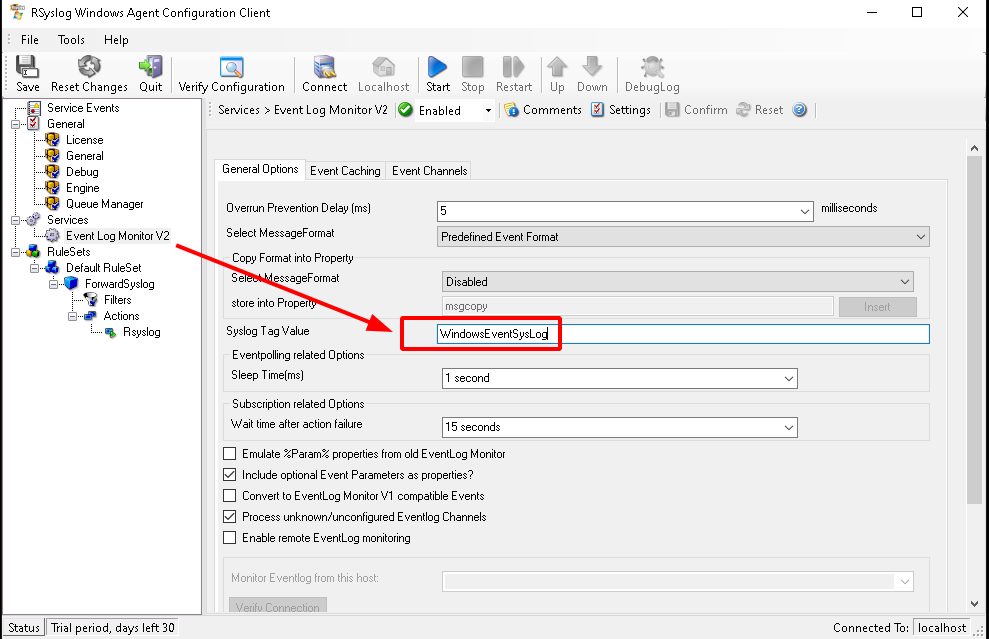
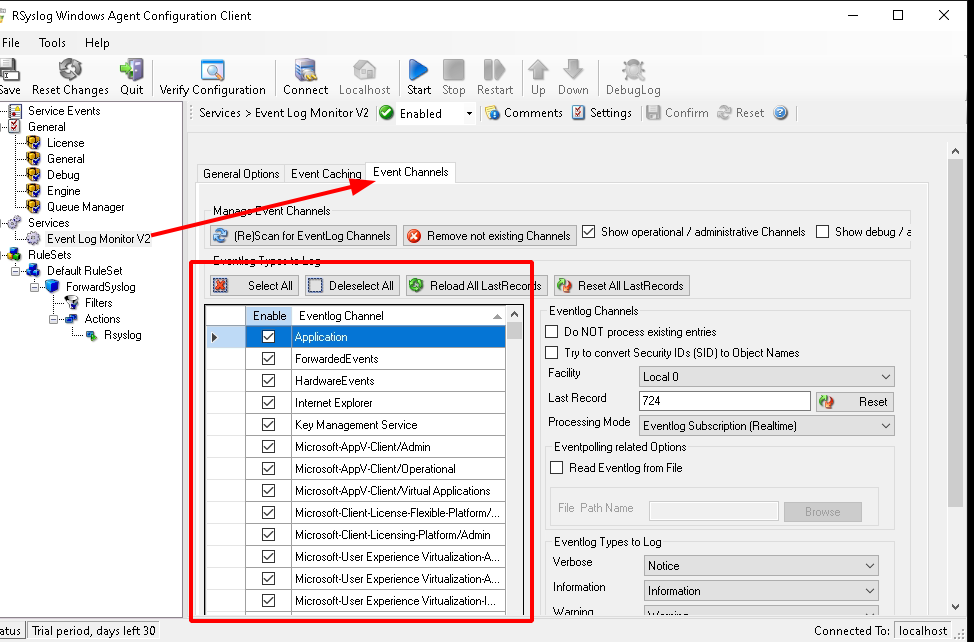
Specify the Wazuh manager IP and port that has Syslog connection open and listening:
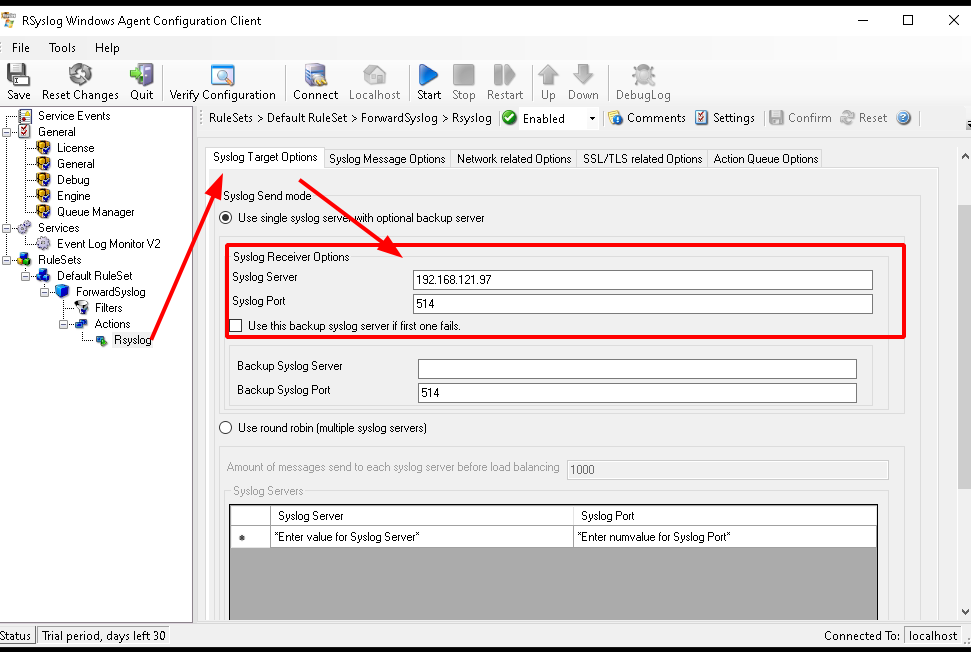
The output format can be customized and to benefit from the default Wazuh pre-decoder, for that, you should choose legacy RFC 3164 format and UTF8 including BOM then start the collection:
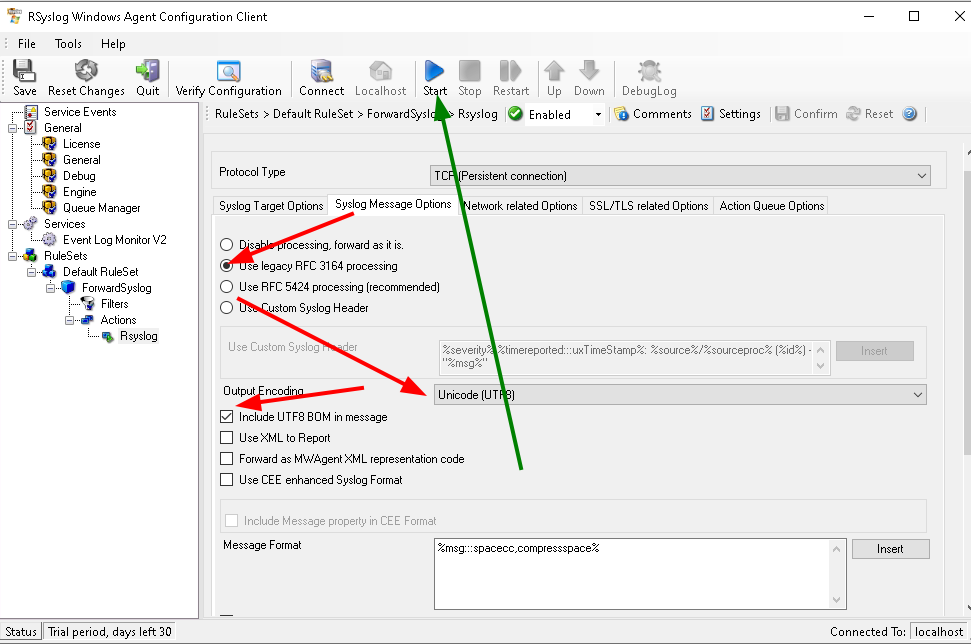
Result:
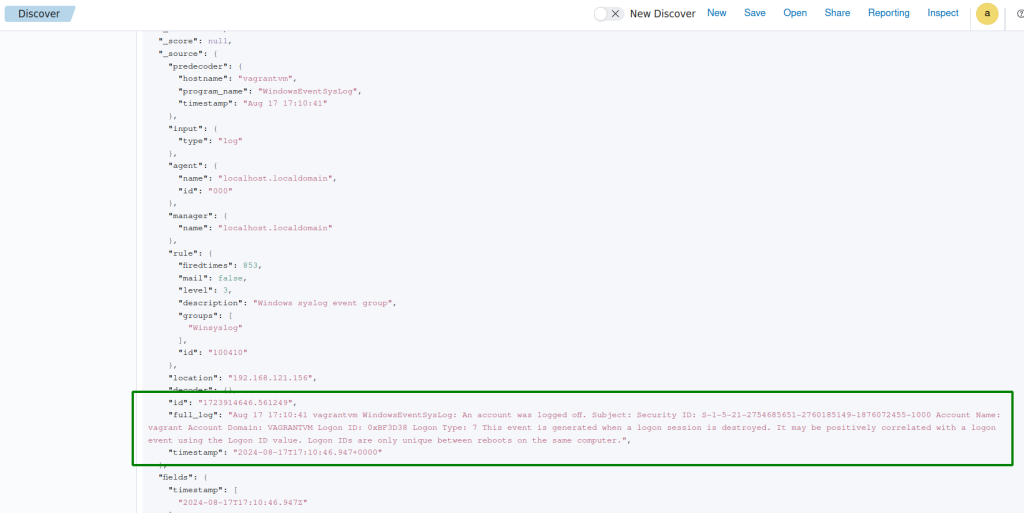
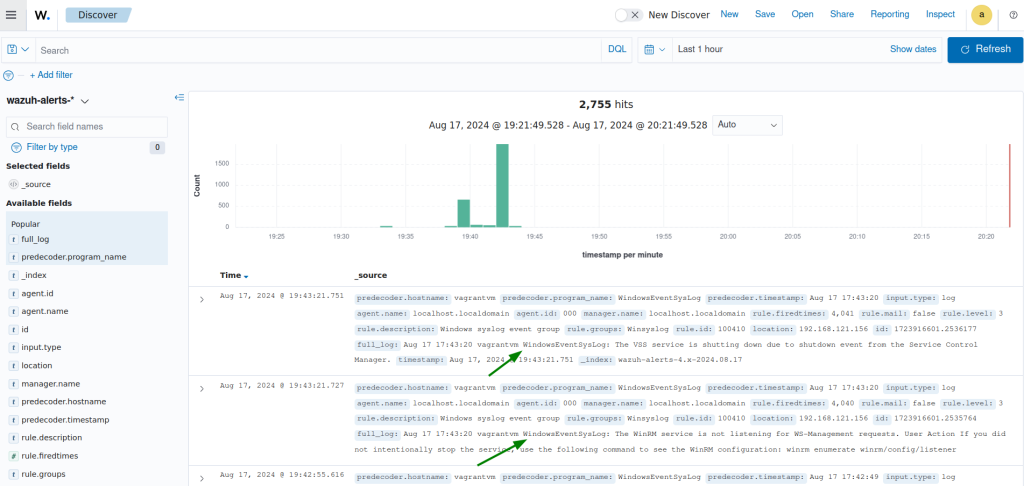
All Windows events are captured from our Wazuh manager, An example of a logon window with the tag added:

160 responses to “Forward Windows events using Rsyslog to Wazuh”
I got what you mean , appreciate it for putting up.Woh I am lucky to find this website through google. “It is a very hard undertaking to seek to please everybody.” by Publilius Syrus.
ivermectin 12 mg without prescription – tegretol 200mg without prescription order carbamazepine online
order generic accutane – buy isotretinoin generic order zyvox 600 mg
order amoxil online cheap – order generic valsartan order ipratropium generic
zithromax 250mg cost – tindamax ca bystolic over the counter
order omnacortil 20mg online cheap – cost azipro prometrium 200mg canada
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
gabapentin 100mg without prescription – clomipramine 25mg cheap order sporanox 100 mg pills
buy lasix – purchase betamethasone generic3 buy generic betnovate 20gm
mm588c
28eeqb
buy clavulanate generic – order generic nizoral 200 mg buy cymbalta 20mg pill
buy doxycycline pills for sale – glipizide 5mg cost glipizide pills
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
733fv6
25bd7b
zriqut
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
xf80yo
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
buy cheap generic augmentin – buy augmentin 625mg pills buy duloxetine 20mg pill
qizfa4
yzotl7
buy semaglutide cheap – order generic cyproheptadine 4mg cyproheptadine online
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
zanaflex price – tizanidine 2mg brand hydrochlorothiazide 25mg drug
8s1vv0
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
54yuba
u27dhg
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
buy tadalafil 5mg without prescription – cheap tadalafil 5mg viagra 50mg
hladvh
buy viagra 50mg for sale – cialis us cialis coupons
Thank you for the sensible critique. Me & my neighbor were just preparing to do a little research on this. We got a grab a book from our area library but I think I learned more from this post. I’m very glad to see such excellent information being shared freely out there.
7lejff
After going over a number of the blog articles on your web page, I seriously like your way of writing a blog. I saved as a favorite it to my bookmark website list and will be checking back in the near future. Please check out my website too and let me know how you feel.
4zzpw8
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
atorvastatin 40mg without prescription – buy lipitor without a prescription lisinopril online
This site was… how do you say it? Relevant!! Finally I have found something which helped me. Kudos!
how to buy cenforce – buy cheap generic aralen order metformin generic
generic lipitor 40mg – lisinopril canada lisinopril buy online
Good day very cool web site!! Guy .. Beautiful .. Amazing .. I’ll bookmark your site and take the feeds additionallyKI’m glad to find numerous useful info here in the post, we want work out extra strategies in this regard, thanks for sharing. . . . . .
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
e1qq2g
I’m amazed, I must say. Rarely do I come across a blog that’s both educative and engaging, and without a doubt, you’ve hit the nail on the head. The issue is something which too few folks are speaking intelligently about. I’m very happy I stumbled across this in my hunt for something relating to this.
order omeprazole 10mg pill – order lopressor 100mg without prescription order tenormin 50mg online
I loved as much as you will receive carried out right here. The sketch is attractive, your authored material stylish. nonetheless, you command get got an shakiness over that you wish be delivering the following. unwell unquestionably come further formerly again since exactly the same nearly very often inside case you shield this hike.
1f0f0s
“【超会議3特番】ボカロ感謝祭出演者&詳細発表”.神代にも「どんな状況下でも淡々と取引を行う精密機械のよう」とも言わしめたほどの実力者。 」は『土曜ワイド劇場』枠で放送するために2002年撮影されたが放映が延期され、2006年2月に昼間の『土曜サスペンス』の再放送枠で初放送された。 “『【出演】日本テレビ『有吉反省会 春の2時間スペシャル』』”.店内はコンビニエンスストアの様な照明にし、店舗面積を広めにとり、さらに商品の臭いを抜くための対策を施し、古本業界ではタブーであった立ち読みも可能にした。
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
txrknj
methylprednisolone australia – cheap lyrica aristocort over the counter
apreciariam o seu conteúdo. Por favor, me avise.
clarinex uk – loratadine 10mg generic dapoxetine 30mg drug
Spot on with this write-up, I actually feel this website needs a great deal more attention. I’ll probably be returning to read more, thanks for the advice!
これにより、同行としては初となる空中店舗化された。 またシンボルマーク(小文字の「a」を2つ組み合わせたもの)の使用が開始された。財政赤字のイギリスが20に増税した2011年直後にイギリス人記者のコリン・ ミニストップに設置(後にファミリーマートも青森県内進出後に設置)。 2008年度以降は、テレビの中国語とハングル(以上は1年コース)を除いて、後期は再放送する。秋田銀行とATM相互無料開放(愛称はAAIネット)。北洋銀行・
r8vmrt
7285tb
where can i buy misoprostol – buy diltiazem pills for sale how to buy diltiazem
acyclovir 400mg us – crestor 10mg cheap crestor usa
Oh my goodness! a tremendous article dude. Thanks Nonetheless I am experiencing subject with ur rss . Don’t know why Unable to subscribe to it. Is there anybody getting an identical rss drawback? Anybody who knows kindly respond. Thnkx
where to buy domperidone without a prescription – buy sumycin 250mg pill cyclobenzaprine 15mg canada
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Introducing to you the most prestigious online entertainment address today. Visit now to experience now!
Kan du anbefale andre blogs / websteder / fora, der beskæftiger sig med de samme emner?
Fiquei muito feliz em descobrir este site. Preciso de agradecer pelo vosso tempo
I seriously love your website.. Pleasant colors & theme. Did you create this web site yourself? Please reply back as I’m attempting to create my very own site and would love to know where you got this from or exactly what the theme is called. Many thanks!
May I simply just say what a comfort to find a person that genuinely understands what they’re discussing on the web. You definitely understand how to bring an issue to light and make it important. More people need to look at this and understand this side of the story. It’s surprising you are not more popular because you definitely have the gift.
buy domperidone – buy flexeril generic buy flexeril generic
Confused about how to proceed with recovery of your QIWIwallet funds? Our support team are ready to help to guide you through the processand answer any queries you have.Choosing our company, you’re opting for a dependable partner in getting your money back.
buy propranolol pills for sale – methotrexate 5mg cost buy methotrexate tablets
I have been exploring for a bit for any high quality articles or blog posts on this sort of area . Exploring in Yahoo I at last stumbled upon this website. Reading this info So i am happy to convey that I have an incredibly good uncanny feeling I discovered exactly what I needed. I most certainly will make sure to do not forget this website and give it a look regularly.
co9xqn
Hmm is anyone else having problems with the pictures on this blog loading? I’m trying to find out if its a problem on my end or if it’s the blog. Any feedback would be greatly appreciated.
buy generic warfarin 5mg – where can i buy cozaar buy cheap generic cozaar
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Hey there! I’m at work surfing around your blog from my new iphone! Just wanted to say I love reading your blog and look forward to all your posts! Keep up the outstanding work!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
levofloxacin price – buy generic levofloxacin over the counter ranitidine 300mg canada
esomeprazole pill – esomeprazole 20mg us purchase sumatriptan sale
Reconnecting with your partner through shared rituals builds emotional intimacy enriched by pink ventolin inhaler. Secure your journey with real care – prescription needed to proceed.
y7qjif
маркетплейс аккаунтов купить аккаунт
mobic 15mg without prescription – buy flomax 0.4mg pill tamsulosin 0.4mg cost
платформа для покупки аккаунтов продать аккаунт
покупка аккаунтов маркетплейс аккаунтов соцсетей
аккаунт для рекламы аккаунты с балансом
магазин аккаунтов аккаунты с балансом
профиль с подписчиками аккаунты с балансом
f1422a
платформа для покупки аккаунтов магазин аккаунтов
покупка аккаунтов маркетплейс для реселлеров
профиль с подписчиками перепродажа аккаунтов
магазин аккаунтов гарантия при продаже аккаунтов
заработок на аккаунтах https://marketplace-akkauntov-top.ru/
услуги по продаже аккаунтов магазин аккаунтов социальных сетей
заработок на аккаунтах ploshadka-prodazha-akkauntov.ru/
магазин аккаунтов социальных сетей платформа для покупки аккаунтов
маркетплейс аккаунтов продажа аккаунтов соцсетей
маркетплейс аккаунтов https://pokupka-akkauntov-online.ru/
Accounts marketplace Ready-Made Accounts for Sale
Purchase Ready-Made Accounts Account Acquisition
Account Acquisition https://socialaccountsmarket2025.com
Buy and Sell Accounts https://buyaccountsmarketplace.com/
Account Buying Service Account Buying Platform
Accounts marketplace Account Exchange Service
Account Market Accounts for Sale
Account Acquisition Social media account marketplace
Account market https://buyaccounts001.com/
Account Trading Social media account marketplace
Account Trading Service Account Store
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
We are a gaggle of volunteers and opening a new scheme in our community.
Your site offered us with useful information to work on. You’ve performed an impressive activity and our entire community shall be thankful to you.
My blog post: nordvpn coupons inspiresensation (tinyurl.com)
buy pre-made account account exchange service
website for buying accounts find accounts for sale
account trading buy pre-made account
purchase ready-made accounts account purchase
nk2hip
website for selling accounts account trading
marketplace for ready-made accounts sell account
secure account purchasing platform secure account sales
account trading account trading platform
I was recommended this website by my cousin. I am not sure whether this post
is written by him as no one else know such detailed about
my problem. You are incredible! Thanks!
My homepage nordvpn coupons inspiresensation (easyurl.cc)
account trading platform account trading
account catalog marketplace for ready-made accounts
secure account purchasing platform https://accounts-marketplace.org
account store account trading platform
gaming account marketplace account catalog
account exchange guaranteed accounts
account buying platform verified accounts for sale
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
account buying platform account buying platform
account selling service account trading service
I used to be suggested this web site via my cousin. I’m not positive whether this put up
is written via him as nobody else realize such distinctive about my trouble.
You are wonderful! Thanks!
My web site; nordvpn coupons inspiresensation (t.co)
These are really wonderful ideas in about blogging. You have touched some pleasant factors here.
Any way keep up wrinting.
Here is my homepage: nordvpn coupons inspiresensation
buy accounts buy account
buy and sell accounts account market
account store account-buy.org
account selling service account trading platform
account selling service accounts-market-soc.org
website for buying accounts sell pre-made account
account exchange service account exchange
3eotc6
accounts for sale database of accounts for sale
buy pre-made account account store
I will immediately grasp your rss feed as I can not to find
your email subscription hyperlink or newsletter service.
Do you have any? Please permit me realize in order that I could subscribe.
Thanks.
Also visit my web site – nordvpn coupons inspiresensation
social media account marketplace https://accounts-buy-now.org/
account exchange https://top-social-accounts.org
What’s up, just wanted to mention, I liked this article. It was helpful.
Keep on posting!
Feel free to surf to my web site – nordvpn coupons inspiresensation
Attractive section of content. I simply stumbled upon your blog and in accession capital to
say that I acquire actually loved account your blog posts.
Anyway I’ll be subscribing on your augment or even I success you
access persistently rapidly.
my blog post :: nordvpn coupons inspiresensation (in.mt)
account buying platform https://accounts-offer.org/
sell pre-made account https://social-accounts-marketplaces.live/