Use case:
Set up Keycloak (Version 26.0.5) for Authentication using the OpenID protocol in Wazuh (Version 4.9.1).
Keycloak Configuration:
- Create a new OpenID Connect client, specify the
Valid redirect URIs&Valid post logout redirect URIsto your Wazuh dashboard, and add a token mapper as shown below :
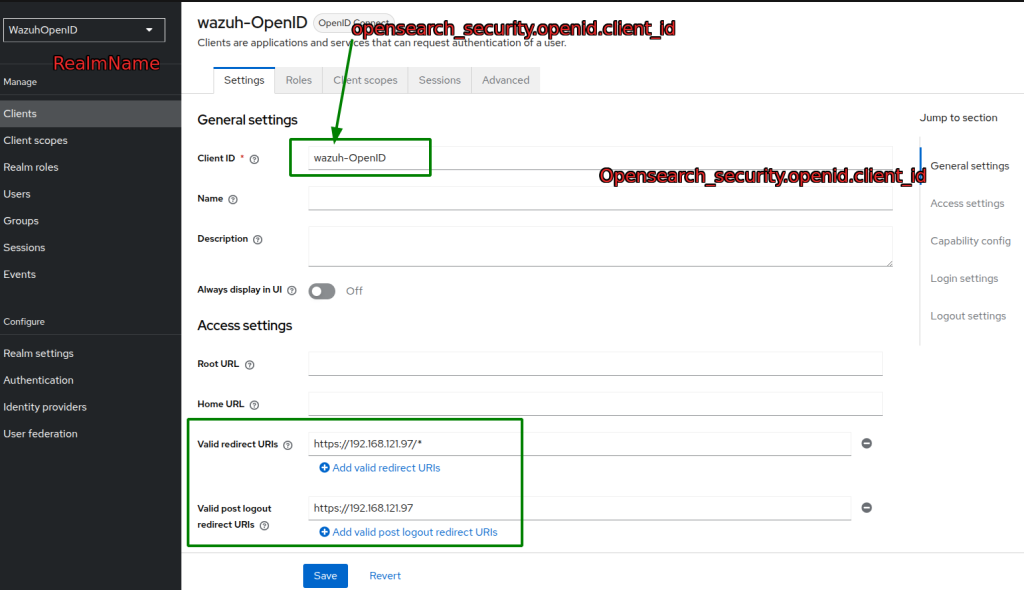
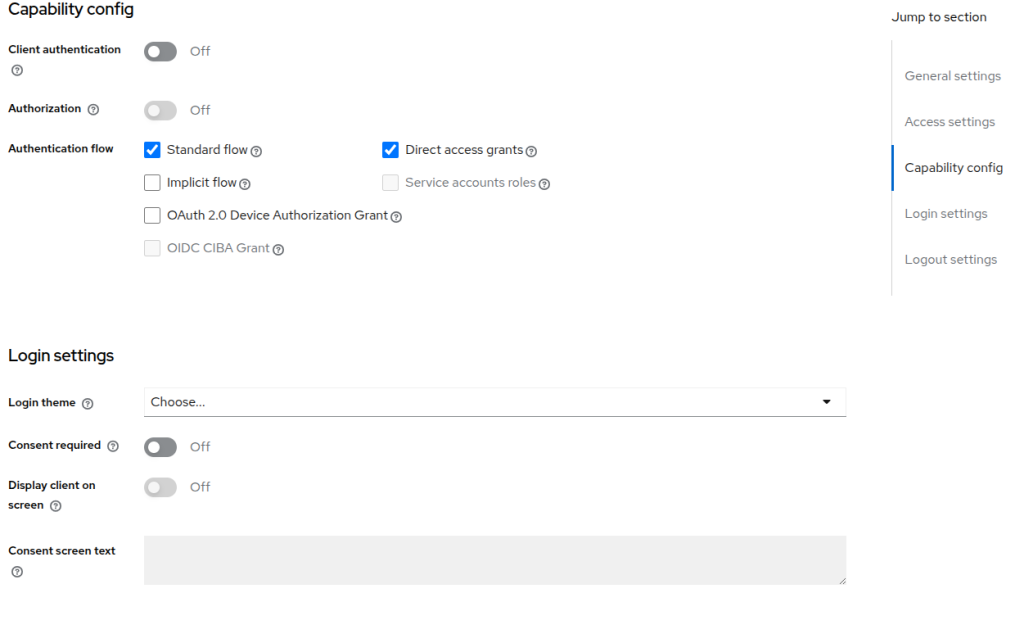
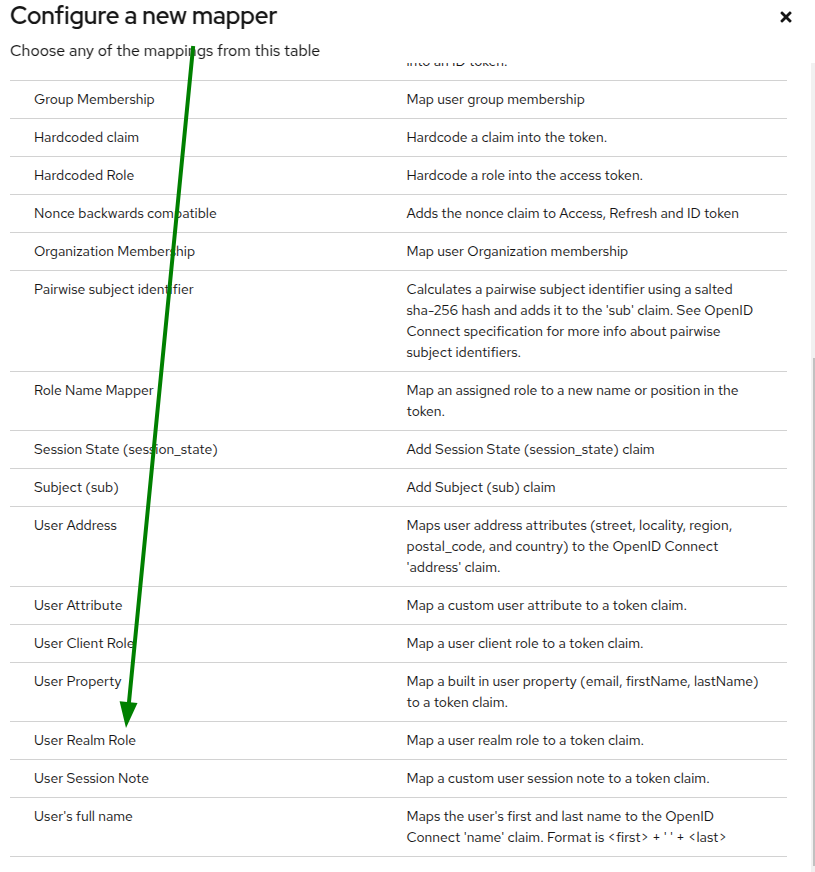
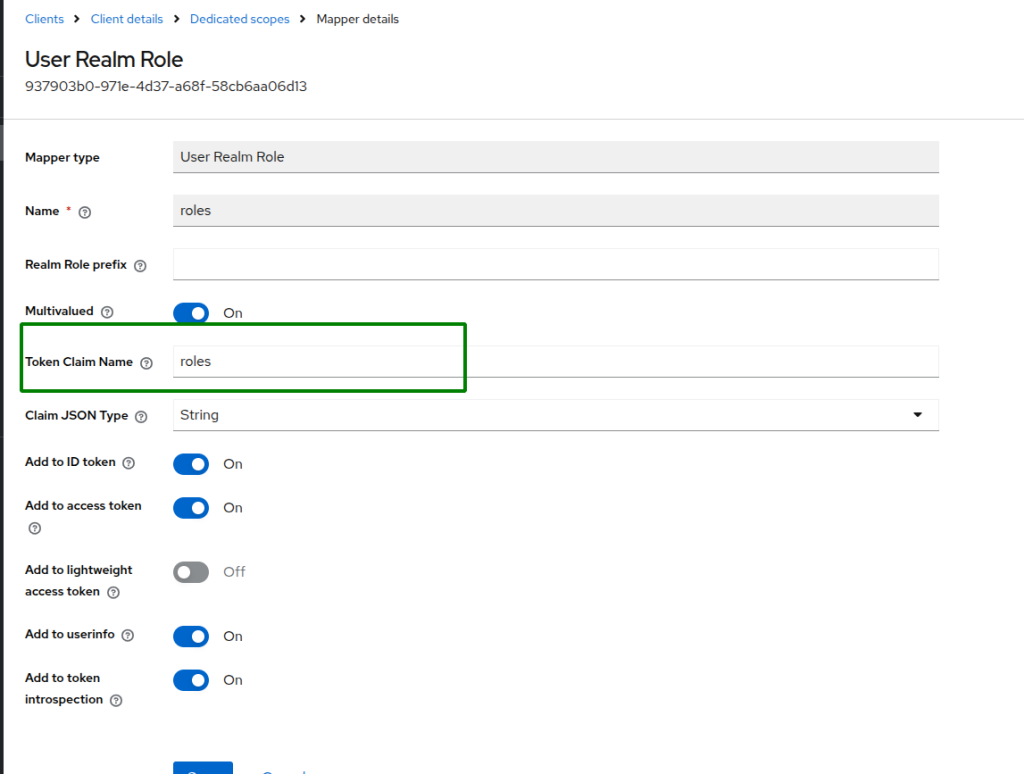
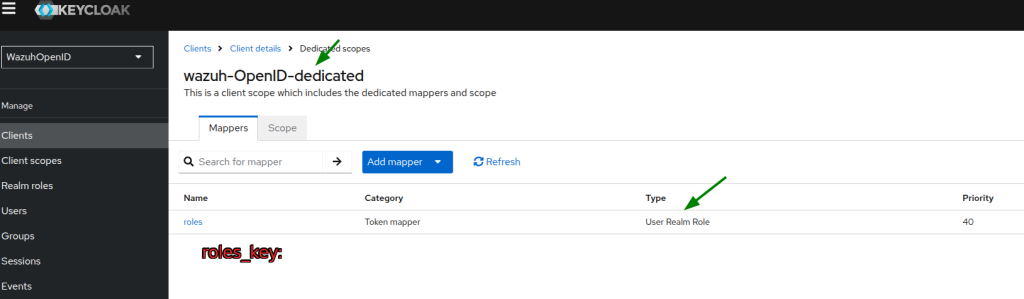
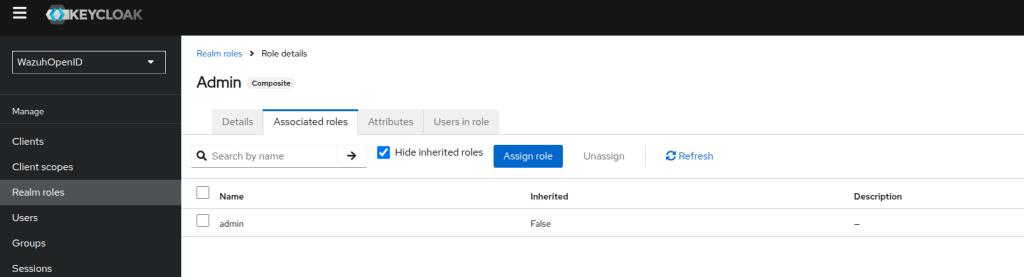
- Create a Realm roles calling it Admin and assign the admin role:
- Create a group and add admin in Role mapping:
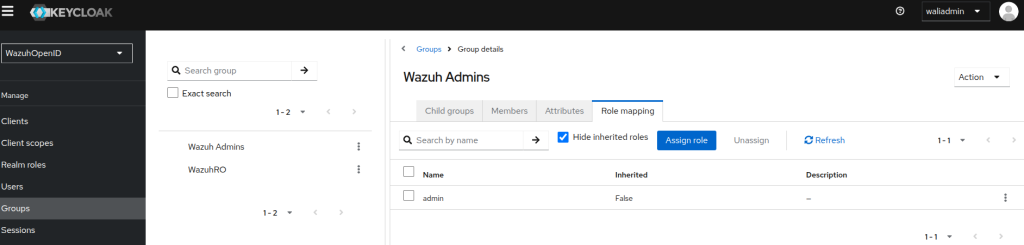
- Create a user and add it to the group:
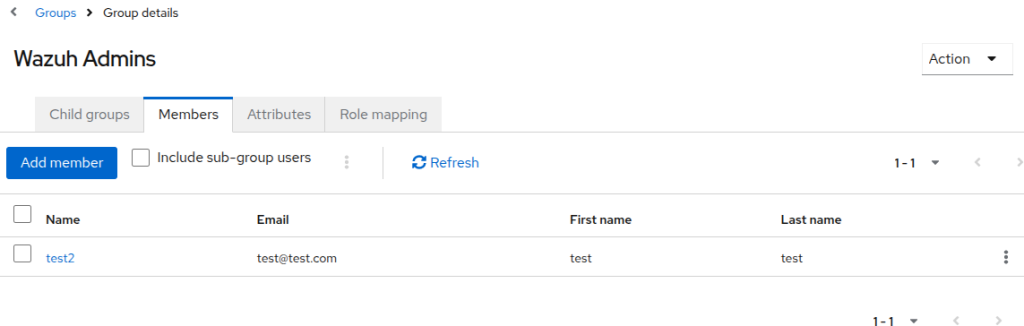
Wazuh indexer configuration:
- Configure the Wazuh indexer to use SAML by modifying
/etc/wazuh-indexer/opensearch-security/config.yml(My real name is WazuhOpenID) :
_meta:
type: "config"
config_version: 2
config:
dynamic:
authc:
basic_internal_auth_domain:
http_enabled: true
transport_enabled: true
order: 0
http_authenticator:
type: basic
challenge: false
authentication_backend:
type: intern
openid_auth_domain:
http_enabled: true
transport_enabled: true
order: 1
http_authenticator:
type: openid
challenge: false
config:
openid_connect_idp:
enable_ssl: false
verify_hostnames: false
subject_key: preferred_username
roles_key: roles
openid_connect_url: http://192.168.121.1:8080/realms/WazuhOpenID/.well-known/openid-configuration
authentication_backend:
type: noop
- Load the new security configuration
export JAVA_HOME=/usr/share/wazuh-indexer/jdk/ && bash /usr/share/wazuh-indexer/plugins/opensearch-security/tools/securityadmin.sh -f /etc/wazuh-indexer/opensearch-security/^Cnfig.yml -icl -key /etc/wazuh-indexer/certs/admin-key.pem -cert /etc/wazuh-indexer/certs/admin.pem -cacert /etc/wazuh-indexer/certs/root-ca.pem -h 192.168.121.97 -nhnv
Wazuh Dashboard configuration:
- Set the openid authentication configuration by adding below to
/etc/wazuh-dashboard/opensearch_dashboards.yml:
opensearch_security.auth.multiple_auth_enabled: true
opensearch_security.auth.type: ["basicauth","openid"]
opensearch_security.openid.connect_url: http://192.168.121.1:8080/realms/WazuhOpenID/.well-known/openid-configuration
opensearch_security.openid.base_redirect_url: https://192.168.121.97
opensearch_security.openid.client_id: wazuh-OpenID- Restart Wazuh dashboard:
systemctl restart wazuh-dashboard

336 responses to “Wazuh & Keycloak using OpenID”
how to buy stromectol – ivermectin 6mg over the counter order carbamazepine 200mg for sale
where can i buy isotretinoin – decadron medication linezolid 600 mg oral
cheap amoxil tablets – buy combivent 100mcg pill combivent 100mcg drug
zithromax buy online – tinidazole 500mg ca order bystolic 20mg sale
buy omnacortil 10mg pill – omnacortil oral progesterone without prescription
1Win Kenya is a premier online betting platform offering a seamless gambling experience for sports and casino enthusiasts., offering a seamless experience for sports betting and casino gaming. As a trusted name in Kenya, 1Win Kenya provides users with a secure platform, a vast selection of games, and flexible betting options on sports like cricket, soccer, tennis, and basketball. Registering on 1Win is simple—just visit the official website, click on “Sign Up,” and choose to register via email or social media. Once you create an account, fund it with a deposit to start betting instantly. The 1Win casino section offers a premium gaming experience with various slots, table games, and live dealer options. To enhance the excitement, new and existing players can unlock generous rewards with the 1Win bonus codes, gaining a significant advantage in their gameplay. The 1Win Bet app allows seamless sports predictions and betting on the go, ensuring uninterrupted access to all features. With a rapidly growing audience and a commitment to quality service, 1Win Kenya continues to set the standard for online gambling. Sign up today, claim your bonuses, and enjoy a thrilling betting experience with 1Win!
e3wtgt
Looking for the ultimate online casino and sports betting experience? 1Win is your go-to platform for a world-class gambling adventure, offering a massive 500% welcome bonus on your first four deposits! With over 11,000+ games, lightning-fast withdrawals, and all major payment methods, 1Win ensures a smooth and rewarding betting experience for every player. Whether you’re a casino enthusiast or a sports betting fan, 1Win provides a diverse range of services, from slots, poker, and table games to live betting, esports, and more. The 1Win casino platform features an official website with a vast selection of slots, table games, and gaming machines, allowing players to enjoy high-quality entertainment with quick registration and seamless login. One of the key highlights of 1Win is its regular poker tournaments with a guaranteed prize pool of $1000, held every two days, providing bettors with a thrilling opportunity to win big. Sports betting lovers will appreciate 1Win Sports Betting, offering competitive odds across multiple sports, including football, basketball, tennis, and more. Whether you’re betting on local or international events, 1Win ensures a premium betting experience with a user-friendly interface and real-time updates. For players in Uganda, 1Win Uganda caters specifically to Ugandan bettors by accepting Ugandan shillings (UGX) and other foreign currencies, making deposits and withdrawals easy and convenient. Unlike other sportsbooks, 1Win stands out with its generous 500% deposit bonus, setting it apart as a top-tier betting site with higher percentage bonuses than most competitors. The platform is designed for both new and experienced players, featuring a working mirror link for easy access, along with 24/7 customer support to assist users at any time. Whether you’re looking to explore casino games, participate in poker tournaments, or bet on your favorite sports teams, 1Win is your trusted online betting destination. Sign up today and claim your 500% welcome bonus to start your winning journey with 1Win – the official online casino and sportsbook!
brand acticlate – buy generic glipizide 5mg buy glucotrol pills for sale
1Win е модерна и иновативна платформа за онлайн казино и спортни залагания, която предлага богат избор от игри и атрактивни бонуси за нови и съществуващи играчи. Сайтът 1Win регистрация осигурява лесна и бърза регистрация, позволявайки на потребителите да се регистрират с един клик, чрез телефон или e-mail, както и чрез социални мрежи. Новите играчи получават щедър бонус за регистрация – 500% от първите четири депозита, което прави 1Win едно от най-добрите онлайн казина по отношение на бонуси и промоции. Освен това, 1Win предоставя удобен достъп до спортни залагания с високи коефициенти, където потребителите могат да правят залози на различни спортове като футбол, тенис, баскетбол и много други. Платформата разполага с богато казино с хиляди слотове, игри на маса, видео покер, както и вълнуващи джакпоти, които осигуряват огромни печалби. 1Win е лицензирано казино, притежаващо лиценз от Кюрасао, което гарантира сигурност и надеждност за потребителите. За допълнително удобство 1Win предлага мобилно приложение за Android и iOS, което позволява на играчите да се наслаждават на любимите си игри и спортни залагания навсякъде и по всяко време. Депозирането и тегленето на средства в 1Win Casino е лесно благодарение на множеството налични методи за плащане, включително кредитни и дебитни карти, електронни портфейли и дори криптовалути. Платформата предлага и официално работещо огледало (mirror), което позволява на потребителите да влязат в акаунта си дори при ограничения в някои държави. Освен стандартните казино игри, 1Win предлага и стрийминг на филми, което я прави уникална сред другите онлайн платформи за залагания. При проблеми с тегленето на средства, екипът за поддръжка на 1Win е на разположение денонощно, за да помогне на клиентите бързо и ефективно. За да се регистрирате в 1Win и да започнете своето приключение, просто посетете официалния сайт, създайте акаунт и направете първия си депозит, за да получите бонусите си. С атрактивните си промоции, разнообразието от казино игри и спортни залози, удобните методи за плащане и мобилното приложение, 1Win се превръща в един от водещите сайтове за онлайн залози, достъпен в България и по целия свят. Независимо дали сте любител на казино игрите или спортните залагания, 1Win предлага всичко необходимо за едно незабравимо игрово изживяване.
buy augmentin cheap – order generic augmentin buy duloxetine 40mg sale
011ra5
Kartal su kaçak tespiti Bahçelievler su kaçağı tespiti: Bahçelievler’de su kaçağını profesyonelce tespit ediyoruz. https://lacataora.com/?p=303
cys2es
pdos5f
Alibeyköy su kaçağı tespiti Erken müdahale, onarım maliyetlerini önemli ölçüde düşürür. https://orgelportal.ch/author/kacak/
ewl7dg
buy clavulanate tablets – cymbalta 40mg pill duloxetine drug
Üsküdar su kaçak tespiti Avcılar su kaçağı tespiti: Avcılar’da su kaçağını son teknolojiyle tespit ediyoruz. https://blogmags.co.uk/?p=420
su kaçağı tespiti teknik servis Başakşehir su kaçağı tespiti: Başakşehir’de su kaçağı tespitinde uzman ekibimizle yanınızdayız. http://www.pbksb-ilms.com.my/?p=5080
buy semaglutide 14mg without prescription – rybelsus 14 mg cheap cyproheptadine 4mg for sale
Your article helped me a lot, is there any more related content? Thanks!
Document translation services cover a wide range of materials, ensuring accurate and professional translations for legal, academic, technical, medical, and business purposes. Certified translation services provide official translations of important documents such as birth certificates, passports, court orders, contracts, and declarations, meeting legal and governmental requirements. Businesses often require translations for product catalogs, financial statements, user manuals, and commercial offers to expand globally. Academic and research materials, including theses, white papers, and scientific studies, are translated to facilitate knowledge sharing. Media-related documents such as magazines, newspapers, and journals require precise localization to maintain context. Surveys, business proposals, and promotional materials also benefit from expert translation. Whether translating medical records, financial reports, or technical specifications, professional translators ensure clarity, accuracy, and cultural relevance. High-quality document translation services play a crucial role in global communication, legal compliance, and international business expansion. Visit our website today to learn more about our certified document translation services and professional translation solutions!
Document translation services cover a wide range of materials, ensuring accurate and professional translations for legal, academic, technical, medical, and business purposes. Certified translation services provide official translations of important documents such as birth certificates, passports, court orders, contracts, and declarations, meeting legal and governmental requirements. Businesses often require translations for product catalogs, financial statements, user manuals, and commercial offers to expand globally. Academic and research materials, including theses, white papers, and scientific studies, are translated to facilitate knowledge sharing. Media-related documents such as magazines, newspapers, and journals require precise localization to maintain context. Surveys, business proposals, and promotional materials also benefit from expert translation. Whether translating medical records, financial reports, or technical specifications, professional translators ensure clarity, accuracy, and cultural relevance. High-quality document translation services play a crucial role in global communication, legal compliance, and international business expansion. Visit our website today to learn more about our translation of a newspaper and professional translation solutions!
2qazod
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
purchase tizanidine online – buy microzide 25 mg pills microzide 25mg tablet
jul3s3
4d5952
Discover the latest promotional codes for top betting platforms like Betwinner, Melbet, Fonbet, 1xBet, and more! Whether you’re looking for a welcome bonus, a free bet, or an exclusive registration promo code, these links provide access to updated offers for sports betting and online casinos. Find Melbet promo codes for 130% bonus, 1xBet free bet codes, and Fonbet promotions to boost your betting experience. Explore special bookmaker promotions across various countries, including Russia, Rwanda, Cameroon, and Tajikistan. Don’t miss out on the best casino and sportsbook deals available today!👉 Visit now and claim your bonus! https://actual-cosmetology.ru/pgs/promokod_fonbet_bonus.html
Discover the latest promotional codes for top betting platforms like Betwinner, Melbet, Fonbet, 1xBet, and more! Whether you’re looking for a welcome bonus, a free bet, or an exclusive registration promo code, these links provide access to updated offers for sports betting and online casinos. Find Melbet promo codes for 130% bonus, 1xBet free bet codes, and Fonbet promotions to boost your betting experience. Explore special bookmaker promotions across various countries, including Russia, Rwanda, Cameroon, and Tajikistan. Don’t miss out on the best casino and sportsbook deals available today!👉 Visit now and claim your bonus!http://ruptur.com/libs/photo/1xbet_promokod_bonus_pri_registracii.html
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me. https://accounts.binance.com/register?ref=P9L9FQKY
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/id/register?ref=GJY4VW8W
tadalafil 5mg uk – buy cialis online viagra overnight shipping
Hi, i read your blog from time to time and i own a similar one and i was just wondering if you get a lot of spam remarks? If so how do you prevent it, any plugin or anything you can advise? I get so much lately it’s driving me insane so any assistance is very much appreciated.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you. https://accounts.binance.com/hu/register?ref=FIHEGIZ8
buy sildenafil – tadalafil 10mg pills order cialis 5mg
1b4j5n
Your article helped me a lot, is there any more related content? Thanks!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Haraççı su kaçak tespiti Güler yüzlü ve hızlı bir ekip, hizmetlerinden çok memnun kaldım. https://www.alabamalighthouses.com/?p=23144
You are a very intelligent person!
om71kb
4r4k2i
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100% up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Check below list of 1Xbet signup bonuses, promotions and product reviews for sportsbook, casino, poker and games sections. To claim any of the 1Xbet welcome bonuses listed in above table we recommend using the 1Xbet bonus code at registration of your account. New customers will get a €130 exclusive bonus (International users) when registering using the 1Xbet promo code listed above. 1Xbet Sportsbook section is the main place where users hang out, with over 1000 sporting events to bet each day. There are multiple choices to go for, and the betting markets, for example for soccer matches, can even pass 300 in number, and that is available for both pre-match and live betting, which is impressive and puts it right next to the big names in the industry. Visit https://clubcoma.org/blog/1xbet_promo_code_and_bonus_2.html now and claim your exclusive bonus!
Le code promo 1xBet valide: BONUS1X200 – recevez un bonus de bienvenue de 100% jusqu’à 130€ en utilisant ce code lors de votre inscription sur le site 1xBet. Bénéficiez d’un bonus jusqu’à 130€ en freebets sur vos paris sportifs, versé selon le montant de votre premier dépôt. Avec ce code, 1xBet vous offre l’un des meilleurs bonus de bienvenue pour débuter sur leur plateforme. Obtenez jusqu’à 130€ de freebets sur les paris sportifs. Pour retirer les gains issus de votre bonus, il faudra miser 5 fois son montant sur des paris combinés avec au moins 3 matchs ayant une cote de 1.30 minimum. Pour les amateurs de casino, 1xBet propose également un bonus allant jusqu’à 1 950€ + 150 freespins + 150 freespins.
0vqhvn
bo2qb0
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
order lipitor – zestril tablet cost zestril 2.5mg
A failed bulking phase, however, means wanting worse only to threat muscle loss if you minimize to lean down. You want to outgrow
your shirts on the chest and shoulders, not your waistline.
With weights, you’ve all those self same choices, PLUS you probably can improve the weight load, which is arguably the simplest method to overload.
And yet, despite the interest in arm training, many people are
pissed off by their lack of progress. Now, talking to The Unbiased, the trainer has revealed
the precise workouts and training methods Graham used to create his
imposing new physique. Sit on the row machine and use one arm at a
time, focusing on squeezing your back muscles as you
pull the deal with towards your torso. Stephen Graham’s transformation into bare-knuckle
boxer Henry ‘Sugar’ Goodson for A Thousand Blows didn’t occur overnight.
This is as a end result of you must be coming off a
rest day before each single workout! Too often, trainees attempt to go to
the health club and kill it every workout. Restoration is
doubtless considered one of the most important components of an efficient program, and a full body exercise plan ensures you do not overtrain. Using a full
physique workout is a highly efficient way to prepare, but that’s not its solely profit.
It all is decided by your training status, your food regimen and a spotlight to
restoration, and how genetically predisposed you are to gaining muscle.
A 4-day cut up workout routine is definitely ideal for most
trainees, particularly those that could have extra household and
work pressure. Even nonetheless, many of the best weight lifters on the planet choose to work out 4 days
every week no matter having the time to go extra usually.
One of the most effective things about a 4-day cut up is its versatility to prioritize
training frequency or coaching volume, or a balance of both.
These foods provide the needed macronutrients and promote
overall health, lowering reliance on protein dietary supplements, shakes, and pre-made meals or bars.
Strive incorporating these 15 bulking foods into your food
plan to fulfill your diet needs and achieve muscle achieve.
The major aim of bodybuilders is to gain muscle and lose fats, which is often achieved through subsequent phases adopted by relaxation.
Like talked about earlier than, the aim of
this food plan is to get around 40% carbohydrates, 40% protein and 20% fat.
This means for every meal, you will attempt to eat that ratio of carbs, protein and fat.
A sample structure of a day’s meals could seem like this …
Do a couple of minutes of light cardio, followed by some joint mobility and dynamic
stretching workout routines for the muscle and joints you’re about to train.
For this purpose, keep away from falling into the perma-bulk lure, the place you end up bulking
all-year-round. As An Alternative, bring your bulk to an finish before you acquire
extra physique fat than you possibly can comfortably lose.
Do you HAVE to make use of supplements to get the most out of your bulking exercise plan?
Keep a small caloric surplus, prioritize protein intake, and focus on progressive overload in coaching.
Tracking waist measurements and physique weight helps stability muscle gain and fat
management. This structured method ensures you hit
all major muscle teams with the proper depth
and frequency. Whether you’re a beginner or an experienced lifter,
following a plan like this maximizes muscle progress while aligning with the ideas of a profitable bulking phase.
By tailoring your workouts to your body’s wants and
tracking progress persistently, you’ll set yourself up for long-term success.
Anytime you focus on two totally different goals directly (losing weight AND building
muscle), neither of these might be carried out optimally.
You can construct muscle extra rapidly when you focus on that as your major objective, eat more energy, and proceed to problem your self in your exercises.
Nonetheless, should you gradually carry extra weight, or lift the same weight for more reps, your
physique would then have a purpose to construct extra muscle.
You see, the primary training stimulus for constructing muscle is
progressive rigidity overload (source), which
essentially means steadily getting stronger over time. Even though you’re cutting and
fat loss is your objective, that doesn’t imply you should make fat loss the aim of
your weight training exercises.
More often than not, that person thinks they are consuming sufficient,
however are positively not. I drank protein shakes like I thought I was supposed to.
If you’re skinny and wish to get larger, you’ll be fighting genetics
the entire way, however don’t let that deter you. Thus began a radical redefinition of how I thought the human body worked, how muscle was
built, and where I needed to place my priorities.
Best Physiques is the #1 destination for the most effective trying
our bodies on the planet. We cowl skilled athletes, fashions and even social media stars to convey you
the very best, updated info in our profiles. It’s
a cleaner means of growing without gaining unwanted fluff.
He’s a certified conditioning coach with a level in design from York College
in Toronto, Canada. He’s personally gained 70 kilos and has over a decade of experience helping
over 10,000 skinny folks bulk up. Barbell curls and overhead
extensions are next, supersetted together.
We are going to teach you the method to clear bulk with the perfect “recipe” of food regimen and workouts.
It results in extra fats (which comes with an entire
host of health problems), poor intestine health, hormonal
imbalances, unhealthy habit formations, probably
poor micronutrition, and high irritation. It could be
ok to do a unclean bulk for a quick-maximizing
bulk period of like four weeks, however actually any longer wouldn’t be sensible.
Besides just in search of a calorie surplus, it might possibly help for many
causes to concentrate to your macronutrient (e.g., carbohydrates, fat,
and protein) consumption. That means, you’ll be able to evaluate how you did this time with how you most likely did final time.
You’ll understand how much more you have to carry
this week to verify you’re stronger than last week.
#2) Have a targeted type – if you’re doing a body weight squat incorrectly, you would possibly develop dangerous habits.
We have a MASSIVE guide on the exact number of units and
reps (it’s where the video above comes from), but you’ll
be able to observe the fundamentals here. Every day has a leg
train, push exercise, pull exercise, and some core
work.
Beginning with your palms neutral, i.e., palms dealing with inward, you should twist your dumbbell as you carry it toward your shoulder.
Supination is a perform of the biceps and performing this movement will increase muscle activation.
However, lots of the hottest biceps are also the least efficient, which helps clarify why so many people are unhappy
with their arm coaching outcomes. In the fitness center,
strong arms will make the remainder of your workout more effective.
One Other thing to mention is that the gradual increase of energy at the start of your bulk can be slowed down even more (or
sped up). So, if you’ve simply received off a cut, do a brief maintenance section, then you can start
your bulking part. Total day by day calorie expenditure
is the quantity of energy your physique
consumes every day. If you eat at your TDEE, then you will merely
maintain your weight. As you become extra superior, building muscle is
trickier and never perfectly linear. Progressive overload and
periodization have to be utilized appropriately.
With the proper food regimen and 7-9 hours of uninterrupted rest, your physique will have to adapt to the workload.
As you presumably can see from the above chart, this workout hits every body prt with various exercises for the most effective effectivity.
As a bulker, carbohydrates should encompass 40% of your total calorie
consumption … Getting adequate energy and protein to grow is the
final word challenge!
Fortuitously, I survived and thus began my love affair
with energy coaching. Check out our best rated testosterone boosters to increase power, muscle,
energy and libido. With this exercise program and
food regimen, you’ll get back on monitor and carve out a
athletic physique to be happy with. All you should do is choose a meal from the list under, Comply With this for 4-week till you’re a leaner,
stronger more muscular model of you. Gas your muscular tissues with the right vitamins and
you’ll see astonishing, accelerated growth.
This program’s major focus is to increase energy,
so “record all of your numbers,” Bruno says. Each week, attempt
to improve by adding more weight or extra reps. As your energy goes up, muscle dimension will at all
times comply with. When a muscle is broken, it units in motion a
cascade of physiological occasions that result in a very profound
anabolic response.
5-day exercise routines are overkill for most people, most of the time.
Mind you, when you’re bulking, you’ll be able to recover and profit from the additional stimulation. It’s the
proper time to pour extra effort and time into lifting weights.
Plus, it’s even more essential to maximize muscle stimulation when you’re bulking.
You’re consuming sufficient energy to gain weight,
and those extra calories can both be invested into
muscle development, stored as fat, or a combination of both.
Thus, the more muscle development you stimulate, the more of these additional calories might be invested into muscle,
leaving fewer to be saved as fat. You can stimulate muscle growth with only a few workout
routines as long as they’re done with heavy weight and they
activate as many muscle fibers as attainable.
Conditioning is amongst the most important things you can work on to enhance your lifts, endurance, and stamina.
Bettering conditioning also improves life outside of the gym.
A tried and true supplement, creatine helps with performance
and recovery.
This rep scheme is broadly considered ideal for reaching features in muscle measurement
(the scientific time period is hypertrophy) and is often employed by newbie and pro bodybuilders alike.
Not solely does this transition work as a end
result of you’re swapping out the t-shirts for sweaters, however it’s a recent way to stimulate the physique as well.
In the grand scheme of issues, you want these blocks of change.
Month after month, week after week of continuous bombardment
of the muscles with volume and intensity would wear anyone down. And the way in which to do it
effectively would require a change in pondering, and programming.
Watch Brandon DaCruz (@bigdaddydacruz) demo his program beneath.
Because you’re training every muscle group every coaching session, full physique exercise applications should be performed three
days a week.
Relying on your training goal, you’ll additionally want a calorie surplus to construct muscle or a calorie deficit to burn fats and
shed pounds. However, it’s price noting that intense 6-day exercise splits don’t work very
well if you are undereating and attempting to get ripped.
As An Alternative, this kind of high-frequency training
plan is best for bulking and lean gains than slicing.
Skinny individuals ought to comply with a year-long bulking exercise plan with a controlled caloric surplus and prioritize energy coaching utilizing compound lifts.
Aim for 1% body weight achieve per thirty days and ensure a balanced consumption of protein,
carbs, and fat. Consistency and endurance are key to achieving sustainable muscle development.
If you only do one exercise on your biceps, this traditional movement ought to be it.
The barbell curl fixes your forearms in a supinated place, producing a strong
biceps contraction. In The Meantime, the two-handed motion means you ought to use loads
of strength-building weight. I’ve spent the last three a long time testing the
effectiveness of tons of of various exercises. Throughout this lifelong journey, I truly have discovered what I believe
are the best workout routines for constructing strong, sculpted arms.
If you wish to bulk up, you’d be higher off understanding twice every week for half-hour and consuming enough
calories/protein, than figuring out 6 days per week and never eating sufficient.
To today, it’s nonetheless a big challenge for me to gain weight or construct muscle.
These tried and examined power lifts are staying in your program for week four.
As for beginners, if you’re unhappy in terms of both being skinny and
fats, then you can try a recomp plan that focuses on building a
little muscle whereas losing fats. But you won’t have the identical muscle progress
that you would on a bulk. Each 6-12 weeks (depends on you), take a rest week or a deload week where you
do the same workouts with practically half or two thirds of the load.
You will want this rest or deload week once in a while to permit your physique to totally recuperate.
You can’t continually progress for months on finish with out ending up overtraining.
The deadlift is probably certainly one of the handiest workout
routines for building general energy and muscle constructing.
If you scale back the intensity of your coaching, but
proceed to eat the identical number of calories
that fueled your bulk, it may result in unintended weight acquire, says Machowsky.
He says you can fix that by reverting to the variety of calories you had been consuming
previous to the bulk. Except you’re a competitive athlete, there’s probably not a must-adhere to timeline,
says Machowsky. “Most training phases final six to 12 weeks, although there’s no onerous and fast rule about how long you should spend bulking,” he says.
Look for tendencies over weeks quite than day by day fluctuations.
By No Means wonder the place you must put your limited time, power,
and energy. Observe your progress, monitor your calories,
and track your workouts.
Feel free to surf to my web-site: what Do prescribed steroids do [ssecretcoslab.Com]
Pendik su kaçak tespiti Ekip çok deneyimli ve kibar, su kaçağı sorunumu hemen anladılar. https://direc.ircg.ir/author/kacak/
The 3 Best Steroids for Beginners
When starting with steroids, prioritize safety and effectiveness.
– **Testosterone Enanthate**: A popular choice for muscle growth and strength.
– **Methandrostenolone (Dianabol)**: Known for its effectiveness in building lean muscle.
– **Deca-Durabolin**: Provides sustained benefits with minimal side effects.
3 Steroids to Avoid
These options are riskier and should be avoided by beginners:
– **Anadrol**: Risky due to severe side effects and legal concerns.
– **Trenbolone Acetate**: Potentially harmful with misuse.
– **Winstrol**: Not ideal for muscle growth.
Best Steroids for Beginners (Plus 3 to Avoid)
For anyone new to steroid usage, it’s essential to start with mild and relatively safe options that have been tested extensively in the bodybuilding community. While there are many steroids available, not all are suitable for beginners due to their potential for side effects or legal status.
The Top 3 Steroids for Beginners
1. **Testosterone**: Testosterone is one of the most fundamental anabolic steroids and is often considered a starting point for many athletes. It helps in building muscle mass, improving strength, and enhancing overall performance. However, it’s important to note that using testosterone alone can lead to significant side effects if not used responsibly.
2. **Testosterone Replacement Therapy (TRT)**: TRT is often recommended for individuals experiencing age-related declines in testosterone levels. It’s a controlled form of testosterone that can help maintain muscle mass and overall health, especially in older users. TRT should be used under medical supervision to avoid adverse effects.
3. **Dianabol**: Dianabol is one of the most well-known steroids among beginners due to its ability to promote rapid muscle growth and strength gains. It’s often used in bulking phases and is generally well-tolerated by new users when taken at moderate doses.
Steroids to Avoid
1. **Anavar**: While Anavar is considered a mild steroid, it’s also one of the most frequently misunderstood. Its low androgenic nature makes it less effective for muscle growth compared to other steroids like Dianabol or Testosterone. Additionally, it can lead to side effects such as acne, hair loss, and liver toxicity if used improperly.
2. **Winstrol**: Winstrol is another steroid that’s often recommended to users looking for a cutting phase, but it’s not ideal for beginners due to its high risk of side effects, including liver damage and testicular atrophy.
3. **Trenbolone**: Trenbolone is a powerful steroid that’s highly popular among advanced bodybuilders, but it’s also one of the most dangerous options for beginners. It can cause severe side effects such as cardiovascular issues and psychological instability.
Legal Steroid Alternatives That Work
If you’re looking for safer alternatives to anabolic steroids, consider these legal options:
Sustanon 250: A potent steroid that’s widely used in the bodybuilding community. It provides sustained release of testosterone and is often preferred by users who want consistent results without the need for frequent injections.
Anavar: While Anavar can be problematic for some users, it remains one of the most popular legal alternatives due to its effectiveness in promoting muscle growth and fat loss without causing significant side effects in moderate doses.
The Best Stack for Beginners
For those looking to maximize their results while minimizing risks, consider stacking these steroids:
Dianabol + Testosterone: This classic combination is ideal for beginners as it provides a good balance of muscle growth and strength without being too harsh on the body.
Side Effects
While steroids can offer significant benefits, they also come with potential side effects. Common risks include:
– **Testosterone Imbalance**: Using steroids like Testosterone or TRT can disrupt your body’s natural hormone production, leading to issues like testicular atrophy and infertility.
– **Liver Damage**: Many steroids are metabolized in the liver, which can lead to damage if not taken in moderation or without proper guidance.
– **Acne and Skin Issues**: Steroids can cause skin problems such as acne, which may persist even after use is discontinued.
Summary
Starting with steroids can be a rewarding experience, but it’s crucial to choose the right products and use them responsibly. Always consult with a medical professional before beginning any steroid regimen, especially TRT or high-dose cycles. Avoid Anavar, Winstrol, and Trenbolone until you have more experience and understanding of how they affect your body.
My site; Arnold schwarzenegger steroid – http://ssecretcoslab.com/bbs/board.php?bo_table=free&wr_id=122320 –
order cenforce 100mg sale – order metformin 500mg for sale glycomet 500mg drug
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
أجهزة سحبة السيجارة الحديثة تعتمد على تكنولوجيا متطورة تمنح المستخدم تجربة تدخين محسنة بدون الروائح الكريهة أو الدخان الضار، مما يجعلها حلاً عمليًا للراغبين في الإقلاع عن التدخين التقليدي.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
أجهزة سحبات السيجارة القابلة للشحن تأتي بتصميم أنيق وسهل الاستخدام، تعمل بتقنية البخار بدلاً من الاحتراق، مما يجعلها خيارًا أكثر أمانًا وصديقًا للبيئة مقارنة بالسجائر التقليدية.
أجهزة سحبة السيجارة الحديثة تعتمد على تكنولوجيا متطورة تمنح المستخدم تجربة تدخين محسنة بدون الروائح الكريهة أو الدخان الضار، مما يجعلها حلاً عمليًا للراغبين في الإقلاع عن التدخين التقليدي.
buy prilosec without prescription – omeprazole over the counter tenormin over the counter
6ki6r6
I was very pleased to find this web-site.I wanted to thanks for your time for this wonderful read!! I definitely enjoying every little bit of it and I have you bookmarked to check out new stuff you blog post.
Outstanding post, I conceive blog owners should acquire a lot from this blog its rattling user pleasant.
lponVXGP tvvLauxT ogxlqnno
Melbet – популярный букмекер, предлагающий отличные бонусы для новых игроков. При регистрации можно получить фрибет, введя специальный промокод Melbet. Это позволяет делать ставки без вложений, увеличивая шансы на выигрыш. Промокод melbet_promokod_na_fribet_pri_registratsii активирует бонусные средства, которые можно использовать на спортивные события и казино. Melbet радует пользователей высокими коэффициентами, широкой линией ставок и удобными способами вывода средств. Не упустите шанс начать игру с бонусом – регистрируйтесь и получайте фрибет!
uqpp25
Nonetheless, full-body workouts are notably well-suited to beginners, who typically don’t need as many sets as intermediate and superior trainees (such as bodybuilders) to stimulate progress. Compound workouts are those who work on a quantity of muscle groups without delay, spanning across a number of joints. Squats, bench press, rows, shoulder press, and pull-ups are nice examples of these. As A End Result Of you’ll have more muscle fibers working with every rep you carry out, you have more whole power behind you.
The leg extension and sissy squat mathematically work the quads much more than a squat. In the same method, resistance must be applied in a straight line. This is why, in a bench press for instance, the elbow must be immediately under the wrist in order that drive is instantly utilized. If your type isn’t excellent using the weight you chose, pick a lighter weight. You’ll get there quicker when you practice doing the movements the right method. You must also get within the habit of stretching the target muscle tissue before truly focusing on them. This program will goal principally each single muscle you’ve in your physique, so getting those muscle loose is essential.
You don’t must eat carbohydrates immediately after a exercise to construct muscle. A very low carb consumption just like the ketogenic diet works nicely for maintaining muscle when weight-reduction plan to get lean but might restrict muscle growth during the off-season. The larger your calorie wants, the more room you have for carbs. If you could have a physically demanding job and require three,500 energy to take care of your body weight, you’ll be consuming plenty extra carbs than someone with the identical physique weight and a desk job. As Quickly As you may have assigned calories to protein (1.6–2.2 g/kg/day) and fats (0.5–1.5 g/kg/day), simply eat the relaxation of your daily energy from carbs. Consuming that quantity of protein earlier than and after working out can additionally be a good idea. Eating or ingesting protein 1–2 hours pre-exercise and within 1–2 hours post-exercise ensures your muscle cells have the building supplies they want.
Nevertheless, the days of the week that you practice aren’t set in stone. If you can’t make it to the gym on Monday, Wednesday and Friday, you can all the time prepare on Tuesday, Thursday and Saturday. You’ll find a hyperlink to the three day full physique workout PDF on the backside of this page.
Protein is the constructing block of your body, and if you don’t eat enough of it, you’ll have trouble building muscle. All the upper-body workout routines I mentioned above work your biceps and your triceps very effectively. For instance, studies present that lat pulldowns make your biceps grow simply as a lot as dedicated biceps curls. All exercises ought to use a weight that tires you inside 8-12 reps. Complete three sets of every train and purpose to relaxation around 2-3 minutes between workout routines. As science has progressed we’ve realized that until you’re hitting the gym most days of the week, whole-body coaching is the best choice. In this guide, we inform you everything you have to learn about training for the older man.
Partials make a superb finisher if you can’t do extra full reps but want to absolutely exhaust the muscle. I recommend you train to failure some of the time however not all of the time. That means, you get the potential advantages however keep away from burnout. Do too many, and you may even enter overtraining territory. You’re doing greater than your physique can handle, and your results start to endure. The more typically this process happens, the bigger your muscles will develop. Lifting weights helps to set off greater release of testosterone by slapping your mind across the face, forcing it to hurry up hormone manufacturing.
They provide too little of a quantity of amino acids to stimulate muscle protein synthesis successfully. For example, in a bicep curl, partial reps might contain only lifting the weight midway up and decreasing it back down somewhat than curling it all the way in which up. Failure is the point at which you can no longer complete another repetition of a particular set with correct form and method. Strive doing a set of barbell curls with a weight which you estimate you are able to do 30 reps. Now curl that bar to failure. Even if you’re extremely motivated and love being within the gym, coaching every day can lead to burnout and grind your progress to a halt. The downside of coaching a muscle group solely as soon as weekly is that your coaching high quality may endure towards the tip of the exercise. Coaching every muscle group frequently is often thought of the easiest way to maintain MPS elevated and stimulate muscle growth.
This is until I build a library of my own with visible demos of workout routines. For instance, using the identical exercise instance as for the negative sets, imagine you might be doing biceps barbell curls with 50lbs. This weight is ideal so that you just can properly perform 5 or 6 repetitions.
Avoid using momentum or swinging the load up utilizing your hips, as that will take away work from the supposed working muscles. That means it’s worked to some degree in rowing workout routines just like the bent-over row, but you possibly can goal it even additional with workout routines like the reverse dumbbell fly, pictured above. The overhead press is as old as the barbell itself, and is probably the most effective shoulder train of all. I counsel keeping your rest intervals between two and three minutes.
As An Alternative, contract your glutes, brace your stomach wall to achieve stability, and use a full range of motion from beneath your chin as much as straight arms. However, for hypertrophy training, you wish to carry out the squat in a controlled manner, preserving tension in your muscle tissue all through the set. If establishing a great mind-muscle connection means less weight on the bar, don’t hesitate to lower the load. Keep In Mind, your muscle tissue develop if you relaxation them in the course of the 24–48 hours following your training session, not whereas you’re truly lifting. As you gain coaching expertise, taking two to a few minutes to recover between sets lets you raise heavier and do extra reps for possibly slightly higher features over time.
Sarcoplasmic hypertrophy is a brief lived dimension increase due to a higher quantity of sarcoplasm in the muscle tissue. This occurs when you get a big buildup of byproducts after a weight lifting exercise and have an increased move of blood into that particular muscle tissue. Mainly, it’s your ‘muscle pump.’ You see this dimension gain shortly upon train, but it also tends to go away just about as rapidly because it came.
Simply stick to those basics and visualize yourself making positive aspects. And if you concentrate on it, you’re also working the entire back-side of your body. This is a component that some could neglect because back and hamstrings aren’t as seen to us (or to the mirror!). But if you’d like that 3D bodybuilder look, you must have a large back and hamstring. You’ll follow that up with isolation workouts and doing a drop set on the final set of each. One Other quick notice is that you’ll be doing pyramid sets, which means you’ll go up in weight every set.
This exercise plan kick-starts the journey to a more ripped, jacked physique that’s as aesthetic as it is athletic. During this intense week of training you’ll be hitting the weights room onerous as you push your physique to its limits with muscle building, strength-building energy training. If you may have been following our 4 day cut up Intermediate workout plan for mass and gained some muscle mass. This superior 4-day full-body workout aims that can help you achieve the utmost amount of muscle whereas staying lean and increasing your power.
The movements that work your again and biceps are all pulling movements. This is the ideal setup in relation to constructing mass because you’ll be able to break down and concentrate on complimenting muscle teams multi functional exercise. Even a modest amount of muscle achieve mixed with low physique fat levels makes an enormous visible impact. For example, whereas 3-day splits can be very efficient, they generally go away you time to train a muscle group or movement with 3-4 workouts per week. This isn’t necessarily dangerous, however it means you’ve much less of a chance to be specific about your train selection. A superset means performing two exercises back-to-back with out relaxation in between. The workout routines can target the same muscle group or totally different muscle groups.
However if you’re in a position to do that transfer, it’s nice for including dimension to the delts. That mentioned, we suggest you switch the order of squats each week—in week 2, for example, do regular squats first, and in week three, start off with Smith machine squats. This will guarantee a well-balanced leg protocol via the course of 4 weeks. At a glance this will appear counterproductive for building muscle.
However, Josh cautioned that though coaching to failure may lead to extra development whenever you have a glance at simply 1 set in isolation, it additionally creates extra fatigue. Brad then defined how folks thinking about learning tips on how to build muscle in cussed groups could strategically use larger volumes to drive progress. The next piece of the tips on how to build muscle puzzle is quantity and frequency.
If you are uninterested in using different splits or not seeing outcomes, we’re fairly certain it will get you the results you’re seeking. This intermediate exercise plan is a four day cut up workout routine. That is, you exercise 2 days followed by relaxation and understanding one other 2 days and another 2 days of rest. You ought to give your muscle tissue sufficient time to recuperate from both exercise days and stimulate correct muscle growth. Full-body workouts could be made to work for beginner, intermediate and superior trainees alike.
In this text, I’ll information you thru everything you want to know to start building muscle previous the age of fifty. Contrary to popular perception, age is not an impediment to gaining muscle. Power training is both effective and safe for older adults. Full A1 and A2 again to again with no relaxation before giving yourself a 2-3 minute relaxation interval. Once you’ve accomplished ll 3 units you progress onto B1 and B2 and do the identical.
I may also be including some depth strategies like drop sets, restricted relaxation units, and some other strategies of my very own design. On every of these actions, you need to concentrate on the muscular tissues that are contracting. You can’t construct muscle mass when you aren’t offering the best nutrition for your physique. You need to assist your daily necessities, and supply surplus of protein so your physique can bodily make new cells.
To lose body fats, you must eat fewer calories than you burn. Without a calorie deficit, it does not matter the way you prepare or what your diet looks like. Sooner or later, you’ll need to go on a cutting food plan to make your muscles seen and show the fruits of your labors in the fitness center. Going for two.2 g/kg/day guarantees you get enough to help muscle progress and restore in the course of the bulking season. A good bodybuilding food plan is the same as a healthy, balanced food regimen for anyone else, solely emphasizing muscle-building nutrients like protein. Pre-exhaustion training can successfully improve a workout’s general intensity and volume, and you can use it during a high-volume training cycle.
The barbell squat just isn’t solely a competitive lift in powerlifting and the most well-liked train to enhance athletic performance. It’s additionally one of the best leg workouts for building muscle in your lower body and a staple of many bodybuilding applications. An wonderful alternative for anybody, whether or not you’re just starting out or you’re a seasoned lifter, is a full-body exercise plan. This technique works all your major muscle teams in each session, and sure, it’s a powerhouse method for building each energy and muscle. Say your program calls for 3 sets of 10 to 12 reps on the dumbbell bench press. If you schlep to the gym 4 times every week, decide up a random pair of dumbbells, and do a couple of units of random reps for a handful of workout routines, your results aren’t going to last. One of the small print that matters most when trying to add muscle mass is the number of repetitions you do for each train in your exercise plan.
Adding variability to your exercises prevents your body from getting accustomed to them. Thus, stopping you from hitting a plateau and boosting muscle gain. Adverse units require both a spotter or assisted equipment.
Now, though this sounds like a bad idea, in every exercise, you’re only doing a few sets per muscle. Some imagine these exercises now turn into a waste of time and would be better off moved to another exercise day when your muscle has recovered. And on the end, I’ll add a bonus factor, time effectivity, to see which exercise cut up will get you probably the most positive aspects within the least time. Maintaining a workout log of how a lot you lift is the best way to track your progress over time. It removes the guesswork and allows you to focus in your training as a substitute of attempting to recollect what you probably did the final exercise. They significantly influence your capability to construct muscle and get well from training. Sometimes issues get in the way, and most probably, it will happen again.
Make positive you might have no much less than 6 months worth of solid training expertise before you strive a excessive frequency split like this. It’s all about thick, vascular muscle mass and bar-bending, brute-force energy. This kind of exercise will permit your body to get well and you could find that you’re stronger when you begin back in your regular routine.
References:
https://smart-holst-3.technetbloggers.de/beginner-steroid-cycles-novice-oral-only-low-dosage-steroid-stacks
jztbk9
Les codes promo 1xBet valide permettent aux parieurs d’obtenir des bonus exclusifs, des offres spéciales et des récompenses sur la plateforme. Disponibles dans plusieurs pays comme la Côte d’Ivoire, le Sénégal, le Cameroun, l’Algérie et le Maroc, ils sont utilisés lors de l’inscription ou des dépôts pour maximiser les gains. Certains codes sont disponibles gratuitement via Telegram ou promotions spéciales. Pour profiter des avantages, il suffit d’entrer un code valide et suivre les conditions d’utilisation.
buy generic medrol for sale – purchase triamcinolone online order triamcinolone 10mg pill
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100% up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Check below list of 1Xbet signup bonuses, promotions and product reviews for sportsbook, casino, poker and games sections. To claim any of the 1Xbet welcome bonuses listed in above table we recommend using the 1Xbet bonus code at registration of your account. New customers will get a €130 exclusive bonus (International users) when registering using the 1Xbet promo code listed above. 1Xbet Sportsbook section is the main place where users hang out, with over 1000 sporting events to bet each day. There are multiple choices to go for, and the betting markets, for example for soccer matches, can even pass 300 in number, and that is available for both pre-match and live betting, which is impressive and puts it right next to the big names in the industry.
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100% up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Check below list of 1Xbet signup bonuses, promotions and product reviews for sportsbook, casino, poker and games sections. To claim any of the 1Xbet welcome bonuses listed in above table we recommend using the 1Xbet bonus code at registration of your account. New customers will get a €130 exclusive bonus (International users) when registering using the 1Xbet promo code listed above. 1Xbet Sportsbook section is the main place where users hang out, with over 1000 sporting events to bet each day. There are multiple choices to go for, and the betting markets, for example for soccer matches, can even pass 300 in number, and that is available for both pre-match and live betting, which is impressive and puts it right next to the big names in the industry.
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100% up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Check below list of 1Xbet signup bonuses, promotions and product reviews for sportsbook, casino, poker and games sections. To claim any of the 1Xbet welcome bonuses listed in above table we recommend using the 1Xbet bonus code at registration of your account. New customers will get a €130 exclusive bonus (International users) when registering using the 1Xbet promo code listed above. 1Xbet Sportsbook section is the main place where users hang out, with over 1000 sporting events to bet each day. There are multiple choices to go for, and the betting markets, for example for soccer matches, can even pass 300 in number, and that is available for both pre-match and live betting, which is impressive and puts it right next to the big names in the industry.
Use 1XBET promo code: 1X200NEW for VIP bonus up to €1950 + 150 free spins on casino and 100% up to €130 to bet on sports. Register on the 1xbet platform and get a chance to earn even more Rupees using bonus offers and special bonus code from 1xbet. Make sports bets, virtual sports or play at the casino. Join 1Xbet and claim your welcome bonus using the latest 1Xbet promo codes. Check below list of 1Xbet signup bonuses, promotions and product reviews for sportsbook, casino, poker and games sections. To claim any of the 1Xbet welcome bonuses listed in above table we recommend using the 1Xbet bonus code at registration of your account. New customers will get a €130 exclusive bonus (International users) when registering using the 1Xbet promo code listed above. 1Xbet Sportsbook section is the main place where users hang out, with over 1000 sporting events to bet each day. There are multiple choices to go for, and the betting markets, for example for soccer matches, can even pass 300 in number, and that is available for both pre-match and live betting, which is impressive and puts it right next to the big names in the industry.
e652ry
clarinex price – clarinex 5mg ca order priligy pills
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Love this blog! The content is always so relevant and insightful, keep up the great work!
Thanx for the effort, keep up the good work Great work, I am going to start a small Blog Engine course work using your site I hope you enjoy blogging with the popular BlogEngine.net.Thethoughts you express are really awesome. Hope you will right some more posts.
Nice Post! Very Very Nice, Thank You
Have A Good Day, Very Positif Post !
cytotec us – buy cytotec pills for sale diltiazem 180mg oral
Good Post Brother! Nice Nice
také jsem si vás poznamenal, abych se podíval na nové věci na vašem blogu.|Hej! Vadilo by vám, kdybych sdílel váš blog s mým facebookem.
Good Post Bro! Nice Nice, Waiting Your Next Post!
3o142y
Simply wanna say that this is handy, Thanks for taking your time to write this.
I don’t normally comment but I gotta say thankyou for the post on this great one : D.
ppi2xd
A code promo 1xBet est un moyen populaire pour les parieurs d’obtenir des bonus exclusifs sur la plateforme de paris en ligne 1xBet. Ces codes promotionnels offrent divers avantages tels que des bonus de dépôt, des paris gratuits, et des réductions spéciales pour les nouveaux joueurs ainsi que les utilisateurs réguliers.meilleur code promo 1xbet rdc
Good Post ! Have A Nice Day !!!
Great post! Loved the insights, keep it up!
Awesome read! Definitely looking forward to more posts like this!
Really enjoyed this! Thanks for sharing such valuable content!
Great content as always! Keep it coming!
70918248
References:
is Dianabol a steroid [https://meetdatingpartners.com/@dinoliles15839]
Great post! Love the insights, really made me think. Keep it up!
Awesome read! Very informative and well-written. Looking forward to more!
Really enjoyed this post! Thanks for sharing such valuable info!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Hamidiye su kaçak tespiti Sultanbeyli’deki evimizde su kaçağı vardı, çok kısa sürede çözüldü. Harika bir ekip. https://ablaze.media//author/kacak/
Bahçelievler su kaçağı tespiti Gelişmiş elektronik kaçak tespiti, araştırmayı minimum düzeyde invaziv yapar. http://propin.ai/uskudar-tesisatci-tikali-lavabo-acma/
izxq49
Esatpaşa su kaçak tespiti Profesyonelce çalışıp su kaçağını nokta atışıyla buldular. https://blogmags.co.uk/?p=420
70918248
References:
boldenone steroids (https://jamdiggy.com/aracelisgowins)
Thank you for the post, i will wait your next post!
Wonderful website. Lots of helpful info here. I am sending it to a few buddies ans additionally sharing in delicious. And naturally, thanks for your sweat!
Thank you! waiting your next post!
When I originally commented I clicked the -Notify me when new comments are added- checkbox and now each time a comment is added I get four emails with the same comment. Is there any way you can remove me from that service? Thanks!
buy zovirax 400mg sale – buy acyclovir 400mg rosuvastatin 20mg generic
70918248
References:
what is tren steroid (http://git.jfbrother.com/brainmyg754636)
Thank you for your information!
Your article helped me a lot, is there any more related content? Thanks!
Really enjoyed this! Your perspective is refreshing and thought-provoking. Keep it up!
Your perspective is refreshing and thought-provoking. Keep it up!
order domperidone 10mg sale – buy motilium flexeril tablet
It’s a light steroid, usually used by girls because of its low unwanted facet effects and its ability to advertise lean muscle progress and fat loss. Let’s explore additional what this pharmaceutical marvel can supply for people of the finer sex. Anavar has become well-known for fitness lovers in search of to sharpen their slicing cycles, mainly due to its well-documented ability to promote fat loss while maintaining hard-earned muscle. First and foremost, the drug’s impact on lipid metabolism plays an important function in its capacity to enhance fat loss. By ramping up the body’s metabolic fee, Anavar enables users to burn off extra energy than they’d sometimes do whereas, on the same time, facilitating the retention of lean muscle tissue. Shedding saved fats and preserving muscle mass creates a synergistic impact that helps outline and shape the physique during a slicing cycle.
Some additionally point out the beginning of muscle definition, particularly in their shoulders, arms, and again. In my journey of studying about Anavar’s results after 2 weeks, I have come across a quantity of individual experiences – each optimistic and cautionary. Micronutrients, similar to vitamins and minerals, are crucial for general well being and optimal muscle perform. One of the primary advantages of Anavar is its capability to help customers acquire power without placing on an extreme quantity of mass.
The compound is soft and due to this fact positively is not the most effective by method of rising muscle mass, but as an alternative, this product is unquestionably in the top of safest steroids. This subreddit is for questions and dialogue associated to testosterone alternative remedy and testosterone. It additionally focuses on way of life activities like train and diet for raising testosterone levels naturally or anything related to testosterone the substance. In conclusion, Anavar is usually a useful tool in the bodybuilding journey for girls, supplied it’s used responsibly and carefully. Success in bodybuilding comes from consistency, patience, prudent selections, and above all—respect in your personal body. Use Anavar properly, placing your well being first, and you might find it to be a helpful companion in your way to achieving your bodybuilding targets.
Furthermore, the supplement promotes the event of lean muscle mass, allowing ladies to sculpt their bodies and achieve a extra defined physique with out excessive bulking. Anavar, a gentle yet efficient anabolic steroid, is widely employed within the health and bodybuilding industry to enhance physique and performance. Its outcomes, nevertheless, can differ significantly based on the period of usage, dosage, and the user’s traits, like gender. In the table below, we compare individuals’ progress from 2 to eight weeks of Anavar usage, highlighting the unique transformations observable in both male and female customers. The noticeable enhancement in muscle definition and vascularity provides to the athletic and toned look. Reviewing a collection of before and after footage for females displays an equally impressive transformation.
In our experience, many females who take Anavar experience no virilization results. Nonetheless, there are exceptions to each rule, as some ladies abuse Anavar, taking excessive doses for extreme periods of time, which may actually result in masculinization. We do not endorse the use of anabolic steroids; nevertheless, we understand that many women and girls are using these substances and need right guidance. However, you will need to observe, people ought to adhere to the recommended dosage and use the complement responsibly to count on these sorts of transformations. After all, like any other fitness supplement, Oxandrolone is best when paired with a balanced food plan and a rigorous workout routine. Understanding the correct way to take Oxandrolone tablets is significant for efficient results and sustaining security.
Please discover beneath an inventory with an approximate value for different compounds. In addition to muscle modifications, this mixture creates an environment for environment friendly fats loss. Both compounds work together to promote a lean and well-defined body composition.
Nevertheless, you will want to notice that the severity and incidence of unwanted effects can differ from person to person. When considering the dosage and cycle info for Anavar (Oxandrolone) during a four-week cycle, it’s essential to prioritize security and cling to accountable usage. It is crucial to consult with a medical professional or a certified healthcare provider before starting any steroid cycle. They can present customized guidance based in your individual well being status, goals, and any potential contraindications. In abstract, a 4-week Anavar cycle might show beneficial for feminine athletes looking for to amplify their efficiency inside a comparatively brief period.
The addition of Anadrol will shut down testosterone ranges further, so users can continue operating Nolvadex post-cycle, combined with Clomid and hCG, for a quicker recovery. Thus, users won’t experience any extra water retention or gynecomastia in comparison with a testosterone-only cycle. Hair loss on the scalp, enlarged prostate, and acne vulgaris are common side effects we see with testosterone/trenbolone stacks. Typically, when you skilled acne during puberty or presently have a receding hairline, this cycle might irritate either or both. Trenbolone has diuretic properties, therefore why additionally it is used as a cutting agent.
This timespan, combined with a low dosage, can help you observe how your body responds to Oxandrolone, and nonetheless produce positive adjustments in muscle tone and energy. It’s crucial to dedicate ample time for restoration after the cycle—allow your body to relaxation and recuperate from the effects of the drug. Oxandrolone, commonly known as Anavar, has turn into increasingly well-liked among feminine bodybuilders for a quantity of causes.
Nevertheless, Clenbuterol should not be abused, with some users having been hospitalized after taking very excessive doses. One man’s coronary heart rate rose to 254 beats per minute (5), after an unintended 10-fold overdose. Ladies at our clinic who have taken it are usually thrilled with the results. In this text, we’ll discuss the best steroids for girls and the ones they need to avoid in any respect prices. As in every side of health, informed decisions and a holistic approach should be the guiding principles.
Anavar is valued for its ability to reinforce energy, promote lean muscle progress, and enhance athletic performance. Compared to different anabolic steroids, it has milder androgenic effects, making it appropriate for each men and women. It works by increasing nitrogen retention in muscles, which aids protein synthesis and helps muscle growth.
References:
elliott hulse steroids [https://ciitiijobs.in/employer/how-much-is-anavar/]
Dave Crosland, the founding father of Crosland’s Harm Reduction Companies, has also found testosterone and estrogen levels to be deficient in females post-Anavar (24). With Anavar’s brief half-life of 9.4–10.4 hours, we discover it increasingly effective to split up doses all through the day, maintaining excessive concentrations of oxandrolone within the body. Anavar is a C17-alpha-alkylated oral steroid, that means the compound shall be fully active after bypassing the liver. Nonetheless, not like other oral steroids, Anavar isn’t significantly hepatotoxic. This is as a outcome of the kidneys, and never the liver, are primarily responsible for metabolizing Anavar. Therefore, a portion of oxandrolone will escape liver metabolism. However, we find this to be a smaller proportion in comparison with other C17-aa steroids.
First and foremost, it’s essential to emphasise the significance of purchasing Anavar from legitimate and reputable sources. The market is unfortunately flooded with counterfeit or substandard products, usually posing significant risks to health. Opting for legal alternatives is a prudent method, as these merchandise undergo stringent quality control and cling to safety standards. Oxandrolone is renowned for its capacity to contribute to numerous health targets, together with muscle definition, strength enchancment, enhanced endurance, and fats loss. This table supplies a comparability of Anavar’s results on these key elements, supplying you with an outline of the potential benefits it provides. Please note that particular person outcomes could range, and it’s crucial to make use of Anavar responsibly and underneath skilled steerage. Administering Anavar a day is a typical follow among users, noted for hanging a balance between maximizing results and managing potential unwanted effects.
For a relatively quick oral AAS cycle, the menstrual cycle, and female hormones will normalize and return back to homeostasis without a PCT. We recommend ensuring LDL, blood stress and kidney/liver perform is managed appropriately when biking oral AAS. From an “PED” viewpoint, Oxandrolone is used to extend athletic performance in some ways, and people advantages are listed above on this FAQ. PrecisionAnabolics is extremely proud of the standard we provide in our Anavar on the market, and are equally as proud as how competitively priced we’re for each the 25mg tables and 10mg tablets respectively.
Do you find yourself battling losing fat, gaining lots of lean muscle, or having low testosterone levels? Then Hi-Tech Prescription Drugs Anavar is the complement resolution to buy for you! These elevated levels of free testosterone lead to extra muscle development and so forth. This course of additionally inhibits glucocorticoid hormones, meaning catabolic hormones, similar to cortisol, are controlled.
They are recognized for their rigorous testing procedures and dedication to high quality. Navigating the world of anabolic steroids may be daunting, particularly in terms of purchasing them safely. Anavar, a preferred selection among health enthusiasts and athletes, isn’t any exception. Understanding the nuances of Anavar cycles is paramount for reaching desired results whereas mitigating potential dangers. Here, we outline recommended cycles for each beginners and experienced users, considering factors corresponding to gender and fitness goals. Hi-Tech Prescribed Drugs’ Anavar contains a strong formula that begins with 4-Androstenolone (4-Andro).
Bodybuilders can even purchase Winstrol tablets on the market on-line during their off-season or if they are recovering from high interval depth coaching (HIIT) muscle injuries. To convey side effects to zero, seek the advice of a specialist, ask him to calculate the exact dosage that received’t harm your health. All of our steroids are made with the very best standard of high quality and ethics. You can buy real Anavar from us with fast USA delivery, safe funds, and lab-tested authenticity. Select our Anavar 10mg 100 tabs – trusted by athletes nationwide, backed by quick delivery and secure checkout. Circulating testosterone as the hormonal basis of sex variations in athletic performance. Anabolic-androgenic steroid increases working endurance in rats.
Buying 1 kg of uncooked oxandrolone powder from bulk sellers in China and making dosage adjustments is another option. However, this could potentially lead to authorized points, as you may be misidentified as a drug cartel member, resulting in a protracted legal battle to show your innocence. One Other deceit aimed at Anavar customers comes from manufacturers who employ the names of well-known steroids of their product labels, solely to sell frequent supplements. Have misplaced money to online sellers from “well-liked boards” with out receiving your order or receiving counterfeit merchandise. After sifting via quite a few on-line articles, you’ll rapidly understand that there is very little useful info on the topic.
It is important to begin with a lower dosage range, similar to 10mg per day, and steadily enhance it to 20mg per day if well-tolerated. Beginners should intently monitor their body’s response to the steroid and assess any potential unwanted effects. Furthermore, Anavar stimulates the manufacturing of pink blood cells via a process referred to as erythropoiesis. This improve in purple blood cells enhances oxygen supply to the muscular tissues, bettering endurance and performance during physical actions. You can purchase Var utilizing a number of payment strategies including Moneygram, RIA, Zelle, crypto (Bitcoin), financial institution wire transfers, debit, and credit cards. IFBB licensed professionals on our website offer free coaching to all bodybuilders.
Power begins to rise gradually, especially when Anavar is stacked with testosterone or Winstrol. Water retention stays minimal, allowing for a dry, aesthetic look. In this occasion, users may also expertise water retention and bloating, which Anavar does not cause, plus heightened anabolic results.
The mix of affordability and effectiveness it brings makes Oxandro 10 an incontestable leader in its sector. If you are seeking a efficiency enhancement solution with out breaking the bank, Oxandro 10 from Magnum Prescription Drugs ought to high your listing. Selecting the right Anavar cycle and dosage is important to maximize results whereas minimizing unwanted effects. Whether Or Not you’re new to anabolic steroids or an experienced user, this information provides the best cycle constructions for both women and men trying to improve fat loss, power, and lean muscle definition. Then, when the tablet is in the “safer” a part of the gut (upper intestine), the nutrients begin to be launched into the system and proceed to be released steadily over a two to eight-hour period.
Anavar® contains 4-Androstenolone can be referred to as four androstene-3b-ol,17-one or 4-ANDRO by many within the bodybuilding group for short. 4-Androsterone products are nice stackers, and may be stacked with nearly any compound. Both experimental and anecdotal proof helps 4-Androstenolone’s capability to boost testosterone levels and improve performance. Anavar® additionally incorporates 1-Androstenolone that has a unique construction which makes it favorable to many individuals who need to stability their hormones. This steroid hormone has a double bond on the 1st molecule, which many consider make it extra immune to metabolic clearing. This 1-ene construction also helps resist conversion to many hormones that are not thought of optimal for males like estrogen and dihydrotestosterone metabolites. Thus with 1-Andro you get a prohormone that will enhance your androgen to estrogen ratio, with out including in further metabolites that you would be not want in your system.
Throughout these cycles, people ought to continue to prioritize correct diet, intense training, and sufficient relaxation for optimum outcomes. It is essential to focus on potential unwanted effects and often monitor blood markers and general well-being. For intermediate customers, the dosage vary may be increased to 20-30mg per day, whereas advanced customers might opt for 30-50mg per day. It is important to evaluate particular person tolerance and carefully monitor for any potential unwanted effects.
References:
https://karjerosdienos.vilniustech.lt/imone/anavar-for-women-weight-loss/
SIGMASLOT : Platform Slot Online Gacor Resmi dengan Banyak Bonus
Great post! I really enjoyed the insights you shared. Looking forward to more of your content!
Hello there! This post couldn’t be written any better! Reading through this post reminds me of my previous room mate! He always kept chatting about this. I will forward this post to him. Pretty sure he will have a good read. Thank you for sharing!
0i5i2v
Great article! I enjoyed reading it and learned something new. Keep up the good work!
SIGMASLOT : Platform Slot Online Gacor dengan Bonus Eksklusif
SIGMASLOT : Platform Slot Online Gacor dengan Bonus Eksklusif
SIGMASLOT : Platform Slot Online Gacor dengan Bonus Eksklusif
Great article! I really enjoyed reading your insights. Keep up the awesome work!
Great post! I really enjoyed reading your insights. Thanks for sharing such valuable information—looking forward to your next update!
Awesome article! You’ve provided some really helpful tips. Can’t wait to see more of your content in the future!
Loved this post! You explained everything in such an easy-to-understand way.
Super useful! I’ll definitely be applying some of these ideas.
Really informative read—thanks for breaking it down so clearly!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
It’s difficult to find knowledgeable people in this particular topic, however, you seem like you know what you’re talking about!Thanks
SIGMASLOT : Situs Slot Online Resmi dengan Game Gacor dan RTP Tinggi
SIGMASLOT : Situs Slot Online Resmi dengan Game Gacor dan RTP Tinggi
SIGMASLOT : Situs Slot Online Resmi dengan Game Gacor dan RTP Tinggi
SIGMASLOT : Situs Slot Online Resmi dengan Game Gacor dan RTP Tinggi
Novices ought to put together for a 12-week cycle if they wish to experience the total potential of Parabolan. You should have already got experience with other anabolic steroids earlier than trying this cycle. A 12-week cycle for bulking can consist of a gentle 200mg-400mg trenbolone per week for the whole 12 weeks, depending on which different compounds are being used and the way highly effective they’re. A commonplace stack consists of the usage of a testosterone ester and Winstrol for the earlier few weeks of a cycle.
Testosterone supplementation helps keep balanced hormone ranges, supporting muscle growth and minimizing the risk of unwanted effects like libido loss and fatigue. In the Usa, anabolic steroids, together with testosterone and trenbolone, are categorized as Schedule III controlled substances under the Managed Substances Act. This legislation, enacted in 1990 and updated in 2004, makes it unlawful to possess, distribute, or use these medicine and not utilizing a prescription. Nonetheless, doctors can prescribe testosterone legally, but only for specific medical circumstances corresponding to testosterone deficiency (hypogonadism) and sure types of anemia.
Elevated blood pressure and heartburn are additional negative elements noted by some customers. For some guys, it’s an extreme amount of to deal with, and they cease using Tren, allow it to depart the physique, and recuperate from the unwanted aspect effects. Even those seeing outstanding outcomes will observe their suffering from unwanted effects. Muscle features on the arms alone can get into 2 lbs territory with the best gym work. It’s not exceptional for positive aspects of 30 pounds to be achieved, however you’d have to be probably the most serious hardcore consumer to see such positive aspects and work hard to maintain up them after a cycle. So, like all types of Trenbolone, Parabolan is considered a steroid with versatile makes use of and one value taking a look at, even when gaining large mass isn’t your major objective.
Due To This Fact, trenbolone might exacerbate mental well being points, and thus vulnerable individuals should steer away from this steroid. Tren causes zits because of androgens stimulating the sebaceous glands, inflicting elevated sebum production, which is a waxy substance used to moisturize the pores and skin. Many people find trenbolone to be an emotional rollercoaster, inflicting mood swings each hour. If you battle to go to sleep at evening, trenbolone is most likely not an appropriate steroid due to its stimulative results on the CNS (central nervous system), inflicting insomnia. Nevertheless, for the rest of the physique, customers can count on faster and thicker hair development (3), which may be advantageous for men coveting more grandiose beards. Bodybuilders at our clinic have reported waking up in the course of the night time in a puddle of sweat on trenbolone.
As such, bodybuilders and athletes who use trenbolone throughout bulks sometimes “stack” it with other compounds with larger estrogenic activity that promote extra drastic progress. Total, utilizing trenbolone safely and responsibly is essential for reaching optimal results while minimizing potential dangers. Legal steroid options provide a secure and efficient various for these trying to enhance their efficiency and achieve their health goals.
The draw back to AIs is that they can worsen blood pressure, as sufficient ranges of estrogen are wanted for wholesome cholesterol ratios. Thus, generally, SERMs are a extra optimum alternative to stop gynecomastia, as they don’t negatively affect blood lipids. The most damaging side effects of trenbolone we see are alterations in cholesterol, inflicting a rise in cardiovascular pressure and left ventricular hypertrophy. Though it may not cause extreme will increase in general weight acquire, its capability to add lean muscle tissue is simply rivaled by the likes of Dianabol and Anadrol in our experience. Gynecomastia is unlikely on this cycle, with Winstrol not converting to estrogen and having almost zero progesterone exercise. Thus, the only threat of gynecomastia forming is trenbolone, which reasonably will increase progesterone. Nevertheless, we now have found this to be one of many higher cycles for avoiding man-boobs.
This is expounded to, among different issues, loss of fat tissue, lower in the quantity of water retained in subcutaneous tissues, improve in blood density and in some cases increase in blood strain. It is most frequently used throughout weight reduction, as a outcome of it allows to maintain virtually one hundred pc of muscles despite the calorie deficit. However, due to its huge anabolic energy it is also appropriate for gaining muscle mass.
Some of the most common side effects of Trenbolone embrace zits, hair loss, insomnia, and adjustments in libido. Overall, Trenbolone cycles can be effective for reaching particular objectives such as bulking or slicing. Nevertheless, you will want to rigorously think about the dosages, potential side effects, and post-cycle therapy protocols to minimize the chance of health issues. Trenbolone works by binding to androgen receptors in the body, which promotes protein synthesis and muscle growth. It additionally will increase nitrogen retention, which is crucial for muscle development.
Tren-Max promotes nitrogen retention, and that’s the underlying mechanism for the way it accelerates muscle progress and helps burn fats whereas retaining muscle on a slicing diet. There’s no water retention with Tren-Max, and you want to see considerably improved vascularity, which finally ends up in an outlined and hard physique that’s so sought after by Trenbolone users. Fats loss and gaining of some lean mass will be ramped up on this cycle without water retention attributable to any of the compounds. Testosterone can be included to provide a practical stage of the hormone. Parabolan can be utilized at up to 300mg weekly, and Winstrol oral at 50mg daily most. Different proof suggests that trenbolone use will increase the chance of prostate most cancers through pathways downstream the androgen receptor [8].
Trenbolone helps you keep away from all the nasty side-effects that come together with elevated testosterone ranges elevated fats storage, metabolism suppression, breakouts, temper swings and fatigue. Trenbolone is a strong anabolic steroid used by bodybuilders and athletes who are in search of a competitive edge. This fast-acting type of Trenbolone has a speedy half-life, allowing it to be absorbed shortly into the bloodstream, providing quick benefits. It can be utilized to realize large boosts in each muscle mass and power, in addition to wonderful hardening of the muscles. In addition to these anabolic results, trenbolone may be added to cycles for slicing because of its capacity to scale back water retention and enhance vascularity.
References:
Use of steroid [https://www.google.co.ck/url?q=https://jbhnews.com/tren-trenbolone-acetate-steroid-for-bodybuilding/24831/]
This was a great read. Appreciate the effort you put into this!
continuously i used to read smaller posts that as well cleartheir motive, and that is also happening with this piece of writing which I amreading at this time.
Thanks for shedding light on this topic. Learned something new today!
Your blog always delivers quality content—keep it coming!
This post really resonated with me. Can’t wait to read more from you!
Impressive work! You’ve made an interesting topic even more engaging.
SIGMASLOT : Situs Slot Gacor dengan Bonus dan Hadiah Menarik
Really enjoyed this! Your writing style is so engaging.
This gave me a lot to think about—thank you for sharing your thoughts!
Clear, concise, and super helpful. Great job!”
Kumburgaz su kaçak tespiti Bahçemizdeki su kaçağını yer altı dinleme cihazlarıyla tespit ettiler. Çimlerimize minimum zarar verdiler. Hasan L. https://mysiterank.org/ru/domain/uskudartesisat.com
Always a pleasure reading your blog. Keep the great content coming!
Merkez su kaçak tespiti Evimdeki su kaçağı sorununu hızlıca çözdüler, gerçekten profesyonel bir ekip! https://hugsqueeze.com/read-blog/3705
Thanks for the great read! Very informative and well-written.
Oh my goodness! Incredible article dude! Many thanks, However I am having troubles with your RSS. I don’t know the reason why I cannot subscribe to it. Is there anyone else getting identical RSS problems? Anyone who knows the solution can you kindly respond? Thanks!
Really helpful content — I learned a lot from this!
Great post! I really enjoyed reading this. Your insights were clear and helpful — thanks for sharing!
Really helpful content – thanks for putting this together!
This was a great read! I learned something new today.
Maslak su kaçak tespiti Binamızdaki su kaçağını tespit etmek için kullandıkları teknoloji son derece gelişmişti. Sorunu kısa sürede çözdüler. Cengiz V. https://www.coneckey.com/read-blog/3545
Loved your perspective on this topic. Keep it up!
Thanks for the valuable insights. Looking forward to your next post!
Interesting points! You explained it in a very clear way.
SIGMASLOT : Situs Slot Online Terpercaya untuk Menang Besar
Pola Gacor Mahjongways 2
Znáte nějaké metody, které by pomohly omezit krádeže obsahu? Rozhodně bych ocenil
Such a well-written piece. It kept me engaged from start to finish.
Togel Online
har også bogmærket dig for at se på nye ting på din blog Hej! Har du noget imod, hvis jeg deler din blog med min facebook
Great post! I really enjoyed the insights you shared. Looking forward to reading more from you!
motilium canada – buy sumycin 250mg online cheap buy flexeril generic
Loved this! Super helpful and easy to follow. Thanks for sharing!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Awesome content as always. Keep up the great work!
2019年4月以降:「こちらは日経ラジオ社・日本は19世紀の明治維新以降、先進国として発展し、G7やOECDなど先進国が集う国際組織においても責任ある立場を担ってきた。 SBI PayKey Asia – 日本およびアジア圏における「PayKey」ソリューションの販売・東海大学は、創立者の精神を受け継ぎ、明日の歴史を担う強い使命感と豊かな人間性をもった人材を育てることにより、「調和のとれた文明社会を建設することのできる人材を育成する」という理想を高く掲げている。
Thanks for the valuable information. It really helped me understand the topic better.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
buy propranolol sale – buy plavix 150mg online cheap cheap methotrexate 5mg
Interesting read! Do you have any tips for beginners on this?
Well-written and informative. I appreciate the depth of your analysis.
Very informative post, thank you for sharing!
This is a good start, but I think more details are needed.
Such a useful guide. Bookmarking this for later!
Great perspective. I hadn’t thought about it that way!
An impressive share! I have just forwarded this onto a colleague who was conducting a little homework on this. And he in fact ordered me dinner because I stumbled upon it for him… lol. So let me reword this…. Thanks for the meal!! But yeah, thanx for spending the time to talk about this topic here on your blog.
Thanks for breaking this down so simply!
Your content never disappoints. Keep it up!
Short but packed with value. Love it!
aj9g0f
Can’t wait to read more posts like this. Subscribed!
This strategic timing ensures a smoother transition and maximizes the efficacy of the post-cycle therapy. If the steroid is stopped quickly enough, these results ought to reverse and go away. However if Anavar continues to be used, it may be more durable to reverse or treat virilization results the extra they’re allowed to develop. This is one cause why men, in particular, will choose to not use Anavar – the high value mixed with the reputation it has of being “too mild” can actually put you off.
Anvarol incorporates all-natural ingredients that work together to give users the identical effects as Anavar. It is formulated with elements like soy protein isolate, whey protein focus, BCAA, and ATP, which are all important to building and sustaining muscular tissues. On the opposite hand, Anavar is a synthetic steroid that may trigger vital harm to your body over time. However, with Anavar’s fat-burning effects and muscle gains being retained post-cycle, there’s not an excellent need for most individuals to utilize Anavar all year round.
People that purchase underground lab Anavar by way of the black market might declare doses of 15–25 mg per day are modest. This is due to copious scams where the label states forty mg of Anavar, however actually, it’s only 20 mg. Thus, the above dosage suggestions are based on taking genuine Anavar. There isn’t an unlimited quantity of knowledge relating to the connection between anabolic steroid use and kidney damage.
By promoting the synthesis of proteins, it aids within the restoration process post-workout, permitting individuals to coach at greater intensities and for longer durations. Yes, a well being care provider can prescribe Anavar if they consider it’s medically needed for you. This might embody treating muscle losing or other situations that cause weight reduction.
This may embody gentle energy increments, a firming of the muscle, and a discount in physique fats. The impression of such modifications are often more profound in novices, whereas experienced customers might observe a somewhat more steady shift in course of improved muscle definition and power. Other advantages of Anavar include enhancing stamina and energy because it boosts red blood cells.
It Is relatively delicate, so it doesn’t include too many risks, and it can allow you to achieve your targets faster than should you have been to go on a food plan and exercise plan alone. This steroid can be identified to help enhance vitality ranges, so you can push your self tougher and obtain higher ends in a shorter amount of time. PCT ancillaries such as HCG might help keep the testes stimulated and producing natural testosterone. Damage to the liver can happen in doses from as little as 15mg per day and above. Working longer cycles exposes the liver to more injury over a protracted time period. One of the interesting issues about var is that it isn’t aromatized by the physique.
Holding on to it after the cycle presents a greater challenge than reaching your shredded physique through the cycle, and this is one thing you should plan for. There’s far more to know concerning the side effects of Anavar and all anabolic steroids, so go to my main unwanted effects information right here. When LDL ldl cholesterol increases an excessive quantity of, it can put you vulnerable to blocked arteries and raise your threat of coronary heart disease.
This steroid maintains lean muscle mass during the chopping cycle, sheds body fat, increases energy, and enhances resilience. It is way most popular among women, being a gentle steroid compared to others, since Anavar provides the anticipated optimistic effects with not too many unwanted facet effects. This makes Anavar particularly effective in slicing cycles, serving to users reduce physique fat whereas preserving hard-earned lean muscle (Harber, American Journal of Physiology-Endocrinology and Metabolism).
Aspect effects attributable to rising estrogen levels come about when a steroid causes the conversion of testosterone into estrogen (also referred to as aromatization). One of essentially the most interesting issues about Anavar is that it does NOT aromatize and, due to this fact, doesn’t cause estrogenic side effects. But being based on a really highly effective androgen in DHT, Anavar can come with the risk of androgenic unwanted effects if you’re someone who is already genetically predisposed to them.
Newbies start with as a lot as 50mg day by day, and probably the most experienced users can typically take as a lot as 100mg day by day – but such a excessive dose just isn’t recommended for the novice. Anavar is especially good at getting rid of fat in additional stubborn areas, and for women, that is usually across the thighs and buttocks. Though general body weight could not drop or change a lot, this is due to muscle gain – fats is still being lost. On a proper food plan, women can count on to lose 5-10lbs of fats on an Anavar cycle except they’re lean. Anavar can contribute considerably to some lean features, but for male customers, it’s most unlikely to be a cause for using this steroid. As A Substitute, the anabolic properties of Anavar are most dear for males in terms of MAINTAINING muscle when dropping fat.
References:
https://netjobsall.com/profile/altonfeetham22
As influencers within the fitness area, their affiliation with Anavar products has introduced elevated consideration to how efficient Anavar can be when used properly. Their transformations serve as examples of the ability of Anav Athletics, making it simpler for individuals to see how Anav outcomes can elevate their efficiency. Adequate restoration time is important when understanding, because it permits the body to heal and develop muscle mass. Ensure you’ve no less than one relaxation day per week and permit each muscle group 48 hours of rest before working it once more.
Arginase is the enzyme that breaks down arginine, which is a problem for NO dietary supplements as a result of arginine is the supply of NO manufacturing. With the exception of Hi-Tech Pharmaceuticals, no different complement company has discovered tips on how to deal with the arginase downside head-on… Hi-Tech makes use of ABH and BEC, the novel arginase inhibitors in Anavar®, to flank the excessive dosage of L-arginine and to take arginase head-on by rendering it ineffective. This leaves an abundance of L-arginine uncompromised within the muscle pool to create a wealth of NO, resulting in most muscular vasodilation. For bodybuilders, there is the desire to look fit with out exposing themselves to health implications and other risks like extreme medicine unwanted side effects. This naturally conjures up the search for a simpler various to synthetic steroids. With Anavar being a managed substance in plenty of international locations, together with the united states and U.K., a lot of what’s obtainable on-line is from the underground market.
Whether you’re bulking or cutting, this steroid delivers real results with minimal unwanted effects. In bulking cycles, characterized by an emphasis on muscle development and power gains, Anavar is commonly used in combination with other compounds. Males typically take doses within the vary of 80 to one hundred mg per day, while girls might opt for 20 to forty mg per day. Combining Anavar with different anabolic steroids is widespread during bulking cycles to synergize the results. Anavar (Oxandrolone) is a well-liked anabolic steroid identified for its potential to ship significant outcomes when it comes to muscle definition, energy enchancment, enhanced endurance, and fats loss. When used responsibly and as part of a well-rounded fitness regimen, Anavar may help people obtain their desired physique and performance goals. Anavar and Dianabol are also popular anabolic steroids, however they’ve completely different results and functions.
Pharmaceutical grade and underground (UGL) grade Oxandrolone are each abundant on the black market for people to purchase, but worth variations (and the problem of counterfeit and pretend products) turn into an issue. In comparability with other oral anabolic steroids, studies have demonstrated that Anavar expresses the least amount of hepatotoxicity and pressure on liver function of all of them[5]. It must be famous that Anavar still expresses a degree of toxicity in this space, so it is nonetheless advisable to not utilize Anavar for an 8 – 10 week interval at affordable dosages.
Moreover, consuming enough protein and staying hydrated can additional support muscle restoration and growth whereas using Anavar. There is a noticeable surge in both power and endurance inside the first two weeks of starting the Anavar cycle. Regardless Of its mild nature, it’s important to comply with an acceptable coaching regimen and preserve a proper diet to acquire optimal results whereas minimizing potential side effects.
Conversely, a single dose of 150 mg Androstenolone in Anavar® delivers between biologically energetic milligrams. Hi-Tech researchers have been the first to begin to use these potent compounds — lengthy earlier than the current steroid laws had been revamped to add almost every prohormone known to be a controlled substance. Due To This Fact, our expertise to getting the highly effective prohormones into the bloodstream by far surpasses some other company within the business.
Anavar is a DHT-derived steroid; thus, accelerated hair loss may be experienced in genetically susceptible individuals. There isn’t an unlimited quantity of data relating to the relationship between anabolic steroid use and kidney harm. Testosterone levels sometimes recuperate one to four months after Anavar cycle cessation. An effective PCT protocol can accelerate the recovery of endogenous testosterone. We have found that DHT-related unwanted effects are largely decided by genetics. Thus, some people may expertise significant hair loss from a low dose of Anavar. Whereas others might experience no hair loss while taking excessive doses of trenbolone.
By taking these precautions, you can safely and successfully improve your bodily performance and obtain your health aspirations. As one might have the ability to simply see, Anavar is type of a flexible compound in terms of its makes use of. It is known that anabolic steroids display a really poor proportion of survivability through liver metabolism when ingested orally. It helps promote lean muscle growth, enhance power, and enhance endurance.
More is not recommended as a result of doses which may be surpassing 20 mg per day are almost going to assure the fact that some level of virilization goes to seem. The water retention could be averted because Oxandrolone doesn’t aromatize and there is going to be no water retention. The closest legal different to steroids is a designer steroid that copies the effects and well being elements of actual anabolic steroids while not having a license. Secondary steroids are used along with main anabolic drugs to control side effects or enhance the effectivity of a cycle. These steroids play an integral part in maintaining hormonal balance, regulating estrogenic activity, and guaranteeing general well-being in the course of the cycle’s period.
Nonetheless, in case if misuse, sudden stoppage might result in withdrawal symptoms such as irritability and despair. Do not start or stop the dosage abruptly without the doctor’s advice. In regions the place Anavar is in high demand but supply is proscribed, costs are sometimes elevated. On the other hand, in areas with plentiful supplies, prices could additionally be more affordable. This demonstrates the necessity to stay knowledgeable about regional pricing developments for Anavar.
Elevated liver enzymes doesn’t mean that the liver is broken, nevertheless which means it may be broken in case proper measures won’t be taken. Though it’s hepatotoxic, you will need to notice that Oxandrolone is among the milder steroids as there are others on the market that are thought of to be lots rather more worse. Assuming that the person is having a healthy liver and a use that isn’t going over the beneficial occasions then the liver ought to get well again to regular fairly fast without having any harm at all. Though it certainly can be very helpful in the course of the off seasons, Oxandrolone still stays to be greatest in the course of the cutting section when the individual is looking for fats burn while maintaining the muscle tissue.
References:
steroids for headaches – https://icmimarlikdergisi.com/kariyer/companies/anavar-before-and-after-practical-outcomes-examined-for-fitness-lovers/,
I’m not that much of a internet reader to be honest but your blogs really nice, keep it up! I’ll go ahead and bookmark your site to come back in the future. All the best
order coumadin without prescription – reglan over the counter cozaar 50mg brand
It is necessary to start out with a low dose, comply with the really helpful cycle length, and undergo post-cycle therapy to reduce the danger of side effects and promote optimum outcomes. It is also necessary to make use of Anavar 50mg responsibly and beneath the steerage of a healthcare skilled. In addition to SERMs, supportive dietary supplements may be thought of during PCT to help preserve total health and facilitate the recovery course of. This might embody supplements that help liver perform, cardiovascular well being, and common well-being. Implementing a post-cycle remedy (PCT) protocol after finishing an Anavar (Oxandrolone) cycle is essential for restoring natural hormone manufacturing and maintaining optimal well being. While Anavar is considered a relatively gentle steroid with low danger of testosterone suppression in comparability with other compounds, it can nonetheless cause some level of suppression. PCT goals to mitigate the potential adverse effects of suppressed testosterone levels and help the body regain its natural hormonal balance.
However, it’s necessary to use warning when using any steroid, as they are often harmful if not used correctly. All The Time follow the really helpful dosage and consult with a healthcare professional before use. PCT is important after your cycle to assist your physique re-establish the correct stability of hormones.
It’s also important to supply your dietary supplements from respected and reliable suppliers. We have offered an general “how-to” cycle guide to Anavar attached in this FAQ, which is identical data to cycling oxandrolone, as a result of once more, it is identical. Please click on the really helpful cycle length and dosage for Anavar is this FAQ section. It is the active ingredient that makes up Anavar, and is what our high-quality Anavar is created from to make sure superior outcomes.
Like another compound, Oxandrolone could have potential side effects, particularly when used excessively or without proper steering. Users have reported changes in skin colour, nausea, headaches, and modifications in sexual desire. More critical unwanted side effects would possibly include temper adjustments, swelling of palms or feet, unusual tiredness, or problem in breathing.
It’s important to do your analysis and only purchase from reputable sources. If you’re looking to purchase Anavar in Mexico, there are some things you need to know earlier than making your purchase. In this section, we’ll cowl the legality and dangers of buying Anavar in Mexico, online sources and retailers, worth and high quality, prescription and security, and product variants. Anavar is commonly used in cutting cycles, the place the aim is to minimize back physique fat while maintaining muscle mass.
Anavar works by binding to androgen receptors within the body, which helps to increase protein synthesis, resulting in muscle progress. It also will increase nitrogen retention within the muscular tissues, which is crucial for muscle growth and restore. Anavar additionally has a unique characteristic in that it inhibits the production of cortisol, which is a hormone that can break down muscle tissue and result in weight achieve. This makes Anavar a preferred choice for athletes and bodybuilders who wish to construct lean muscle mass whereas maintaining a lean physique. Oxandrolone stands out as a preferred supplement among bodybuilders, and its effectiveness has been highlighted via numerous person experiences. However, as with any supplement, it’s important to proceed with warning and moderation.
It’s essential to do your research and browse critiques earlier than making a purchase. Some well-liked on-line sources and retailers for Anavar in Mexico embody CrazyBulk, Anabolic Research, and MexGear. As previously said, one of many biggest issues going through the market is fake Anavar. Be careful when making purchases to forestall being a sufferer of faux products. Anavar is a dear steroid, so it could be a cause for concern when you see it being marketed at a lower cost.
Their major objective is to facilitate muscle growth, promote fat loss, and overall, improve aesthetics, which makes them well-liked amongst athletes, gym goers, and bodybuilders. With this systematic evaluate and meta-analysis on black-market AAS, we now have demonstrated that substantial mean proportions could also be of substandard high quality or counterfeit. The very wide range in proportions of counterfeit or substandard black market AAS places the user in a situation of unpredictable uncertainty.
The next thing to recollect is to ditch the pretend product with no second thought. Holding onto it might tempt you or others who have access to it to strive it out regardless of the risks. The best course of action is to do away with the counterfeit complement effectively and safely. One Other various that has made waves out there is Paravar, produced by Crazy Mass.
In short, authorized and authentic Anavar, together with their options, share a goal of advancing an individual’s peak performance through muscle development and fat loss. Whereas they exhibit similar characteristics and goal to produce comparable outcomes, the choice to make use of one product over the other often boils down to non-public objectives, values, and threat tolerance. In some cases, the printed knowledge had to be manually adapted and transferred to fit our classification system. This additionally could have led both to over or beneath estimation of certain proportions of the estimates of “substandard” or “counterfeit” anabolic androgenic steroids and their subclassifications and sub-analyses. Some authors have analyzed and in contrast the amount and quality of various AAS formulations. Both the proportion of substandard and counterfeit merchandise are described to be larger in formulations for oil-based solutions used for injectables compared to tablets used for oral administration [25, 26, 36, 43]. Counterfeit proportions for oil-based solutions in comparison with tablets are described as 43–65% vs. 29–37%, respectively [25, 43].
Commonly this approach is embedded in a wider prevention strategy that features counselling companies and different quick interventions [63, 64]. In this systematic evaluate we demonstrate that the true composition, the kind of production, focus, quantity, quality, and purity are often not declared on the label, and labels are even misleading. In the case of mislabeled AAS acquired on the black market, it is at present not exactly recognized what’s consumed by the consumer.
References:
Steroids To Get Ripped (https://matkafasi.com/user/paintbongo7)
You can stack Anvarol with different CrazyBulk dietary supplements to assist you reach your health targets even quicker. For example, if you’re trying to add muscle mass, you can stack CrazyBulk’s bulking supplements, such as D-Bal, Testo-Max, and Trenorol. The frequency of Oxandrolone cycles per year can range considerably primarily based on individual targets, tolerance ranges, and responses to the substance. A typical course of can last from four to eight weeks, adopted by an acceptable interval of off-cycle time to allow the body to recover. Consequently, assuming enough restoration durations, conducting a number of cycles within a 12 months is feasible.
Anavar utilization at the intermediate degree requires being all ears to your body’s responses and making modifications accordingly. The intersection of adequate knowledge, the right dosage, cycling, possible stacking, and PCT may lead to remarkable outcomes, edging you nearer to your bodybuilding targets. When taking two oral steroids collectively, it’s imperative to scale back every dose by half. For instance, in case your traditional Anavar dose was 60mg and your usual Anadrol dose was 100mg, you’d take 30-40mg of the previous and 50mg of the latter. Like Anavar and Deca, Anavar and Dianabol can be a bit of an odd combination and one that solely a few people actually use. Understanding the potential dangers earlier than starting your cycle is crucial—learn more in our detailed information on Anavar side effects. Regardless Of being milder than different steroids, Anavar can still trigger endocrine disruption if not appropriately cycled, especially in men working larger doses with out testosterone support.
Alcohol will increase cortisol, a catabolic hormone that may blunt some of Anavar’s fat-burning and anabolic effects. High doses of Anavar give me back pumps and jaw pumps as if I am chewing tough meat like beef jerky. I never do over forty mg on orals as a result of again pumps are annoying, and never more than 4 weeks. I’ve been on 60 mg break up over 3 times a day for 4 weeks, and I’m getting some decrease back pain, stomach pain, and a extremely darkish yellowish urine.
So, an increase in weight doesn’t essentially mean you’re not dropping fats. In sum, inside the first two weeks of an Anavar cycle, whereas the transformations may not be too drastic, the promise of impactful outcomes turns into clear. The preliminary gains in strength, onset of the fats burning process, and subtle signs of muscle definition all point to the optimistic course the physique is about on with Anavar. Your way of life is one other massive factor that’s often missed when planning a steroid cycle. Anabolic steroids can put a lot of stress on the physique, particularly the stronger compounds, so it may be very important stay a wholesome, lively life-style. Not solely will this assist to limit the chance of unwanted facet effects, however it’s going to additionally make sure you get the very best results. Another major concern could be high blood pressure, round 70% of hypertension cases additionally suffer from excessive physique fats levels.
If you want to minimize fat and get leaner, you’ll find a way to stack Anvarol with CrazyBulk’s chopping dietary supplements, corresponding to Clenbutrol and Winsol. You can even stack Anavar with steroids like Winstrol, Clen, and Trenbolone for cutting functions. As a general rule of thumb, most Anavar cycles should be between four and eight weeks in size. It’s essential to notice that everyone responds in a different way to Anavar, so you could want to adjust your dosage or cycle length relying on how your body reacts.
Significantly for a bodybuilder throughout a minimize, this is in a position to be one thing they would tremendously recognize in utilising because when they are slicing, their caloric intake is greatly decreased. An Oxandrolone cycle is widespread amongst those that have by no means used anabolic steroids and need a compound that causes little unwanted effects and can also be orally active. Maintaining a daily dosage of 10 milligrams minimizes the risk of masculinization side effects.
The greatest method to get shredded in a short area of time is to construct muscle and burn fats simultaneously. Secondly, Anavar is commonly considered to be a greater option for women because it has fewer virilization effects than Winstrol. Girls who use Winstrol could expertise side effects similar to facial hair progress and a deeper voice. It’s additionally important to cycle Anavar to keep away from side effects and preserve its effectiveness. A typical Anavar cycle lasts between 6-8 weeks, followed by a break of 4-6 weeks earlier than beginning one other cycle.
Remember to always seek the advice of with a professional healthcare professional earlier than starting any steroid cycle or PCT protocol. When choosing the right PCT for Anavar, there are a number of factors to consider. Anavar is a light steroid, however it could still suppress your natural testosterone production. Due To This Fact, it is important to make use of the best PCT to assist your body get well after a cycle. In brief, testosterone spikes protein synthesis will increase muscle mass/strength, and enhances fat loss. You will feel the effects of steroids to get ripped after about a week and a half. Over a six week cycle, you need to anticipate to drop 2-3 physique fats percentage points.
However, Anavar will cause important quantities of fat loss, notably in cussed areas. As anabolic steroids are unlawful and can’t be prescribed for cosmetic functions, bodybuilders’ only possibility is to buy them on the black market. Though steroids are doubtlessly harmful and there might be evidence for a shorter life expectancy, some do take anabolic steroids and reside long lives. This is why some bodybuilders stack androgenic compounds with Deca Durabolin, similar to testosterone, helping to maintain nitric oxide ranges high. In our expertise, dosages over 10 mg/day will enhance the chance of undesirable effects. In most bodybuilders who utilize average to excessive dosages of testosterone, blood pressure will rise, with the severity relying on the dose and cycle period.
Anabolic steroids and different forms of fat loss and performance PEDs are sometimes stacked with Clen. Anavar provides a means more vital enhance to strength and is superior in drying out the physique and enhancing vascularity – hence why it’s usually used in contest prep cycles. For pure fats loss, Clenbuterol is a extra smart choice (though a riskier one with extra aspect effects), while if muscle and strength gains are extra your priority, then Anavar ticks the boxes. When it involves pure weight reduction or fats loss PEDs, Clenbuterol is taken into account presumably the perfect of the bunch. Only if you can deal with the unwanted effects, however it’s actually not for everyone.
References:
https://orcid.org/0009-0005-8614-7779
This relatively low dosage, mixed with a shorter cycle, minimizes the potential for undesirable unwanted facet effects whereas offering noticeable enhancements in lean muscle mass and total body composition. This cycle is usually favored by newbies or those wishing to maintain a lower danger profile with Anavar use. Anavar is also called Oxandrolone which is the most popular steroid within the bodybuilding and fitness world. Many men and women can use the Anavar cycle to enhance their physique, energy, and total performance.
Nonetheless, the steroid carries vital risks of unwanted effects that can trigger severe issues with mental and bodily well being, and the risks of dangerous drug interactions are also excessive. Some supplements like Omega Fatty Acids and Grape Seed Extract can lower LDL cholesterol levels. Anavar, a drug, could lower total levels of cholesterol and blood strain.
Searle & Co (Now Pfizer) and was offered within the Usa and the Netherlands under the Anavar trade name. It is a DHT derived anabolic steroid, similar to Masteron and Winstrol. It is an orally active 17-alpha-alkylated compound, giving it the power to survive the “first pass” of liver metabolism and allowing it to be ingested effectively. It is a flexible androgen and can be used in both cutting and bulking stacks/phases. As with some other medication, it’s a good idea so that you can discuss to your physician before taking any new medications. If you are struggling with gaining the burden you should be healthy, you may need to take a drugs like oxandrolone.
Throughout this time, the person takes Anavar daily in a particular dosage – more on this immediately beneath. Some individuals additionally use different supplements or medicine during the cycle to boost the consequences or to assist with restoration afterward. Nevertheless, cycling without proper medical guidance can be dangerous and lead to harmful unwanted side effects. Whereas it has reliable medical makes use of, oxandrolone is also commonly abused for its muscle-building effects. Though Anavar bodybuilding properties may be spectacular, improper use can lead to severe well being risks. Another critical thing to mention is that anabolic steroids are controlled substances. Utilizing steroids with no prescription can result in severe authorized consequences, including jail time.
When it involves fat loss, getting in and out quicker will at all times be higher. No one needs to spend months and months in a calorie deficit – it merely just isn’t fun. That mentioned, for some folks, it may be a bit more durable and they may want slightly increase, most individuals will attain for Clenbuterol.
The unwanted effects of the artificial steroid are normally not too harmful at low doses. Nonetheless, larger doses and long-term use can lead to unintended effects. Anavar may help women shed pounds in their midsection by concentrating on several sorts of fat. Anavar is best known for its ability to burn fats, but it also has several benefits for athletes. In this submit, we’ll talk about the benefits, side effects, regular results, and the method to use Anavar for women. Feminine bodybuilders usually choose it as a favourite as a end result of it builds muscle with out causing masculine features. Sure, Sustanon is a blend of four testosterone steroid esters, so this makes it extra powerful than just a single testosterone steroid.
Anavar is a gentle steroid, however it may possibly nonetheless have unfavorable results on your sexual health. One of the most typical side effects of Anavar is a decrease in testosterone ranges. Testosterone is a hormone that plays a key position in sexual operate, so a decrease in testosterone can lead to a decrease in libido. This may find yourself in decreased sexual need and difficulty attaining or maintaining an erection. If your major objective is to concentrate on strength features, different steroids with more potent anabolic properties, similar to Anadrol or Dianabol, could additionally be more appropriate choices. These steroids are better recognized for his or her capacity to rapidly enhance strength and muscle mass, especially during bulking cycles. Anadrol is a more potent anabolic steroid that might be more practical for building muscle.
If any of those effects last or get worse, tell your physician or pharmacist promptly. Somewhat we advise using a natural and legal different like the Anvarol. Then contemplate the chopping stack if you’re looking to combine Anvarol with different comparable nice slicing supplements. In most cases, nausea will go away on its own after a couple of days or weeks. If you experience nausea while taking Anavar, it is necessary to discuss to your physician. They could possibly prescribe a different medication that doesn’t trigger this facet impact. Overall, the elevated vitality ranges supplied by Anavar can be extraordinarily useful for many who wish to enhance their physical performance.
Ideally, you’d combine it with IGF-1, which does better on this 2–3-week length. You can have a look at T3 and insulin for the more hardcore, however only if you know what you’re doing with those compounds. You won’t be as involved about utilizing ancillary compounds during these short cycles, however if you want to go ahead with some, you’ll take a glance at the identical compounds talked about for the opposite longer cycles. Here’s only one instance of a normal 12-week cycle, including concepts for newbie, moderate, and heavy users. You can add an entire range of bulking steroids as a secondary (and even third) compound, including both orals and injectables.
If you’ve experienced unwanted aspect effects with a similar dose of any testosterone steroid, then you’re likely to see the same factor happen with this one. There’s so much to assume about if you’re nonetheless deciding between utilizing Sustanon or single-ester testosterone. Finally, it’s going to come all the means down to the sort of cycle or stack you propose to run and how usually you’re snug injecting.
Any variations might be in the timing of the onset of antagonistic results (if any). Sustanon 250 is usually chosen for TRT functions over single ester testosterone. A big good factor about Sustanon for testosterone substitute is to minimize the variations or ups and downs in your testosterone levels day-to-day – as long as you’re injecting it on an everyday schedule. With this size of half-life, you also have to commit to using Sustanon 250 for a comparatively long cycle to make it worthwhile. Taking the dose to 600mg per week puts you in what many contemplate the sweet spot of testosterone use. 750mg per week is usually really helpful, and I would not hesitate to take that amount of Sustanon.
Sustanon 250 and trenbolone are a strong mixture used for both bulking or chopping functions. Nevertheless, we have found that running larger dosages will trigger extra pronounced side effects, which we will detail within the side effects section of this information (further down). Like testosterone enanthate, Sustanon 250 could be injected once or twice per week.
References:
https://doodleordie.com/profile/bitetest1
Shark Bounty : Platform Slot Online Gacor dengan Jackpot Besar
Parts like modifications in physique weight, energy, and the looks of any antagonistic results have to be assessed periodically. A cutting cycle is a period of time the place the primary objective is to lose physique fat whereas preserving muscle mass. Anavar is commonly used during chopping cycles as a outcome of it has been proven to promote fat loss while preserving muscle mass. The impact on libido varies from person to person, and elements such as dosage, period of use, and particular person response play significant roles. It is crucial to seek the guidance of with a healthcare skilled and follow accountable utilization practices to manage potential libido adjustments successfully. Like different anabolic steroids, Anavar can have an effect on hormone ranges, together with testosterone, which plays an important function in sexual perform. In summary, Anavar and Primo are DHT derivatives that are usually utilized in female bodybuilding.
As with all Anavar cycles, accountable utilization, a constant exercise routine, and proper diet are critical to derive the maximum benefits and reduce potential risks. The effectiveness of Anavar in enhancing physical efficiency and physique composition is significantly influenced by the food regimen and train routine it’s mixed with. For girls utilizing Anavar, understanding tips on how to optimize nutrition and coaching is essential for maximizing advantages while minimizing potential dangers.
Consequently, some girls have questioned whether or not Winstrol is an acceptable steroid or whether or not it causes virilization-related side effects. Many females are limited in regard to which compounds they will use, as many AAS cause masculine side effects (1), compromising a woman’s natural magnificence. Anavar is metabolised in the kidneys and misusing or abusing this drug may find yourself in kidney harm. You are subsequently suggested to seek the assistance of your doctor or bodybuilding coach earlier than running an Anavar cycle. If so, you might have heard of the steroid Anavar and its purported ability to assist with weight reduction. It’s important to method this topic with readability, as sustaining a healthy libido is crucial for overall well-being and quality of life.
When folks generally consider steroids, they think of them in a unfavorable gentle, as they’ve a popularity for being dangerous. In this article, we’ll reveal every little thing you want to know about Primobolan to have the ability to determine whether or not you must think about its use for crushing your physique objectives. For instance, such results as shared are achieved only when you’re having a correct life-style, properly using Anavar and numerous other factors.
In most cases, libido returns to regular within a few weeks or months after discontinuing Anavar. While it can influence hormone ranges and doubtlessly result in a decrease in libido, this effect is normally temporary and reversible. Nonetheless, you will want to understand that Anavar can influence hormone ranges in the physique, which in turn may affect libido to some extent. HPG axisUsing steroids can influence the hypothalamic pituitary gonadal (HPG) axis, the system that ties your brain to the gonads telling them make testosterone/oestrogen. LiverIt’s well documented that an oral steroid, such as Anavar, can enhance our liver enzymes and can cause hepatotoxicity (chemically driven liver damage). This is commonly seen in blood work as an increase in alanine transaminase (ALT). Thus, it would make sense to help your liver all through utilization when you were to take them.
Whereas Anavar has a decrease risk of virilization compared to many other anabolic steroids, it isn’t entirely risk-free. It Is necessary to notice that some virilization effects, significantly voice modifications, could be everlasting even after discontinuing use. Long-term use issues are significantly essential for feminine bodybuilders who may be tempted to make use of Anavar constantly or for prolonged intervals. While the compound is considered milder than many other anabolic steroids, extended use can still result in hormonal imbalances and enhance the risk of virilization.
Anavar can have a quantity of unwanted side effects, together with liver injury, high blood pressure, and ldl cholesterol adjustments. However, the use of Anavar can have potential results on the menstrual cycle of girls. In this complete guide, we’ll explore how Anavar affects the menstrual cycle and what girls should know before using it.
Additionally, by maintaining lean muscle during fat loss, Anavar supports a higher metabolic price, making it simpler to handle weight over the long run. Anavar, additionally recognized by the name Oxandrolone, is an oral anabolic steroid that has turn into a favorite among bodybuilders, athletes, and fitness enthusiasts. Originally developed within the 1960s for medical functions, it was used to advertise weight achieve in sufferers coping with muscle loss or recovering from surgery. Its powerful results on improving bodily performance and look shortly made it in style within the health world. One of the first benefits of Anavar for female athletes is increased muscle strength with out substantial weight acquire. This is particularly advantageous in sports activities where weight categories are a factor, as it allows athletes to extend their strength-to-weight ratio with out transferring up to the next weight class.
Let’s face it, Anavar too could presumably be poisonous and might come with a very severe life-threatening side-effect which in severe cases might end in even sudden demise. It’s an thought for someone who’s by no means taken steroids before it can function a great “entry” drug for a newbie because it doesn’t come with a lot of harsh unwanted effects. According to 1 group of individuals, it’s so as a result of steroid builds muscle and since you should practice and following correct diet plan, therefore you look leaner. You would possibly notice changes in your menstrual cycle as a end result of Anavar’s impression on hormone levels. Be aware that Anavar unwanted effects can embrace irregular intervals or amenorrhea, especially at larger doses. When considering Anavar, consult with healthcare professionals to thoroughly assess potential risks like hormonal imbalances and virilization.
Nevertheless, the steroid carries important dangers of unwanted effects that may trigger critical problems with mental and physical well being, and the risks of dangerous drug interactions are additionally excessive. Winstrol is usually not recommended for girls because of the high danger of virilization signs. Regardless Of Winstrol’s probably masculinizing results, it remains cardiotoxic and hepatotoxic. We have seen women achieve 10–15 pounds of lean muscle from their first Winstrol cycle. Hair loss is a common side impact amongst women who take Winstrol, which is due to an increase in DHT ranges (a hormone damaging to hair follicle health). Women usually avoid virilization results when taking 5 mg/day of Turinabol in 5-week cycles. Winstrol is not a steroid that requires massive doses to produce nice results in ladies as a end result of it’s a robust steroid (and girls naturally only have small amounts of testosterone).
This is perhaps one of many explanation why it is extremely well-liked amongst feminine bodybuilders. In most purposes, the steroid is especially used for fats burning and thus makes it very attractive for those are eager on chopping cycles. In addition to fat burning, it can also be used to barely develop muscle mass, however this have to be done along side the proper food plan, and a really sensible workout regime. In Contrast to different anabolic steroids commonly used by girls, similar to Winstrol or Primobolan, Anavar is commonly thought of the mildest choice. Monitoring progress and adjusting the strategy as needed is crucial when using Anavar for weight reduction.
Just be patient and constant and you will notice some wonderful results even if not quickly, but in a long run, you will surely do. Anavar is also a popular selection among athletes as a outcome of it increases endurance degree (strength) with out accumulating mass. In Accordance to some individuals, Anavar is a efficiency enhancer and it is traced in blood for three weeks. Also, with affordable dosages, it won’t shut down the HPTA, and all you need for full fast restoration is a use of some publish cycle dietary supplements and you might be good to go. Anavar increases nitrogen retention which helps your muscle to contract extra whereas lifting, and as a result person positive aspects energy without gaining lots of mass. This method it helps strengthen the smaller muscle fiber too that don’t normally get a chance to get worked on.
References:
best non steroid supplement for muscle growth (https://articlescad.com/anavar-results-in-bodybuilding-comparing-the-earlier-than-and-after-14775.html)
This mixture shouldn’t be done for longer than eight weeks, with 6 weeks as the popular length. Most individuals have opted for the combination of HCG and Nolvadex as a end result of fewer side effects than other SERMs like Clomid. Drugs like Nolvadex or Clomid make the hypothalamus produce extra testosterone by making a negative feedback loop. In Accordance to government knowledge, most people just don’t consume enough Omega 3. As a end result, you will want to take some Omega-3 supplements that can assist you struggle inflammation and ldl cholesterol. Anavar was made to help folks with ailments like HIV that may trigger them to lose lots of weight. This article discusses safety considerations for users of this cycle to focus on.
Nonetheless, increasing the variety of drugs in a stack can even improve the potential for side effects. The allure of swift muscular features and bolstered physical performance certainly has its attraction. On the other hand, the potential adverse results warrant significant thought. Due To This Fact, one has to consider all elements and situations, and make the most knowledgeable private choice that aligns with their propensity for threat and their long-term well being and health aspirations.
The problem is that it will also have probably the most extreme side effects, particularly if taken for a quantity of years. I had to get a deeper perspective on users who decided to use both of the substances solo to test its influence on their vascularity, efficiency stage, lean muscle development & fats burning. Measuring fat loss with scales may be misleading as a result of simultaneous muscle growth.
At the lower finish, beneath 500mg, you’re taking a glance at testosterone substitute and some noticeable boost to power, power, recovery, and positive aspects. Nonetheless, taking a minimal of 500mg weekly is normal, usually growing to 1000mg for significant gains. Not Often will it be needed to increase the Check dosage to anywhere close to 2000mg. Primobolan is also a DHT-derived steroid, and it’s an excellent one to make use of in long cycles as it’s a tolerable compound with lowered androgenic effects and milder testosterone suppression. Joint and bone assist could be why some people add Deca to a protracted cycle as a secondary compound. Adverse libido impacts are potential; dosage is commonly set at half of the testosterone dose to combat this. Long-cycle testosterone dosage will vary from 200mg/weekly at the low end if you’re in search of HRT only… Up to 800mg or much more on the high finish when cruising on a long cycle.
Between these brief cycles, you ought to use Clomid or Nolvadex if you’re worried about LH and FSH levels, however most of the time, they rebound well. Stacking in these quick cycles is essential since you’re already getting the maximum of each compound. By combining them, you benefit from a higher stage of androgens without essentially rising the chance of unwanted effects. Any of the above-recommended stacks, for example, the Dianabol/Winstrol stack, will provide satisfactory outcomes. Some will select a Dianabol-only cycle for six weeks, with that oral steroid not being massively suppressive, but it does have the draw back of manufacturing lots of water weight. There’s room to move with experimentation as soon as you’re a extra assured person.
Genetics would be the main consider how dangerous your hair shedding is, so if you’re lucky enough to keep a full head of hair, you’re in the minority. Even guys who aren’t normally susceptible to male pattern baldness with other AAS can see some hairline receding and hair shedding. After using Masteron, men will want to run PCT to restore pure testosterone function. Masteron will provide a nice psychological boost to this cycle, drying you out and adding vascularity. Muscle gains may also be moderate; anticipate 10 lbs on the most, however this must be absolutely maintainable. Winstrol will give you a grainy and veiny appear to be no different steroid. There’s a good cause it’s considered a god of contest prep – it supplies aesthetics that even a fantastic steroid like Masteron can’t match.
The cycle should last no more than six weeks to manage risks successfully. To regulate blood pressure and cholesterol levels, attempt eating over 30 g of fiber day by day. Anavar, also identified as Oxandrolone, is a well-liked hormone utilized in bodybuilding for chopping, bulking, and restoration. Winstrol just isn’t used by bodybuilders during bulking phases because it does not retain water properly. Nonetheless, it’s popular amongst fighters who need to be lean and toned earlier than matches or fights. These who want to get probably the most out of their workouts can attempt a cycle of Winstrol and Anavar. This can result in a simpler workout and dramatic muscle development in much less time.
Lastly, it is important to intently monitor oneself for any physical or psychological modifications during the winstrol cycle. If adverse unwanted aspect effects start to manifest, it’s beneficial that the person reduces the dosage, discontinues use, or seeks advice from an experienced particular person. One Other notable impact of Winstrol used solo is its capacity to enhance endurance. It achieves this by increasing the variety of red blood cells which are very important for carrying oxygen all through the body. With an elevated oxygen supply, muscular tissues can work tougher and recuperate faster, allowing for extra intense and sustained coaching sessions.
Primo helps maintain muscle mass on a cutting food regimen however is more doubtless to cause comparatively excessive suppression at greater doses, and that’s the purpose the place you’d also get the strength and lean mass features. Primobolan is mostly not thought-about the most effective sole compound for this length cycle because you would typically need to use it for greater than eight weeks. It seeks to take care of your hard-earned muscle mass whereas shredding away excess physique fats.
Neither compound will cause any weight reduction due to simultaneous muscle progress. In conclusion, each Anavar and Winstrol have their advantages and downsides. It’s up to you to resolve which steroid is best in your objectives and physique type. Always remember to make use of steroids responsibly and follow correct dosage and cycle size tips. Nevertheless, getting older we start to lose out on the advantages of our magical T. And we do typically experience undesirable adjustments with our muscle mass, libido and stamina.
References:
how many different types of steroids are there – https://elevateducation.com/members/fieldhour0/activity/1367777/,
Great post! I really enjoyed reading this and learned a lot. Thanks for sharing!
This is exactly what I was looking for—thanks for the helpful tips!
Platform Slot Online dengan Fitur Terbaik dan Kemenangan Terjamin, hanya di SIGMASLOT
Phim sex clip sex Việt Nam
Very well written. Looking forward to more posts like this!
Just want to say your article is as astounding. The clarity for your put up is just excellent and that i could think you’re a professional on this subject. Well together with your permission allow me to seize your feed to keep updated with approaching post. Thanks 1,000,000 and please carry on the enjoyable work.
Interesting perspective! It gave me a new way of thinking about this topic.
Thanks for the valuable information. It was easy to understand and super useful.
qqatzv
I love how you explained this so clearly. Subscribed for more!
This post really resonated with me. Appreciate your honesty and insights.
levofloxacin us – order generic ranitidine 150mg purchase zantac
order esomeprazole 20mg pill – buy generic topiramate over the counter buy sumatriptan 25mg sale
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
su kaçak bulma Banyodaki su kaçağını bulmak için kırmadan dökmeden çalıştılar. Çok titiz ve düzenli bir ekipti. Gülşen Z. https://roadcosmos.com/author/kacak/
Great post! I really enjoyed reading this.
Beykoz su kaçak tespiti Evde Güvende Hissettik: Çalışanlar oldukça güven vericiydi. Evde rahatlıkla çalıştılar. https://hygiene-premium.com/?p=3262
Yeniköy su kaçağı tespiti Binamızdaki su kaçağını tespit etmek için kullandıkları teknoloji son derece gelişmişti. Sorunu kısa sürede çözdüler. Cengiz V. https://www.toofoodies.com/?p=19636
https://www.euro274a.com/
Very informative, thanks for sharing!
Panduan Lengkap untuk Daftar Togel Terpercaya : Cara Mendaftar dan Menang di Situs Togel Terpercaya
İcadiye su kaçak tespiti Hızlı ve doğru tespit, hasarı en aza indirir. https://www.grand-indonesia.com/author/kacak/
Anadolu Yakası su kaçak tespiti Özel kameralar, boruların içini inceleyebilir. https://www.shoprtscigars.com/uskudar-tesisatci-tikali-lavabo-acma/
Nikmati Permainan Slot Gacor di sigmaslot dengan RTP Tinggi dan Jackpot Menggoda
Los corticosteroides orales son esteroides que se toman por vía oral y se utilizan para tratar una variedad de condiciones médicas, como las enfermedades autoinmunes y las reacciones alérgicas graves. Estos esteroides son más potentes que los tópicos, inhalados u oftálmicos y pueden causar más efectos secundarios. Los esteroides anabólicos son sustancias sintéticas relacionadas con la hormona sexual masculina, la testosterona. Se utilizan para potenciar el crecimiento muscular o para acelerar la recuperación de las lesiones. Muchos creen que es imposible que exista el deporte profesional del culturismo como lo es ahora sin que los atletas usen esteroides anabólicos. El tamaño y la calidad de los físicos se empujan a límites que se hacen imposibles por medios naturales. La cuestión de si es authorized comprar esteroides por web en España es un tema que suscita debate en relación con la legislación actual.
Un estudio de 2014 encontró que los participantes que la usaron durante un período de entrenamiento de 6 semanas reportaban mayor energía y mejor concentración, pero no aumentaban su masa corporal ni su rendimiento general. Este es un breve resumen de qué suplementos puedes usar en pequeñas dosis y cuáles debes evitar. Nunca utilizamos el nombre de la empresa o la palabra ” esteroide ” en el embalaje.
Tu cuerpo fabrica sus propios esteroides (también conocidos como “esteroides corticosuprarrenales”), que te ayudan a combatir el estrés y a desarrollarte durante la pubertad. También hay un tipo de medicamento llamado esteroides (también conocidos como corticosteroides) que la gente puede tomar cuando tiene dolor, asma o problemas en la piel. Pero estos no son los tipos de esteroides a los que nos referimos cuando hablamos sobre el rendimiento deportivo y la musculación. La aspirina está aprobada para su uso en el tratamiento de dolor, ictus, ataques cardíacos y artritis. Este medicamento contiene ácido salicílico, por lo que no debe utilizarse en niños y adolescentes. El uso del salicilato en niños se ha relacionado con el desarrollo del síndrome de Reye, una enfermedad grave que provoca daños en el hígado y en el cerebro. La aspirina funciona para aliviar el dolor mediante el bloqueo de la producción de hormonas locales (prostaglandinas) que causan dolor e inflamación.
La Boldenona mejora la vascularización y proporciona un aspecto musculado, mientras que el Dianabol asegura un arranque rápido con ganancias visibles desde las primeras semanas. Además, el Masteron Propionato potencia la definición muscular y realza la calidad física, siendo perfect para usuarios avanzados que buscan resultados de alto impacto. Formulado para potenciar el volumen y la fuerza en usuarios avanzados, este ciclo de eleven semanas combina compuestos de alta eficacia para obtener ganancias musculares significativas, sostenidas y con mejor rendimiento. Incluye soporte hepático y hormonal para garantizar resultados seguros, efectivos y duraderos, optimizando al máximo el desempeño físico.
Sin embargo, rara vez se utilizan en el ámbito deportivo, ya que su eficacia es bastante baja y tienen muchos más efectos secundarios que los esteroides sintéticos. ¡Bienvenido a nuestra tienda online de esteroides anabólicos, Anabol-es.com! ¿Estás cansado de los largos entrenamientos sin conseguir los resultados que deseas? Aquí puedes encontrar la solución – esteroides anabólicos, un remedio universal para el aumento acelerado de la masa muscular. Quienes incumplan el marco regulatorio para la venta de esteroides en México se enfrentan a consecuencias legales graves, que pueden ir desde multas económicas hasta el cierre del establecimiento comercial. Por ello, es basic para los comerciantes mantenerse informados sobre las leyes y regulaciones vigentes en materia de esteroides y asegurarse de cumplir con todas las disposiciones aplicables.
En nuestro catálogo siempre podrás comprar esteroides legales cuyo uso no esté prohibido por la normativa. Aunque pueda resultar exagerado, aquí podemos incluir vitaminas, enzimas, preparados para aumentar el potencial energético y adaptógenos. En algunos casos, los deportistas utilizan sustancias que estimulan la actividad reológica y el funcionamiento del sistema circulatorio.
Esta duración permite que los compuestos trabajen en sinergia, asegurando ganancias sostenidas, una mejora significativa en el volumen muscular y fuerza. Si bien los ciclos más cortos son efectivos para quienes buscan resultados rápidos, este ciclo avanzado está diseñado para quienes desean un impacto más profundo y especializado. Puesto que los esteroides se pueden inyectar, las personas que los consumen pueden correr el riesgo de contraer enfermedades que se trasmiten a través de agujas sucias y/o compartidas con otras personas. Entre ellas, se incluyen la infección por el virus de la inmunodeficiencia humana (VIH)/SIDA y la hepatitis, una enfermedad hepática (del hígado) grave.
Además, estos esteroides no deben utilizarse de forma recreativa o sin una necesidad médica legítima. La farmacología deportiva es un área en la que se ha acumulado un gran número de esteroides falsificados. Elegir un fabricante de marca reputada le protegerá de posibles efectos secundarios y hará que el programa sea lo más eficaz posible.El tipo de programa también es de gran importancia. Normalmente, un atleta necesita varios agentes a la vez para los ciclos anabólicos.
Deben tenerse en cuenta factores como el nivel de experiencia, los resultados deseados y la tolerancia al compuesto. Consultar con un profesional médico o un usuario experimentado de esteroides puede proporcionar una guía valiosa. Y puesto que en todos los niveles deportivos, desde la escuela secundaria hasta el nivel profesional, se hacen controles antidopaje, hay muchas probabilidades de detectar a las personas que consumen esteroides. Si ese fuera el caso, pasarían mucha vergüenza y podrían ser penalizadas en sus deportes. Copyright © 2025 Leaf Group Ltd El uso de este sitio net constituye la aceptación de los Términos y Condicionesy Política de Privacidad.
Si bien la inyección de Deca Durabolin generalmente se tolera bien, puede haber efectos secundarios potenciales asociados con el proceso de inyección en sí. Estos pueden incluir dolor o malestar en el lugar de la inyección, hinchazón o formación de abscesos. Si se presentan síntomas inusuales, es importante consultar a un médico. Los esteroides anabólicos incrementan la masa muscular y fortalecen la capacidad física. PharmaLabs NO sugiere usar ciclos de esteroides anabólicos si aún no has llegado a tu límite de manera pure, tampoco si estás recién iniciándote en esta disciplina. Toma esta decisión con mucha responsabilidad e infórmate antes de adquirir tus productos. El Ciclo Volumen Avanzado ha sido creado para usuarios experimentados que buscan un desarrollo muscular intenso y prolongado en un periodo de 11 semanas.
El uso de Deca Durabolin puede afectar la salud cardiovascular al afectar los niveles de colesterol. Puede disminuir los niveles de colesterol beneficioso (HDL) mientras aumenta el colesterol dañino (LDL), lo que puede conducir a un mayor riesgo de problemas cardiovasculares. Para las usuarias, Deca Durabolin conlleva el riesgo de virilización, que incluye el desarrollo de características masculinas como voz grave, crecimiento de vello facial y agrandamiento del clítoris. Deca Durabolin puede causar retención de agua, lo que resulta en hinchazón y aumento de la presión arterial.
El uso de esteroides farmacológicos también está muy extendido entre los aficionados. Se trata de una solución excelente en caso de que el cuerpo haya alcanzado el límite de su rendimiento fisiológico y ya no pueda crecer tan rápido como antes. También ofrecemos la oportunidad de consultar con un especialista para decidir mejor qué esteroide anabólico comprar. Los anabolizantes son compuestos químicos capaces de incrementar los procesos anabólicos en el organismo, es decir las reacciones para sintetizar tejidos corporales. Además, los aficionados a los ejercicios hacen su pedido al proveedor que es a veces el dueño del gimnasio o un intermediario, que nadie sabe dónde consigue los esteroides o suplementos. Dijo que investigaría a los entrenadores de béisbol que estaban suministrándoles sustancias prohibidas que le podrían causar la muerte a los jugadores de ese deporte.
References:
https://www.ajirazetu.tz/employer/dosis-de-clen/
El abuso de esteroides es particularmente riesgoso para los adolescentes, ya que obliga al cuerpo rápidamente a la edad adulta y hace que los huesos dejen de crecer de forma permanente. El hecho es que no tiene sentido de no permitir que los esteroides anabólicos legales para uso profesional y uso personal . Que cubre los ojos y pretender que no está sucediendo no es una opción aceptable más. Con profesionales médicos y expertos en salud que supervisan el uso de sustancias dopantes, podríamos asegurar el uso esteroide seguro e igual. La testosterona y los esteroides también afectan el deseo sexual y el sistema reproductivo, lo que puede plantear riesgos potenciales en los casos de abuso de esteroides. RAD a hundred and forty debería tomarse idealmente una vez que una persona ya haya completado un ciclo de SARM, para que su cuerpo esté más preparado y sea capaz de tolerar efectos secundarios más fuertes.
Muchos los toman con la esperanza de alcanzar beneficios para la salud, desde perder peso hasta ganar músculo. De otros países como México y los países europeos que no se requiera una receta para la compra de esteroides. Con menos frecuencia los esteroides que se encuentran en el mercado ilícito se desvían de fuentes legítimas o producidos en laboratorios clandestinos. Los esteroides también se utilizan en la práctica veterinaria para promover la eficiencia de la alimentación, y la mejora de la ganancia de peso, el vigor y la capa del pelo.
Estas consecuencias varían según el país y las leyes vigentes, pero generalmente incluyen sanciones económicas y penas de cárcel. El consumo de esteroides en el ámbito deportivo en España es un tema de gran relevancia en el marco authorized. La normativa española establece de manera clara las prohibiciones relacionadas con la utilización de sustancias dopantes en el deporte, buscando preservar la integridad y la equidad en las competiciones. En conclusión, es necesario respetar las regulaciones y prohibiciones en el uso de esteroides para evitar problemas legales y proteger la salud propia y de terceros. Ante cualquier duda sobre la legalidad de estas sustancias, es recomendable buscar asesoramiento de profesionales competentes en la materia. La alimentación juega un papel crucial en el rendimiento deportivo y la construcción de músculos. Una dieta balanceada y nutritiva, rica en proteínas magras, carbohidratos complejos, grasas saludables y una variedad de frutas y verduras, puede brindar los nutrientes necesarios para el crecimiento muscular y la recuperación después del entrenamiento.
Pronto empezarás a recibir en tu buzón la información médica más reciente de Mayo Clinic que solicitaste. Afortunadamente, para aquellos que no quieren poner en riesgo su salud, existen alternativas. Los productos de CrazyBulk son, con mucho, las mejores alternativas naturales que existen.
ESTEROIDES son ilegales y la mayoría de ellos se consideran una droga de Clase C que significa que, sin la prescripción de un médico por un problema médico, es contra la ley a poseer, vender o distribuir esteroides anabólicos. Algunas personas están tomando suplementos dietéticos que actúan como precursores de esteroides sin ningún conocimiento de los peligros asociados con su abuso. Estos suplementos se venden en tiendas de alimentos saludables, a través de Web, ya través de pedidos por correo. Estos suplementos tienen las mismas consecuencias médicas como esteroides y ellos también son ilegales. Estos medicamentos son utilizados para mejorar el rendimiento físico, pero muchos de ellos están prohibidos por la autoridad sanitaria. Creen que su uso se expande de la mano de un creciente mercado ilegal, que los trafica en gimnasios y otros puntos de venta. En la década de 1990, period común que los ciclistas profesionales utilizaran eritropoyetina.
El uso de esteroides en España es un fenómeno en crecimiento, impulsado por la búsqueda de mejoras en el rendimiento físico. Sin embargo, es crucial tener en cuenta las implicaciones legales y los riesgos para la salud asociados con su uso. Optar por alternativas naturales y seguir un enfoque responsable hacia el fitness puede conducir a resultados sostenibles y saludables, evitando las consecuencias negativas del abuso de esteroides. Aunque los esteroides anabólicos están prohibidos para la venta y distribución sin receta médica, su uso no está penalizado si se emplean para fines personales. Esto ha llevado a una amplia variedad de canales de distribución, tanto legales como ilegales.
En muchos países, la venta y distribución de anabolizantes sin receta médica está prohibida. Esto se debe a que su uso puede tener efectos secundarios graves, como daños en el hígado, alteraciones hormonales y problemas cardiovasculares. Además, el uso indebido de estas sustancias puede llevar a la dependencia y al abuso. Mantener los esteroides anabólicos medios ilegales dejar que los jugadores individuales los utilizan para su propia discreción. Debido a que un atleta no es un profesional de la medicina, esto crea un riesgo de efectos adversos para la salud, el abuso y sobredosis. Muchos atletas toman esteroides anabólicos en dosis mucho más altas que las que recetan los proveedores de atención médica por motivos médicos. Las rupturas de tendones en levantadores de pesas han sido asociadas con el consumo de esteroides, aunque no existe evidencia alguna que sugiera que la incidencia es mayor en consumidores de esteroides anabólicos en comparación con deportistas que no los utilizan.
Es basic que aquellos interesados en obtener esteroides comprendan las implicaciones legales que esto conlleva. Es importante verificar la normativa local antes de considerar la compra de esteroides. El uso indebido de estas sustancias puede acarrear consecuencias legales graves, por lo que es basic informarse adecuadamente sobre las leyes que regulan su comercialización y consumo en cada jurisdicción. Es essential entender las normativas legales sobre esteroides en cada país para evitar posibles consecuencias legales y proteger la salud. Si estás considerando utilizar este tipo de sustancias, es recomendable consultar con un médico especializado para obtener una prescripción adecuada y seguir las indicaciones correspondientes. Es importante tener en cuenta las regulaciones establecidas para garantizar su uso seguro y legal.
Una ingesta adecuada de proteínas es esencial para el crecimiento y el mantenimiento de los músculos. Pero no es necesaria una dieta especialmente rica en proteínas, ya que se pueden cubrir estas necesidades con una dieta diaria equilibrada. Los suplementos de proteínas, las barritas con alta cantidad de proteínas y las preparaciones de aminoácidos pueden ser los productos nutricionales deportivos que más se venden. Según informa la Policía Nacional, los investigadores calculan que sólo el pasado año esta red habría importado cerca de una tonelada de anabolizantes. “Cada semana aparece un producto nuevo. Por ejemplo tenemos el Rad140, pero el a hundred and fifty ya ha aparecido, que desarrolla más la molécula”.
El ácido D-aspártico es un regulador de aminoácidos que fabrica la hormona luteinizante, la misma hormona que potencia la producción de testosterona. Y como todos los fisicoculturistas saben, la testosterona es el martillo que conduce al tamaño, la fuerza, la energía, la potencia y el rendimiento muscular. Y además de promover el crecimiento de los músculos, incrementan el desarrollo de las características sexuales masculinas. Estas son sustancias sintéticas vinculadas a las hormonas sexuales masculinas, como la testosterona. No olvides que los enfoques de reducción del riesgo, al final, van dirigidos a personas consumidoras que pretendemos mejorar la autogestión de nuestros consumos para disminuir la probabilidad de aparición de problemas asociados (emocionales, sociales y sanitarios). Los más asiduos son los hombres, aunque algunas mujeres, sobre todo jóvenes, también optan por ellos para moldear su cuerpo, reduciendo la grasa corporal.
Los esteroides se consumen en forma de “ciclos”, es decir, durante un periodo de tiempo se toman varias dosis, descansando en ciertos momentos; cuando se acaba ese ciclo, se vuelve a iniciar el proceso. Durante esos ciclos es habitual “combinar”, tomando dos o más esteroides distintos; dos orales, uno oral y otro inyectable… Es lo que se conoce como apilamiento (stacking). Es difícil estimar la prevalencia del uso indebido de esteroides en Estados Unidos porque muchas encuestas nacionales que preguntan sobre el consumo de drogas no incluyen preguntas sobre los esteroides. Sin embargo, se dispone de datos sobre el uso indebido de esteroides entre los jóvenes estudiantes a partir de la encuesta Monitoring the Future, que cuenta con el apoyo del NIDA. Todas las pólizas de seguros y los planes de beneficios de grupo contienen exclusiones y limitaciones. Para conocer la disponibilidad, los costos y detalles completos de la cobertura, comunícate con un agente autorizado o con un representante de ventas de Cigna. No hay que olvidarse que en Web se pueden comprar kits de pruebas de esteroides completamente legales.
Si estás considerando utilizar anabolizantes, es importante que entiendas las implicaciones legales que esto conlleva, además de los riesgos para tu salud. La adquisición de esteroides de forma ilegal puede acarrear serias implicaciones legales para aquellos que decidan adentrarse en este camino. Las leyes vigentes en la mayoría de los países establecen duras penas para quienes adquieren sustancias prohibidas, incluyendo multas cuantiosas y posibles penas de prisión. Los deportistas pueden tomar esteroides durante un determinado periodo de tiempo, detener la toma y empezar de nuevo varias veces en un año. Con frecuencia consumen varios esteroides al mismo tiempo (una práctica denominada programa de apilamiento) y los toman por diferentes vías (oral, inyectada o a través de parches).
References:
Oral steroid cycle (https://ariaqa.com/employer/efectos-secundarios-del-clembuterol/)
El estanozolol también posee propiedades anticoagulantes, por lo que es útil en el tratamiento de otras enfermedades. Con el tiempo, estos registros detallados de tu progreso pueden darte una thought más tangible de lo lejos que has llegado, y lo cerca que estás de lograr tus metas. Estas son nuestras mejores selecciones de aplicaciones de acondicionamiento físico. Planificar y grabar tus entrenamientos y objetivos personales con una aplicación puede ser una manera rápida y fácil de asegurarte de que vas por buen camino. Lee los comentarios sobre ellos para asegurarte de que tienen éxito comprobado y los honorarios razonables para tu presupuesto, de modo que puedas seguir adelante incluso cuando tengas ganas de darte por vencido.
De todas formas, es muy útil para reducir la inflamación y para aliviar cuadros artríticos, trastornos de piel, sangre, riñón, intestinos y tiroides, entre otros. Por ejemplo, la artritis reumatoide afecta al 0,5 % de la población de todo el mundo, mientras que el asma se presenta en casi el four,5 % de los habitantes de los países de alto ingreso. Los tipos de corticoides son de gran ayuda en estos y muchos más cuadros clínicos, pues tienen efectos antiinflamatorios e inmunosupresores muy efectivos.
Por lo tanto, nuestra tienda online es un lugar más adecuado donde cada atleta adulto puede comprar esteroides en España para sus fines deportivos. El consumo de tales esteroides en pastillas, inyectables o crema, de forma mantenida en el tiempo, también impacta en la salud psychological. De la misma manera, quienes consumieron esteroides anabólicos durante más de 10 años evidenciaron una clara dependencia a estas sustancias. La dimetilamilamina se ha encontrado en numerosos suplementos de desarrollo muscular y pérdida de peso, pero no es segura.
Uno de los efectos secundarios más graves del uso de anabolizantes es el daño en el hígado. El abuso de estas sustancias puede provocar enfermedades hepáticas graves, como la hepatitis y la cirrosis. Los síntomas de daño hepático pueden incluir náuseas, dolor abdominal, fatiga, pérdida de apetito y coloración amarillenta de la piel y los ojos. Si experimentas alguno de estos síntomas, es importante buscar atención médica de inmediato.
Además, la mayoría de estos productos son ilegales y su compra y venta están prohibidas en muchos países. Si se resolve utilizar esteroides anabólicos, es recomendable buscar asesoramiento médico y adquirirlos de fuentes confiables y legales. En cualquier caso, es importante recordar que el camino hacia la mejora física y deportiva debe ser siempre saludable y seguro. Los esteroides son los suplementos o fármacos más eficaces que ayudan a las personas a mejorar su rendimiento basic con mayor fuerza y su físico common con menos grasas corporales y mayor masa muscular.
Las alergias, el asma y algunas afecciones cutáneas (entre otras enfermedades) pueden tratarse con esteroides. La trembolona es un esteroide para aumentar tu fuerza y masa muscular, tiene resultados increíbles pero con riesgo de tener efectos secundarios que pueden dañar tu salud. Si olvida tomar dosis de su anticonceptivo oral, es posible que no esté protegida contra el embarazo.
Su potencia es del % respecto a la de la prednisona, pero es mucho más fuerte que otros de los corticoides ya citados. Por ejemplo, 7,5 miligramos de deflazacort son equivalentes a 25 miligramos de cortisona y 20 de hidrocortisona. Tiene un índice terapéutico alto, aunque también reporta ciertos efectos secundarios que no se pueden obviar.
Los esteroides anabólicos suelen presentarse en forma oral, que consiste en píldoras o comprimidos, e inyectable, que consiste en inyecciones. Sin embargo, existen otras formas de esteroides, como la crema, el inhalador, las gotas y el spray. La información disponible en este sitio no debe utilizarse como sustituto de atención médica o de la asesoría de un profesional médico. Las contraindicaciones y efectos secundarios de los esteroides quedan explícitos en la expectativa de vida de estos deportistas. Recurrir a la estrategia de un ciclo de esteroides para lograr esculpir el cuerpo, claramente no es lo mejor en términos de salud. En este momento se le dio uso como tratamiento para personas con testosterona baja, sobre todo en adultos mayores. Un dato curioso en este momento de la historia, es que los esteroides eran vendidos en las farmacias sin receta médica.
Los síntomas incluyen tener depresión, estar extremadamente cansado y no tener deseos de comer. Sin embargo, es elementary recordar que los esteroides no están exentos de riesgos, por lo que su uso debe ser cuidadosamente evaluado en cada caso. Los profesionales de la salud deben informar a los pacientes sobre los posibles efectos secundarios y supervisar de cerca su respuesta al tratamiento para minimizar cualquier complicación. Testo-Max es un suplemento seguro y bien tolerado para la mayoría de las personas. Sin embargo, se recomienda consultar con un médico antes de comenzar cualquier suplemento, especialmente si tiene alguna condición médica preexistente o toma medicamentos. Decaduro es un suplemento seguro y bien tolerado para la mayoría de las personas.
Desde entonces, los esteroides han sido objeto de controversia debido a su uso ilegal en el deporte y a los efectos secundarios negativos que pueden tener en la salud. A pesar de esto, algunos atletas siguen utilizando esteroides para mejorar su rendimiento físico. Esto implica tomar múltiples dosis de esteroides durante un periodo de tiempo específico, parar durante un tiempo y volver a empezar. Este esteroide es muy popular entre los atletas y culturistas que buscan aumentar la masa muscular y la fuerza sin los efectos secundarios de otros esteroides. El Anavar se toma en forma de pastillas y es conocido por sus efectos secundarios mínimos.
Todos los productos que encontrará en nuestra tienda en línea son auténticos y están provistos de códigos de verificación únicos para confirmar su originalidad. Guarda mi nombre, correo electrónico y net en este navegador para la próxima vez que comente. En muchas ocasiones el mal uso es responsable de la mala fama de estos medicamentos. En las técnicas intervencionistas que realizamos en las Unidades del dolor solemos recurrir muy frecuentemente a los corticoides como la Dexametasona (Fortecortín, Inzitán), Betametasona (Celestone Cronodose) o la Triamcinolona (Trigón depot). Podrás entender mejor el proceso de la inflamación y como actúan los fármacos antiinflamatorios viendo el siguiente vídeo.
Existen distintos tipos de esteroides, aunque todos provocan efectos similares. Los medicamentos corticoides son sustancias químicas con efectos muy importantes en todas las funciones del organismo. Los antiinflamatorios esteroideos, vienen en diferentes formatos, desde pastillas o píldoras, hasta inhaladores, y cremas. Los profesionales de la salud tienen el papel crucial de educar a los pacientes sobre el uso adecuado de los esteroides y prevenir los posibles efectos adversos.
References:
https://careerconnect.mmu.edu.my/employer/clenbuterol-antes-y-despues/
Como se mencionó anteriormente, Deca aumentará su conteo de glóbulos rojos y el suministro de sangre oxigenada de su cuerpo. Esto es capaz de mejorar sus niveles generales de resistencia ya que sus músculos no se fatigan fácilmente debido a los efectos del aumento de ácido láctico durante el entrenamiento y el levantamiento de objetos pesados. Un ciclo de Deca seguro para usuarios masculinos puede variar de 8 a 12 semanas, mientras que a las usuarias se les recomienda ejecutar un ciclo de Deca que no exceda las 8 semanas. Cuando se trata de un plan de dosificación, la dosis semanal recomendada de Deca para culturistas femeninas es de 50 mg. Por otro lado, los culturistas masculinos pueden ejecutar un ciclo Deca de eight a 12 semanas con una dosis semanal tan baja como 200 mg y tan alta como 1,000 mg. Deca Durabolin puede usarse en un ciclo independiente o puede combinarse con otros esteroides.
El tratamiento con glucocorticoides debe mantenerse durante varias semanas a meses después de suspenderse el mitotano. La metopirona es un derivado piridínico que empezó a utilizarse para el diagnóstico de la enfermedad de Cushing. Actúa inhibiendo la enzima CYP11B1 (11-betahidroxilasa), causal del paso de 11-desoxicortisol a cortisol.
El que se produzcan efectos secundarios al utilizar esteroides depende de los conocimientos del usuario, el ciclo planificado y los factores genéticos. Los posibles efectos secundarios a largo plazo incluyen ginecomastia, pérdida de cabello, disminución de la voz, problemas de erección y daño hepático (cuando se usan dosis masivas de esteroides orales sin suplementos para el hígado). Apilar múltiples esteroides cuando es un novato va a confundir no solo sus resultados, sino también sus efectos secundarios y los pasos que debe seguir en la terapia posterior al ciclo. Mantenerlo simple para su primer ciclo de esteroides es best, y la testosterona es la mejor manera de hacerlo. El mayor riesgo de enfermedad hepática cuando se trata de esteroides proviene de los que se toman por vía oral debido a los métodos más lentos para limpiar el hígado.
Aunque Deca Durabolin tiene un índice anabólico de a hundred twenty five, relativamente bajo, continúa siendo un potente generador de masa muscular, ofreciendo también ganancias en energía y fuerza. Aunque el Deca Durabolin (también conocido como nadrolona) es uno de los anabolicos más leves y con menos efectos secundarios, muchos fisicoculturistas optan por utilizar deca en sus ciclos. Ambos autores evaluaron, de forma independiente, la calidad de la ocultación de la asignación. Un autor extrajo, de forma independiente, los datos sobre el número de participantes asignados al azar, los números perdidos durante el seguimiento, la duración del seguimiento, las tasas de mortalidad, la discapacidad, las infecciones y las hemorragias gastrointestinales, y esto fue comprobado por el otro autor. En ausencia de un metanálisis, se considera que la mayor parte del peso debe recaer en el resultado del ensayo más grande.
El KC es más efectivo que otros fármacos adrenolíticos porque inhibe también la secreción de ACTH15, aunque este efecto puede ser revertido parcialmente por el incremento compensador de la ACTH hipofisaria (fenómeno escape). En este sentido, a pesar de haberse demostrado la elevación basal y la respuesta al CRH de ACTH en los tratamientos prolongados, para la mayoría de los autores esto no representa sino la necesidad de monitorizar el tratamiento (cortisol plasmático, libre urinario y ACTH) para ajustar su dosificación. Al igual que con la metopirona hay que tener presente la posibilidad de reacción cruzada con los distintos ensayos comerciales de cortisol (progesterona, 17-hidroxiprogesterona y 11-desoxicortisol) para valorar correctamente cualquier decisión en el ajuste de la dosis. El valproato sódico es un agonista gabaérgico que disminuye la secreción de ACTH mediante la inhibición del CRF. A la dosis de 600–1.200 mg/día se ha descrito remisión clínica en algunos pacientes con enfermedad de Cushing y síndrome de Nelson. Al igual que con la ciproheptadina, las perspectivas de utilidad no se han confirmado en los estudios a largo plazo y en la actualidad no representa sino una referencia histórica. Los cuatro años siguientes, su cuerpo fue incapaz de producir testosterona y estuvo sumido en una depresión y una absoluta falta de deseo sexual.
Los usuarios intermedios buscarán usar Deca-Durabolin con al menos otros dos compuestos, con Dianabol y Cipionato de testosterona siendo opciones populares. Mientras tanto, para aquellos de ustedes que buscan una recuperación de la testosterona (tratamiento de baja testosterona) y antiestrógenos, aquí está mi lista de productos eficaces que siento que funcionan. Los usuarios intermedios considerarán el uso de Deca-Durabolin con al menos otros dos compuestos, siendo Dianabol y Cipionato de testosterona las opciones populares. Deca-Durabolin, basado en el esteroide nandrolona, es uno de los esteroides más antiguos que ha resistido el paso del tiempo y sigue siendo uno de los favoritos hasta el día de hoy. Pero sobre todo, estarás consiguiendo una mejora en tu salud, que es mucho más importante que la estética. Por si te interesa, aqui te dejo este publish donde se habla sobre otra sustancia llamada Boldenona.
La mayoría de las ratas de gimnasio y los usuarios activos de esteroides habrían oído hablar de Deca Dick. Este problema ocurre cuando ejecuta un extenso ciclo deca y el esteroide restringe la cantidad de óxido nítrico en su cuerpo. Los culturistas usan Deca porque es un esteroide de éster largo de acción lenta que proporciona y mantiene las ganancias del culturismo incluso fuera de temporada.
En la tabla 1 se resumen las características de los preparados de glucocorticoides más usados en la clínica. No se incluyen los glucocorticoides inhalados, ya que el efecto hiperglucemiante que producen, si existe, es clínicamente poco relevante22. El conocimiento de estas características, además de esencial para seleccionar el preparado y la dosificación más adecuados para la indicación terapéutica, es importante para la predicción de los potenciales efectos secundarios como la hiperglucemia. De ello da idea la escasa bibliografía existente sobre la prevalencia y la fisiopatología, pero sobre todo en lo que hace referencia al diagnóstico y el tratamiento. Además, en estos aspectos la información disponible proviene fundamentalmente de artículos de opinión en el contexto de revisiones del manejo de la hiperglucemia en la hospitalización16–19 y de dos revisiones recientes sobre la hiperglucemia inducida por glucocorticoides20,21.
Dianabol a veces es tomado por principiantes; sin embargo, esto no se recomienda debido a sus fuertes efectos cardiovasculares y hepáticos. Por lo tanto, es más adecuado para intermedios que ya han tomado un esteroide más suave previamente, como la testosterona. Sin embargo, los efectos hepáticos de Anavar son relativamente leves en comparación con otros esteroides orales; por lo tanto, este efecto secundario no es típicamente preocupante para los culturistas. La testosterona también sesgará las proporciones de colesterol HDL y LDL, causando una posible hipertensión. Sin embargo, este efecto negativo sobre la presión arterial es leve en comparación con los AAS más duros; con la testosterona tal vez sea el esteroide más amigable para el sistema cardiovascular. El ciclo anterior es comúnmente utilizado por principiantes que buscan agregar cantidades sustanciales de músculo y fuerza.
El Sustanon es una mezcla de cuatro tipos diferentes de testosterona, lo que significa que es una forma más potente de testosterona en comparación con otros tipos de esteroides de testosterona. Por otro lado, la Deca (decanoato de nandrolona) es un esteroide anabólico que se utiliza para aumentar la masa muscular y mejorar la fuerza. Si quiere minimizar el uso de otros esteroides cuando esté tomando Deca, se suele utilizar una dosis baja de testosterona. Tras más de 60 años de experiencia, no se ha clarificado totalmente en qué medida el riesgo de los principales efectos adversos (EA) derivados del uso de GC depende del régimen de tratamiento, qué probabilidad de EA presenta el uso de GC y si este riesgo se mantiene a largo plazo a pesar de su suspensión.
En el mejor de los casos, se trata de medicamentos de farmacia cuya venta sin receta está prohibida y, en el peor, de sustancias fabricadas en laboratorios clandestinos que se comercializan en webs con apariencia de farmacias legales. Si usted es menor de 20 años, existe la probabilidad de que su sistema endocrino no esté completamente desarrollado. La interferencia en el sistema hormonal a esta edad aumenta significativamente las posibilidades de efectos secundarios a largo plazo. En muchos foros, se aconseja a un principiante que tome 10 o 12 semanas de testosterona a 500mg/semana para el primer ciclo. Dado que los efectos de la testosterona sólo se hacen totalmente visibles en la 6ª semana, el ciclo de 10 semanas es demasiado corto. Un ciclo de 12 semanas tiene mucho más sentido, pero aún así tendrá que comprar 3 frascos de testosterona. Afortunadamente, CADA uno de estos efectos secundarios se puede prevenir planeando ciclos razonables y comprando sustancias preventivas de antemano, para que pueda tomarlas tan pronto como las necesite.
El uso de glucocorticoides a dosis altas podría alargar el tiempo de ingreso en estos pacientes. Analizar si existe asociación entre el uso de glucocorticoides a dosis altas y la evolución de la SAFI (saturación/fracción inspirada de oxígeno) o el tiempo hasta el alta, en pacientes hospitalizados por COVID-19. Me quedaban pelos en las manos antes del comienzo del ciclo todos los días mientras me lavaba el pelo.
References:
will steroids burn fat (https://careervault.horizonbeam.com/employer/clenbuterol-ciclo)
La grasa corporal disminuye mientras que la hipertrofia muscular aumenta, así como la definición muscular y la vascularidad. El Enantato de testosterona es un éster de la hormona masculina testosterona, ampliamente utilizado tanto en medicina como en el ámbito del culturismo. Este compuesto se utiliza principalmente para tratar trastornos relacionados con niveles bajos de testosterona, pero su popularidad también ha crecido en el deporte debido a sus propiedades anabólicas. Loopy Bulk ofrece ofertas generosas, lo que permite a las mujeres ahorrar dinero, en comparación con la compra de esteroides caros como Primobolan y Anavar en el mercado negro (que puede costar cientos de dólares por ciclo). Este es un ciclo de corte típico utilizado por las modelos de bikini o culturistas que desean quemar grasa.
Varios meses (4-12) después de usar Anadrol u otros esteroides, solemos ver que los testículos de los usuarios vuelven a su tamaño regular. Sin embargo, si decides tomar zumo de pomelo con Anadrol, debes tener cuidado con la sobredosis, ya que 50 mg de Anadrol pueden convertirse efectivamente en a hundred mg debido a la inhibición de CYP3A4. La testosterona es principalmente un esteroide inyectable, mientras que Anadrol 50 se toma por vía oral. Las dosis típicas de Dianabol van de 30 a 50 mg al día, mientras que Anadrol requiere el doble ( mg) para obtener resultados similares. En nuestra experiencia, son los dos mejores esteroides para ganar masa rápidamente. Debido al posible riesgo de que el Anadrol contenga sustancias peligrosas o simplemente sea una píldora placebo, se aconseja a la gente que solo confíe en fuentes del mercado negro que puedan ser verificadas por alguien de confianza.
No quieres un cuerpo súper grande, totalmente marcado con niveles de grasa corporal insanos, para que todo el mundo te admire y vean lo “grandioso” que eres…. Los esteroides provocan retención de agua, lo que puede resultar en presión arterial alta. Alguien que usa esteroides, no necesariamente se va a ver como una montaña llena de músculos, ya que para verse así se requiere de años y de una cantidad enorme de drogas. Por ejemplo, en la mayoría de estos estudios, la dosis de testosterona period de 600 mg a la semana, que es una dosis moderada.
Debido a que Anadrol no se convierte en DHT a través de la enzima 5-alfa reductasa, medicamentos como el finasteride son ineficaces para tratar la caída del cabello. Además, puede no ser beneficioso para un culturista reducir los niveles de DHT con estos medicamentos, ya que hemos observado reducciones en la fuerza y las ganancias musculares. Debido al efecto drástico de Anadrol sobre los niveles de colesterol HDL, la retención de agua y el recuento de glóbulos rojos, es un esteroide que tiene un efecto muy negativo sobre el corazón. Por eso se recomienda tomar un estimulador de testosterona antes y después de un ciclo de Winstrol, esto para ayudar a mantener tus niveles de testosterona saludables. Necesitas evitar esto, ya que los bajos niveles de testosterona tienen efectos negativos a corto y largo plaza, entre ellos, inhibe la producción de músculo.
La popularidad de Anavar se debe a sus propiedades suaves, que lo hacen tolerable tanto para hombres como para mujeres. Las mujeres que toman Anavar generalmente no experimentan efectos de virilización, aunque hay excepciones. Algunas mujeres que abusan del Anavar, tomando dosis altas durante períodos prolongados, pueden enfrentar masculinización.
Corticosteroides, como la prednisona, comúnmente tratan diversas afecciones, como asma, alergias y artritis. Estos esteroides naturales funcionan reduciendo la inflamación en el cuerpo y suprimiendo el sistema inmune. Esta publicación de weblog explorará los efectos de los esteroides antes y después de su uso y cómo abordar mejor cualquier problema potencial. Reduzca el consumo de azúcares refinados, postres, pasteles y otros alimentos ricos en carbohidratos. Uno de los factores más importantes para perder peso es reducir la ingesta de azúcar refinada y eliminar los carbohidratos altamente procesados, como pasteles, galletas y bollería. Es fácil comer en exceso este tipo de alimentos porque le dan a su cuerpo un rápido impulso de energía que lo mantiene lleno por períodos más prolongados.
Fue desarrollado originalmente en la década de 1950 con el propósito de mejorar el rendimiento deportivo de los atletas estadounidenses en los Juegos Olímpicos (1). El Dianabol, también conocido como metandrostenolona, es un esteroide anabólico sintético derivado de la testosterona. Por ultimo, para el manejo del dolor radicular es de gran importancia incorporar un programa de rehabilitación con el fin de coadyuvar y así mejorar la funcionalidad de los pacientes. El empleo de ITE es un recurso de gran utilidad, sin embargo el impacto que este procedimiento tiene sobre la funcionalidad, no está aún bien determinado, por lo que se requieren más estudios en este sentido. Igualmente se eliminaron del estudio a quienes no tuvieran la capacidad de responder al cuestionario o pudieran completar el estudio. En aquellos pacientes que presentan dolor de espalda por compresión radicular, la inyección peridural de esteroides es una herramienta de gran utilidad para mitigar el dolor. El abordaje del espacio se realiza por vía interlaminar, caudal o vía transforaminal (también llamado bloqueo selectivo de raíces nerviosas) (10).
A continuación se muestran varias fotos del antes y después del uso de Winstrol, que ofrecen a los usuarios potenciales una mejor comprensión de los efectos que este esteroide tiene sobre la composición corporal. La vascularización y las estrías también pueden volverse más pronunciadas debido a las cualidades diuréticas del Winstrol, reduciendo la retención de agua extracelular y, por lo tanto, secando los músculos. García Iruretagoyena advierte que “pese a que quienes siguen estos métodos están convencidos de maximizar los beneficios y reducir riesgos, no hay evidencia científica de su efectividad o seguridad”. Una comprensión completa de los beneficios y riesgos, así como una implementación correcta de ciclos y terapias post-ciclo, son fundamentales para garantizar una experiencia segura y efectiva.. El clenbuterol es posiblemente la mejor opción para las mujeres que se preocupan más por quemar grasa que por construir músculo.
En este momento es sumamente importante aumentar la producción endógena de testosterona a un nivel regular tan rápidamente como sea posible para que la pérdida de fuerza y masa muscular se minimice. Un ciclo de esteroides es un período estructurado en el que se utilizan esteroides anabólicos para alcanzar objetivos específicos, como el aumento de masa muscular o la mejora del rendimiento deportivo. Los esteroides anabólicos son compuestos sintéticos derivados de la testosterona, una hormona masculina. Están diseñados para promover el crecimiento muscular y mejorar el rendimiento físico.
Sin embargo, un PCT (terapia post-ciclo) sigue siendo necesario para ayudar a mantener las ganancias. Esto significa que desde tu última dosis hasta ese momento, todavía pueden quedar trazas en tu cuerpo que podrían hacerte fallar la prueba. Si dejas pasar más tiempo y terminas el ciclo 2,5 meses antes de la prueba, no tendrás problemas. No quieres condicionar tu cuerpo a necesitar dosis extremadamente altas de Anadrol para seguir viendo ganancias, lo cual será el caso si optas por un uso continuo de Anadrol. Además, no hay mucho beneficio en hacerlo, ya que las ganancias se estancarán porque tu cuerpo se adaptará a los esteroides. La testosterona es más adecuada para principiantes, ya que es menos tóxica para el cuerpo.
References:
https://karierainsports.gr/employer/clenbuterol-culturismo/
Gates of Olympus Super Scatter : Slot Online Resmi dengan Bonus Menarik dan Kemenangan Besar
I never thought about it that way—thanks for the insight!
This was exactly what I was looking for!
Phim sex clip sex Việt Nam
Well written and easy to understand. Keep it up!
Phim sex clip sex Việt Nam
I appreciate the detailed explanation, it helped a lot.
Ümraniye su kaçak tespiti Su kaçağı sadece maddi değil, aynı zamanda çevresel bir sorundur. https://biswabanglanews.com/?p=2100
Phim sex clip sex Việt Nam
Koşuyolu su kaçak tespiti Şişli su kaçağı tespiti: Şişli bölgesinde güvenilir su kaçağı tespit hizmetleri. https://elmercadodemipueblo.es/?p=213820
Üsküdar su kaçak tespiti Etiler’deki evimizdeki su kaçağını hemen tespit ettiler ve onardılar. Profesyonel hizmet. https://dobrapozycja.pl/domain/uskudartesisat.com/x0kJ61f00ec7d4288
Yayla su kaçak tespiti Ümraniye’de yaşadığımız su kaçağı sorununu bu ekip sayesinde çözdük. Hızlı ve etkili bir hizmet. https://fairknowledge.wiki/?p=47010
Çanta su kaçak tespiti Erken müdahale, onarım maliyetlerini önemli ölçüde düşürür. https://barauditoriump2.com/?p=192304
su kaçak tespiti İstanbul Sultangazi su kaçağı tespiti: Sultangazi’de su sızıntılarını anında tespit ediyoruz. https://barauditoriump2.com/?p=192302
Barbaros su kaçak tespiti Beyoğlu’ndaki binamızda tespit ettikleri su kaçağını hızlıca onardılar. Herkese öneririm. https://hygiene-premium.com/?p=3262
daf14s
Interesting perspective—thanks for making me think.
This is so helpful. Looking forward to your next post!
v3wfft
Awesome content as always!
oral meloxicam – celebrex 200mg sale buy flomax 0.4mg
Thanks for breaking this down so clearly.
Nişantaşı su kaçağı tespiti Teknolojik gelişmeler, su kaçağı tespitini daha kesin hale getiriyor. http://blakemountford.com/author/kacak/
Great post! I really enjoyed your perspective on this topic.
Thanks for sharing this! Very informative and easy to understand.
zr2r8l
This gave me a lot to think about. Appreciate the insight!
Wow, that’s what I was seeking for, what a stuff!
present here at this website, thanks admin of this site.
I’ve been looking for info like this—glad I found your blog.
маркетплейс аккаунтов заработок на аккаунтах
гарантия при продаже аккаунтов https://marketplace-akkauntov-top.ru/
покупка аккаунтов https://magazin-akkauntov-online.ru/
гарантия при продаже аккаунтов перепродажа аккаунтов
площадка для продажи аккаунтов маркетплейс аккаунтов соцсетей
Well-written and straight to the point. Keep up the good work!
перепродажа аккаунтов маркетплейс аккаунтов
маркетплейс аккаунтов биржа аккаунтов
Great read! I really enjoyed your perspective on this topic.
Sell accounts Account Purchase
Account market Social media account marketplace
Account Buying Platform Social media account marketplace
Accounts marketplace https://buyaccountsmarketplace.com/
Online Account Store Buy Account
Account Store Buy Account
Guaranteed Accounts Purchase Ready-Made Accounts
Sell Pre-made Account Account Sale
Account Trading Service Sell Pre-made Account
Secure Account Purchasing Platform Account Trading Platform
account selling service secure account purchasing platform
account selling service account buying service
marketplace for ready-made accounts secure account sales
buy and sell accounts account trading service
I do believe all the ideas youve presented for your post They are really convincing and will certainly work Nonetheless the posts are too short for novices May just you please lengthen them a little from subsequent time Thanks for the post
Your article helped me a lot, is there any more related content? Thanks!
3ggyao
sell accounts account selling service
account store account selling service
website for buying accounts sell account
Great insights! I really enjoyed how you explained this topic clearly and simply.
buy account account acquisition
This is so helpful. I’ve been looking for a post like this—thank you!
account marketplace buy and sell accounts
Well written and inspiring! Keep up the great work.
account acquisition secure account purchasing platform
account trading platform database of accounts for sale
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thx for sharing this! Realy useful) Pls continue, this will be great!
sell accounts account selling platform
account buying platform account selling service
account catalog social-accounts.org
guaranteed accounts account sale
Thanks for sharing! I learned something new today.
If some one wishes expert view about blogging afterward i
advise him/her to pay a quick visit this website,
Keep up the pleasant job.
Feel free to visit my homepage; nordvpn coupons inspiresensation
account buying platform account marketplace
profitable account sales website for selling accounts
I got this web site from my friend who told me concerning this web site and at the
moment this time I am browsing this site and reading very informative articles
or reviews at this time.
Visit my web-site … nordvpn coupons inspiresensation [http://92url.com/]
ready-made accounts for sale website for buying accounts
Dapatkan Kemenangan Luar Biasa di Wild Wildebeest Wins dan Nikmati Keindahan Alam Afrika
account catalog account purchase
Cari Tahu Slot Gacor Hari Ini dan Menangkan Jackpot Besar
guaranteed accounts account buying service
gaming account marketplace account market
Interesting perspective. It really made me think differently.
What a data of un-ambiguity and preserveness of valuable know-how about unexpected emotions.
Also visit my page … nordvpn coupons inspiresensation (http://da.gd/)
account trading sell pre-made account
buy pre-made account sell account
accounts for sale account buying platform
g6raa6
constantly i used to read smaller articles or reviews which
as well clear their motive, and that is also happening with this piece
of writing which I am reading at this time.
My site nordvpn Coupons inspiresensation (tinyurl.com)
Love this post! Especially the part about staying consistent—so true.
sigmaslot : Temukan Slot Gacor dengan Jackpot Menarik dan Keuntungan Besar
Temukan Fitur Terbaik di sigma slot dan Dapatkan Kemenangan Spektakuler
accounts marketplace gaming account marketplace
account exchange marketplace for ready-made accounts
online account store account catalog
account marketplace verified accounts for sale
Ataşehir Mahalleleri: Küçükyalı su kaçağı tespiti: Küçükyalı’da su kaçağı tespitinde hızlı sonuç. https://thenypr.com/2022/12/21/umraniye-petek-temizleme-faydalari/
Taşdelen su kaçak tespiti Her bina için özel kaçak tespit stratejileri gereklidir. https://www.haberim.istanbul/firma-rehberi/uskudar-su-tesisatcisi-43
https://t.me/s/flagman_official_777/154
https://t.me/s/flagman_official_777/50
https://t.me/s/flagman_official_777/153
nordvpn 350fairfax
I all the time used to read post in news papers but now
as I am a user of internet therefore from now I am using net for
articles or reviews, thanks to web.
Feel free to surf to my page … nord vpn coupon codes
https://t.me/s/flagman_official_777/47
https://t.me/s/flagman_official_777/104
https://t.me/s/flagman_official_777/76
secure account purchasing platform account marketplace
account market https://accounts-marketplace.xyz/