Use case:
Set up Keycloak for Authentication using SAML protocol in Wazuh.
Keycloak configuration:
- Create a new client with the protocol set to
saml:
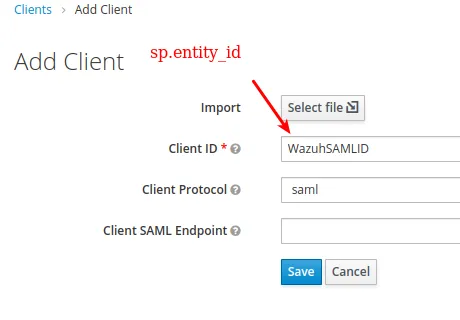
- Configure it to use the below options:
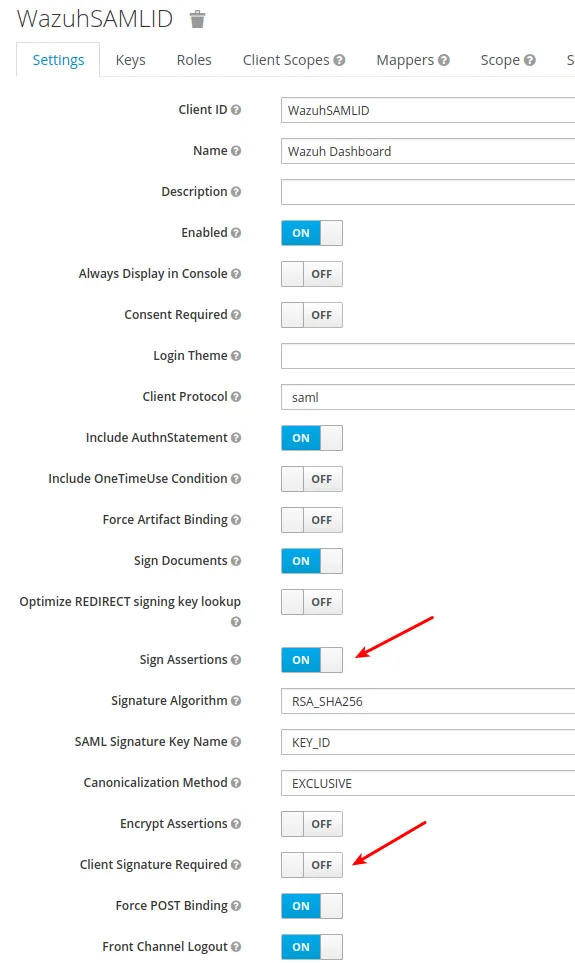
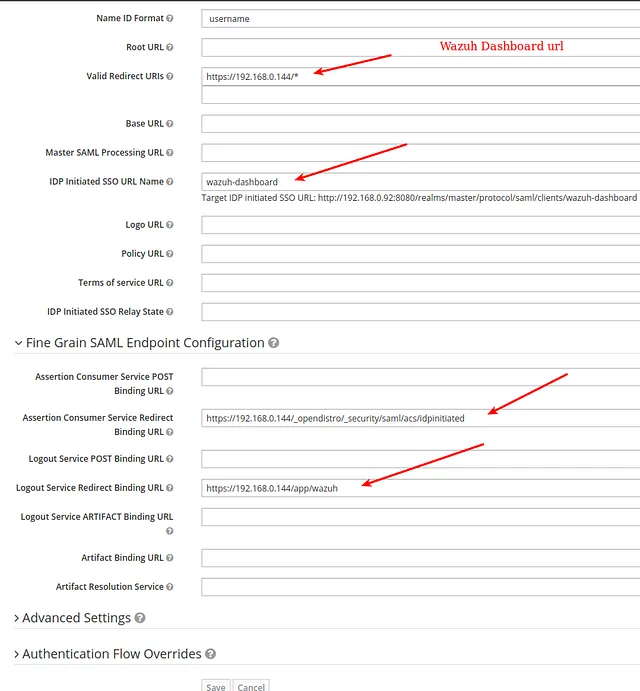
- Add a role naming it
Administrator:
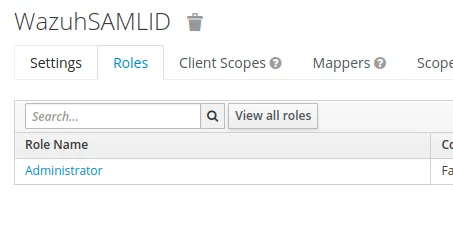
- Add a
Role listmapper:
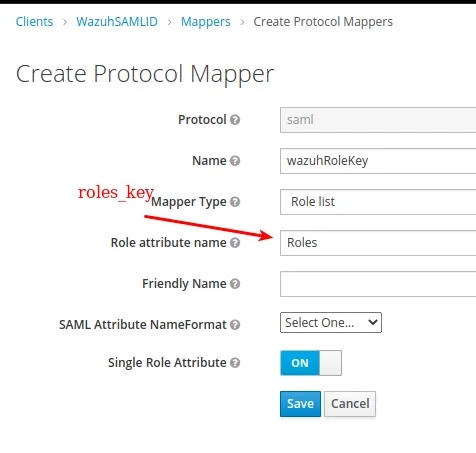
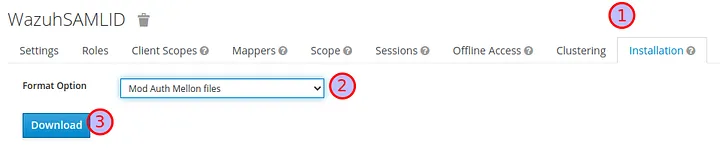
- Navigate to
Installationto generate the IDP and SP metadata files:
- The
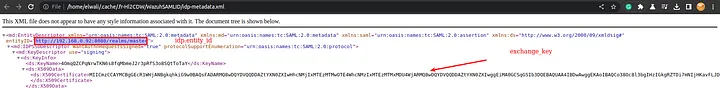
idp.entity_id&exchange_keysare included in theidp-metadata.xmlfile:
Wazuh indexer configuration:
- Place the content of
idp-metadata.xml&sp-metadata.xmlrespectively within /etc/wazuh-indexer/certs/idp_metadata.xml&/etc/wazuh-indexer/certs/sp_metadata.xmlsetting the ownership towazuh-indexer:
chown wazuh-indexer:wazuh-indexer /etc/wazuh-indexer/certs/sp_metadata.xml
chown wazuh-indexer:wazuh-indexer /etc/wazuh-indexer/certs/idp_metadata.xml- Configure the Wazuh indexer to use SAML by modifying
/usr/share/wazuh-indexer/plugins/opensearch-security/securityconfig/config.yml:
---
_meta:
type: "config"
config_version: 2
config:
dynamic:
http:
anonymous_auth_enabled: false
authc:
internal_auth:
order: 0
description: "HTTP basic authentication using the internal user database"
http_enabled: true
transport_enabled: true
http_authenticator:
type: basic
challenge: false
authentication_backend:
type: internal
saml_auth:
order: 1
description: "SAML provider"
http_enabled: true
transport_enabled: false
http_authenticator:
type: saml
challenge: true
config:
idp:
metadata_file: /etc/wazuh-indexer/certs/idp_metadata.xml
entity_id: http://192.168.0.92:8080/realms/master
sp:
entity_id: WazuhSAMLID
metadata_file: /etc/wazuh-indexer/certs/sp_metadata.xml
kibana_url: https://192.168.0.144/
roles_key: Roles
exchange_key: 'MIICmzCCAYMCBgGEcsVHGzANBgkqhkiG9w0BAQsFADARMQ8wDQYDVQQDDAZtYXN0ZXIwHhcNMjIxMTEzMjA1MjIyWhcNMzIxMTEzMjA1NDAyWjARMQ8wDQYDVQQDDAZtYXN0ZXIwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCPyuaYpgSOSiLFpj6u+TgGTEqspH/iBfBkHOwkEHlHXqkjLLZzzWMNxnzKxU/rjwpuxX6tNP0NQzzLe97Cq4hB9BLixcUJwzBdnlSDr3yI/kASSojqllPcrx94CTs6hMUC5RU6wNanAD5wu1OkI9DPUjN+0/3QCbVGDMjCzgT6u6PkRe9m9kg1Gp6MpdVmmfn8sVdp9HycbZM6gRCL0EU5DZubjHwO+QGmjZRCGmIAenuoTUDttCLC/TzzxeZ8dMHiUohiQYKtkavRLuhuqdCgHXASvE89BY9pv626TivUb3wx/LV9E4qeLb0LMmUSDtVH28M71cmaKClAOnZR0QUlAgMBAAEwDQYJKoZIhvcNAQELBQADggEBADi/ylzDpO1c8HODIIKPzFi6wsbGYyiGzHwZQTFvb6mXBUCpgoRk10RMshlyvWu27MtvYl3ot6ayPxwcJfCFf0KNladmPCR/3cKUvGEr/2AuXbXXoJSniua/LGTHp42D8B1xVOP5v8dvKPar50KK2BXhbvRZqbyemZ7MXb6P6hPZz2cYdjAcN48Zq4obNznUqd46hcHqDHtzVxIXlgpeA1B2QbUR3NdxsVWT8hcoh6xfNxh1RpNmWRGMsnHkFovJOvs1QCgrEjQzf1x+6m7JF+BNI7B3EZoTuft9TsiqppTBzUkTp6B0/FMkfy2OeLcUitag3JbPmkvY2rTAkGBrpnI='
authentication_backend:
type: noop
- Load the new security configuration:
export JAVA_HOME=/usr/share/wazuh-indexer/jdk && /usr/share/wazuh-indexer/plugins/opensearch-security/tools/securityadmin.sh -cd /usr/share/wazuh-indexer/plugins/opensearch-security/securityconfig/ -icl -key /etc/wazuh-indexer/certs/admin-key.pem -cert /etc/wazuh-indexer/certs/admin.pem -cacert /etc/wazuh-indexer/certs/root-ca.pem -h localhost -nhnvWazuh Dashboard configuration:
- Set the authentication to
samlby adding below to/etc/wazuh-dashboard/opensearch_dashboards.yml:
opensearch_security.auth.type: "saml"
server.xsrf.whitelist: ["/_opendistro/_security/saml/acs", "/_opendistro/_security/saml/acs/idpinitiated", "/_opendistro/_security/saml/logout"]As this might be solved in future versions you should perform the next step only if you are facing logout issue (https://forum.opensearch.org/t/saml-issue-on-logout/5617/14).
- Modify the logout endpoint in
/usr/share/wazuh-dashboard/plugins/securityDashboards/server/auth/types/saml/routes.jsby changing it from/auth/logoutto/logout:
this.router.get({
path: `/logout`,
validate: false
}, async (context, request, response) => {
try {
const authInfo = await this.securityClient.authinfo(request);
this.sessionStorageFactory.asScoped(request).clear(); // TODO: need a default logout page
const redirectUrl = authInfo.sso_logout_url || this.coreSetup.http.basePath.serverBasePath || '/';
return response.redirected({
headers: {
location: redirectUrl
}
});
} catch (error) {
context.security_plugin.logger.error(`SAML logout failed: ${error}`);
return response.badRequest();
}
});
}
}
exports.SamlAuthRoutes = SamlAuthRoutes;- Restart Wazuh dashboard:
systemctl restart wazuh-dashboard
DEMO:
I hope you find it useful 🙂

556 responses to “Wazuh & Keycloak using SAML”
buy oral stromectol – ivermectin 6mg over counter tegretol 400mg for sale
order accutane pill – order accutane generic zyvox without prescription
925535 322360I love your wordpress template, where did you download it from? 135047
… [Trackback]
[…] Read More here: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] Information on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] Find More Info here on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] Find More Info here on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] Here you can find 14316 additional Info on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
zithromax pill – how to buy tindamax buy nebivolol 5mg pill
… [Trackback]
[…] Read More Info here on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
buy omnacortil medication – azipro 500mg canada order prometrium 200mg for sale
… [Trackback]
[…] Read More on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] There you will find 52425 more Info on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
… [Trackback]
[…] Read More on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
buy neurontin pills for sale – anafranil tablet buy itraconazole online
… [Trackback]
[…] There you can find 5010 more Information on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
lasix 100mg oral – buy betnovate 20 gm online3 buy generic betamethasone
… [Trackback]
[…] There you can find 84504 more Info to that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
monodox drug – order acticlate for sale glipizide uk
order augmentin 625mg pill – augmentin 1000mg without prescription duloxetine 40mg cost
… [Trackback]
[…] Info to that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
order augmentin for sale – augmentin 1000mg us buy cymbalta 40mg online cheap
buy rybelsus 14mg generic – levitra 10mg ca cyproheptadine 4 mg price
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
generic tizanidine 2mg – hydroxychloroquine pills microzide 25mg pills
purchase sildenafil without prescription – usa pharmacy cialis tadalafil 5mg us
cost cialis 20mg – cialis 40mg buy generic viagra 100mg
… [Trackback]
[…] Find More here on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
Thanks for sharing. I read many of your blog posts, cool, your blog is very good. https://accounts.binance.com/el/register?ref=IQY5TET4
… [Trackback]
[…] Info on that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
cost cenforce – purchase cenforce online buy generic glycomet for sale
… [Trackback]
[…] Find More on to that Topic: opensourcesecurityblogs.com/wazuh-keycloak-using-saml/ […]
atorvastatin 10mg cost – purchase prinivil pill buy zestril tablets
Retire seus ganhos da [bingo](https://bingo-br.com) com facilidade. O processo de saque é simples e exige apenas que você forneça os dados do seu método de pagamento. A plataforma assegura a proteção dos seus fundos com criptografia avançada, garantindo que seu dinheiro esteja sempre seguro.
https://lioleo.edu.vn/christmas-section/4.png.php?id=coin-bet
https://lioleo.edu.vn/daily01-huyen/4.png.php?id=asiana-bet
Use For Weight Loss, Side Effects, Cost, And More
Health Conditions
Wegovy is used for weight loss and managing obesity in adults, particularly those who are overweight or have a significant
weight-related health risk.
Condition Spotlight: Obesity Management
Wegovy has been shown to effectively aid in weight management
and reduce the risk of cardiovascular events associated with obesity.
Wellness Topics: Emphasizing Lifestyle Changes
While Wegovy helps with weight loss, it should be combined with a healthy diet and regular
exercise for optimal results.
Product Reviews: Comparing Weight-Loss Aids
Wegovy is similar to diabetes medications like Ozempic and Victoza but is specifically designed for weight management.
It differs from Saxenda and phentermine in its mechanism of action.
Featured Programs
Placeholder for featured programs
Lifestyle Quizzes: Test Your Knowledge
Answer these questions to learn more about using Wegovy effectively:
1. What is the primary purpose of Wegovy?
2. Can Wegovy be used alongside other medications?
3. Are there specific foods you should avoid while on Wegovy?
Health News: Recent Insights
Recent studies have highlighted Wegovy’s efficacy in reducing cardiovascular risks, making it a
valuable tool for long-term weight management.
This Just In: New Updates
Placeholder for health news updates
Top Reads: Essential Articles
– “The Science Behind GLP-1 analogs”
– “Effectiveness of Wegovy in Different Populations”
– “Living a Healthy Lifestyle While Using Weight-Loss Medications”
Video Series: Visual Learning
Placeholder for video content
Find Your Bezzy Community
Join our community to share experiences and tips with others using Wegovy.
Follow Us on Social Media
Connect with us on social media platforms for updates, news, and more.
Wegovy Injection Overview
Wegovy is an injectable medication used for weight loss and managing obesity in adults.
It works by mimicking the effects of GLP-1, a hormone involved
in appetite regulation and glucose metabolism.
Wegovy Basics
Wegovy is a synthetic analog of GLP-1 designed to promote weight loss by regulating hunger and glucose levels.
How Does Wegovy Work?
By binding to receptors in the gastrointestinal tract, Wegovy slows gastric emptying, reducing appetite and
promoting fullness.
What Are Wegovy’s Side Effects?
Common side effects include nausea, constipation, headache,
and dizziness. Serious side effects may include increased
heart rate and palpitations.
Mild Side Effects
Mild side effects often subside within the first few weeks of use.
Serious Side Effects
Seek medical attention if you experience severe or persistent serious side effects.
Boxed Warning: Nausea
Nausea is a common side effect and may require dose
adjustment. Consult your healthcare provider for guidance.
What Does Wegovy Cost? Are Savings Available?
Wegovy can be costly, but savings may be available through insurance or manufacturer programs.
Always check with your pharmacy for pricing options.
What Does Wegovy Cost with Insurance?
Insurance coverage can significantly reduce out-of-pocket costs.
Verify your plan’s specifics to maximize savings.
Is Wegovy Used for Weight Loss and Weight Management?
Yes, Wegovy is specifically designed for weight loss and managing obesity
in adults.
Limitations of Use
Wegovy may not be suitable for everyone, particularly
those with certain health conditions or allergies
to its components.
Is Wegovy Used to Reduce Cardiovascular Risks?
Yes, studies suggest Wegovy may reduce the risk of cardiovascular
events associated with obesity.
Frequently Asked Questions
1. Is Wegovy similar to diabetes drugs? Yes,
but it’s specifically for weight loss.
2. Does Wegovy require refrigeration? No,
but store at room temperature unless otherwise instructed.
3. Is Wegovy a controlled substance? No, it is classified as a
biologic drug.
Wegovy vs. Ozempic
Wegovy and Ozempic are both GLP-1 analogs but differ in their
indications and dosage forms.
What is Wegovy’s Dosage?
Wegovy is typically administered once weekly via injection, with a dosage determined
by the healthcare provider based on individual needs.
Form and Strengths
Wegovy comes as a prefilled pen with a fixed dose, usually 10 mg.
Other strengths may be available upon prescription.
Recommended Dosages
The recommended starting dosage is typically one injection per week, adjusted by your doctor as needed.
Questions About Wegovy’s Dosage
Always consult your healthcare provider for specific instructions and adjustments.
What If I Miss a Dose?
Take the missed dose as soon as possible and adjust your next injection time
to maintain consistency.
Will I Need to Use Wegovy Long Term?
Yes, long-term use is often necessary to achieve sustained weight management benefits.
When Does Wegovy Start Working?
Effects may begin within a few weeks, with full benefits emerging over months of consistent use.
How Long Does Wegovy Stay in Your System?
The medication’s effects can last for several weeks,
but individual response varies.
How Is Wegovy Used?
Wegovy is injected under the skin and should be used as prescribed by a healthcare provider.
Using Wegovy Pens
Follow the provided instructions for proper administration, including
cleaning the injection site before use.
Using Wegovy with Other Drugs
Inform your doctor of all medications, supplements, and vitamins you are taking to avoid interactions.
Interactions
Wegovy may interact with other drugs or supplements.
Always inform your healthcare provider of any changes in your medication.
Other Warnings
Avoid combining Wegovy with alcohol, as it may increase the
risk of side effects. Inform your doctor if you are pregnant or breastfeeding before
using Wegovy.
Pregnancy and Breastfeeding
Consult your healthcare provider regarding the use of Wegovy during pregnancy or breastfeeding.
What Should Be Done in Case of Overdose?
If an overdose occurs, contact emergency services immediately.
Symptoms may include severe nausea or dizziness.
Wegovy and Alcohol
Alcohol consumption is generally discouraged while on Wegovy to minimize side effect risks.
Read This Next: Understanding GLP-1 Receptor Modulators
Learn more about how GLP-1 analogs like Wegovy work in the body.
Take a look at my homepage; medical uses for steroids
https://lioleo.edu.vn/dang-ky-form/4.png.php?id=33k-bet
Quer começar com US$ 100 de bônus? Registre-se na [thelotter](https://thelotter-br.com) e aproveite essa oferta para novos jogadores! O processo de cadastro é fácil, e após fazer login, você poderá usar o bônus em vários jogos de cassino. Não perca essa chance de começar com uma vantagem!
https://lioleo.edu.vn/daily01-huyen/4.png.php?id=56-bet
https://lioleo.edu.vn/creatorcourse01/4.png.php?id=indox-bet
Cadastro rápido na [esoccer bet](https://esoccerbet-br.com) + US$ 100: A vantagem que você merece!
Baixe o aplicativo [batbet](https://batbet-88.com) e desfrute da melhor experiência de apostas em dispositivos móveis. A instalação é rápida e a interface otimizada oferece uma navegação ágil e divertida, com gráficos de alta qualidade para uma experiência de jogo perfeita.
A pixbet é um cassino online de confiança, com jogos populares e uma plataforma justa para todos os jogadores. E para deixar sua experiência ainda mais incrível, a plataforma oferece bônus vantajosos que aumentam suas chances de ganhar e fazem a diversão durar mais tempo.
Instale o Aplicativo [iribet](https://iribet-88.com) e Transforme Sua Experiência de Jogo com Interface Otimizada e Rápida
Cách Đăng Ký Tài Khoản 12bet – https://12bet-vn.com Nhanh Chóng Chỉ Trong 3 Phút
Chơi Tại bet168 – https://bet168-vn.com – Gửi Tiền Đầu Nhận Thưởng 100$ Hấp Dẫn
Ưu Đãi Độc Quyền: Thưởng 100$ Cho Người Dùng Mới Tại bk8 – https://bk8-vn.com
order prilosec 10mg pills – brand metoprolol 50mg tenormin 100mg uk
Receba 100$ ao Registrar-se no [esport bet](https://esportbet-br.com) e Aposte com Mais Facilidades!
Entre no Mundo dos Jogos de Azar Populares e Bônus da [moverbet](https://moverbet-login.com)
Quick and Easy: Register on phwin slot – https://phwin-slot-ph.com and Receive Your Bonus
Registre-se no [Bet61](https://bet61-br.com) e Aproveite 100$ de Bônus na Sua Primeira Aposta!
At comeon – https://comeon-in.com, customer service is available 24/7 to cater to your every need. Whether you’re looking for assistance with your account, have questions about promotions, or need help with a technical issue, our friendly, professional team is here to resolve your inquiries quickly. We pride ourselves on offering fast, efficient, and reliable support, so you can focus on enjoying your gaming experience without any concerns. Reach out to us anytime, and we’ll ensure your issues are resolved promptly.
Na [tvbet](https://tvbet-br.com), o atendimento ao cliente está disponível 24/7 para garantir que você tenha o suporte necessário a qualquer momento. Com uma equipe de profissionais altamente treinados, você pode esperar soluções rápidas para todas as suas questões, sejam elas sobre pagamentos, bônus ou qualquer outra dúvida. A plataforma prioriza a satisfação do cliente e garante que sua experiência de jogo seja sempre positiva, sem atrasos ou problemas para resolver.
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Trust yako – https://yako-in.com for Reliable Customer Service, Anytime You Need It
phl63 – https://phl63-8.com offers 24/7 customer support from a team of professionals who are always ready to address your concerns. We provide fast, reliable solutions for any issues you may encounter, whether it’s related to account management, game access, or payments. You can trust us to resolve any issues quickly and efficiently, allowing you to focus on enjoying your gaming experience.
[url=https://m358-888.com]m358[/url] พร้อมให้คำแนะนำตลอด 24 ชั่วโมง บริการลูกค้าระดับมืออาชีพ
[esportesdasorte](https://esportesdasorte-br.com): Jogos Populares e Bônus Incríveis Para Todos – Entre Agora e Experimente!
sbobet – https://sbobet-vn.com – CSKH Chuyên Nghiệp, Hỗ Trợ Liên Tục 24/7
Li-hua Yao () must be contacted if someone desires to request the
information from this examine. This part collects any knowledge citations, information availability statements,
or supplementary materials included in this article.
The data offered on this examine can be found in this article and the
accompanying Supplementary Supplies. In summary, MIFs promote myoblast proliferation, myogenic differentiation, and muscle regeneration by upregulating muscle regulatory genes.
On the other hand, they inhibit proliferation and adipogenic differentiation by downregulating adipogenic regulatory genes.
In-depth evaluation of the bindings between MSTN and the activin kind IIB receptor (ACVRIIB) or
FMOD confirmed that the residues at positions 22–31 of MSTN had been predominantly involved with both
interactions. Computational alanine scanning of MSTN–FMOD and
MSTN–ACVRIIB complexes showed that MSTN residues in this region were main contributors to ACVRIIB
and FMOD binding (Supplementary Tables S1–S3).
Last however not least, EP1LOGUE contains a proprietary vasodilating and nitric oxide-boosting formulation of gallate-enhanced oligomers derived from grape seeds and marketed as 10x more powerful than the
basic citrulline. This means better blood move to the
muscle tissue – and thus enhanced supply of epicatechin and
urolithin B. In brief, if you want to develop muscle tissue, you have to control myostatin and enhance
follistatin.
In a section 2 medical trial of patients with myelodysplastic syndromes (MDS), ACE-011 successfully decreased transfusion burden in 47% of sufferers with a high transfusion burden, while elevating Hb levels in 58% of patients with a low transfusion burden [88].
Likewise, in a part 2 clinical trial involving patients with β-thalassemia, 75% of
non-transfusion-dependent patients treated with greater doses resulted in a sustained improve
in Hb levels [89]. In addition, preclinical research in animal
fashions of pulmonary arterial hypertension (PAH) confirmed consistent efficacy
of sotatercept [90], and a phase 2 human trial for the remedy of
PAH is at present ongoing. Current literature means that MSTN acts
as a mediator between muscle and bone metabolism, influencing
bone formation and reworking via paracrine and endocrine mechanisms
[8].
We additionally measured biochemical indicators, together with LG, MG,
LA, CK, LDH, and BUN levels, to evaluate fatigue.
Previous research has highlighted the importance of glycogen as an power
source during exercise, with adequate hepatic glycogen and myoglycogen enhancing endurance and sustaining high-intensity
exercise18,19,20. LA is a key indicator for assessing fatigue levels as it is the end product of
anaerobic glycolysis throughout high-intensity train. This process can lead to a decrease in the muscle and
blood pH, which can trigger tissue injury and elevated
fatigue21,22. Elevated LDH and CK levels replicate skeletal muscle cell necrosis and tissue damage23,24.
When fatigue arises from high-intensity train, inadequate vitality from carbohydrate and fats metabolism happens, resulting in protein and amino acid depletion and
elevated urea nitrogen levels22.
It wasn’t acquired by Wealthy Gorilla Restricted until 2019, and
since then each our vary of content material and
our viewers have grown considerably. For finest results, Big Dietary Supplements advises
stacking Epitech with different prime anabolic muscle-building supplements like Annihilate and Archidone, particularly if you’re serious about gaining muscle and
power. The brand suggests consuming one capsule twice
a day, as soon as in the morning and once within the night, for a interval of 30 days,
and continuing for longer if you’re trying to maximize muscle features.
For the consumer, this implies superior energy and endurance positive aspects, plus overall muscle
growth and vascularity. Physique Essentials Epicatechin contains a highly concentrated type of naturally occurring Epicatechin, optimizing lean muscle development and recovery.
Epi-Triol by House of Muscle is an advanced muscle constructing complement that helps you construct hard, lean muscle and energy.
SOD exercise was decided utilizing the WST-8 methodology and MDA activity was evaluated primarily based on the principle of MDA-TBA adduct
formation. NAD acts as a hydrogen acceptor, and the conversion of lactate to pyruvate is catalyzed by lactate dehydrogenase.
The ensuing pyruvate then reacted with dinitrophenylhydrazine to type dinitrophenylhydrazone.
Absorbance readings have been recorded at 450, 440, and 553 nm using a spectrophotometer and
microplate reader (Thermo Fisher, USA). C2C12 cells, 3T3-L1 cells, or mouse MSCs (1000 cells/mL) were cultured in development
media supplemented with one thousand nM MIF peptides (MIF1,
MIF2, Ac-MIF1, Ac-MIF2, MIF1-NH2, MIF2-NH2, Ac-MIF1-NH2, or Ac-MIF2-NH2) for 1 day.
Media was then removed, and cells were washed with DMEM (C2C12
and 3T3-L1 cells) or Ham’s F10 (Mouse MSCs) media and then incubated with zero.5 mg/mL of
MTT reagent (Sigma-Aldrich, St. Louis, MO, USA) for 1 h at 37 °C.
Indeed, myostatin is taken into account a extremely druggable goal and the present research demonstrates a possible
novel dietary strategy for its modulation that negates prior problems
with poor ET/EA bioavailability. Polyphenolic plant extracts have demonstrated anti-inflammatory and
anti-catabolic results in vitro, however their significant translation into people
stays elusive. Urolithin A (UA), a gut-derived metabolite of ellagitannins,
has shown promise for bettering muscle function and metabolic health
in rodent models. This research aimed to explore the impact of UA
on insulin and anabolic sensitivity in human skeletal muscle cells.
Elevated angiotensin ranges diminish the satellite tv for pc
cell reservoir and impair muscle regeneration capability.
Furthermore, CKD stimulates the renin-angiotensin mechanism, which
triggers caspase three in muscle tissue and promotes actin cleavage, thus
precipitating muscle atrophy. Angiotensin II enhances muscle proteolysis by stimulating the UPS and
the TGF-β process, while concurrently reducing circulatory
IGF-1 concentrations, a principal cause of muscle mass discount [96].
In summary, CKD leads to elevated ranges of angiotensin II within the physique,
contributing to skeletal muscle atrophy. After confirming the optimistic effects of Ac-MIF1 and Ac-MIF2-NH2 on myogenesis,
we investigated the regenerative potentials of those peptides in CTX-injected mouse gastrocnemius muscle tissue.
There had been no important differences in physique or gastrocnemius muscle weights
between peptide-injected and non-injected muscles, which could be attributed to the
reality that the peptide-injected mice experiments have been conducted after a
short interval (7 days). MSCs are liable for the maintenance and recovery of SM following injury
and specific nuclear Pax7, which regulates MYOD and MYF5 [32,33].
Due to this limitation in examine design, the authors can not decide with certainty whether the increased myostatin concentration occurred during the immobilization part or the restoration phase,
or each. This is especially relevant in light of a recent 10-day mattress rest study that discovered
an unexpected improve in circulating myostatin after two days of restoration, however not in the course of the unloading interval (Oranger et al., 2022).
Why did the authors resolve to not collect blood samples on day 14
(onset of the immobilization phase) and day 28 (end of the
immobilization phase)?
In addition, ghrelin has been proven to forestall muscle
atrophy in rats by enhancing AKT phosphorylation, suppressing the MSTN pathway, and activating
myogenin and MyoD (Chen et al., 2015). Ghrelin formulations for parenteral
administration are being developed (Garin et al., 2013).
However, administration by injection over prolonged durations can end result in poor affected person compliance
and therapy failure, and ghrelin is vulnerable to enzymatic breakdown in blood when delivered intravenously (Brimijoin et al., 2016).
Ghrelin liposomes coated with chitosan are being developed for nose-to-brain administration for the therapy of cachexia (Salade et al., 2017).
It also focuses on findings in myostatin biology which will have
implications for the event of antimyostatin therapies. Customers are satisfied with
the muscle strength and recovery advantages of the nutritional supplement.
The product speeds up muscle recovery, making their exercises easier and allowing them to hold
up muscle mass. Two traits of senescent MPCs probably lead to the frequent description of CKD
as an inflammatory persistent condition. Initially, senescent cells exhibit resistance to apoptosis, resulting in their
continued existence in the senescent part. Secondly, they
formulate an SASP characterised by sustained cytokine technology [57].
However, we’ve not stopped since, as we’ve seen impressive
features in energy, muscle mass, and restoration. If you’re looking to achieve some extra
muscle mass whereas concurrently growing energy and energy, then supplementing with Epicatechin could probably be
for you. For occasion, a 12-week study discovered that whole eggs and egg
whites lowered myostatin with no difference
between the teams. (Bagheri et al., 2020) Furthermore, follistatin, which is an inhibitor
of myostatin, was increased. This has been investigated and proven in each animal research
and research with people (here’s one study example, and right
here is another). Not solely have been they no stronger than their wild, much
less huge counterparts, but when particular drive was
measured (i.e. energy as a function of muscle size) they have been weaker.
The hypertrophic pathway triggered by resistance training is certainly one of them, and a
vital one when deciding whether or to not try taking a industrial or lab grade myostatin inhibitor
(keep studying and I’ll get to that half soon).
Inhibiting MSTN may have therapeutic purposes in selling bone regeneration and healing in bone fractures, osteoporosis,
rheumatoid arthritis, and osteoarthritis. In mice, administration of recombinant MSTN propeptide improved fracture healing
in a fibula osteotomy mannequin [150]. Moreover, remedy
of younger mice with ActRIIB-Fc led to elevated bone mass [151].
Formulas of dietary supplements typically outpace the science behind their components — epicatechin supplements are one
other instance of that development. Although it could enhance nitric oxide
manufacturing and mitochondrial biogenesis, it’s unclear
if epicatechin confers significant muscle-building advantages.
Inhibiting myostatin is an example of disinhibition — when a molecule that normally
inhibits a pathway is inhibited by one other molecule, an opposite impact results.
In this case, the expression of myogenic factors increases when myostatin is inhibited.
When myostatin binds to its receptor, ActRIIB, it activates a cellular pathway
known as Smad that blocks genes from transcribing myogenic components.
Protein synthesis and degradation homeostasis are required for the upkeep
of healthy muscle mass and for sensitivity to bodily activity,
hormonal steadiness, injury, and nutritional standing [1].
The IGF1-Akt-mTOR pathway is a optimistic regulator of protein synthesis
and is counterbalanced by the myostatin—Smad2/3 pathway, which acts as a
negative regulator [5]. Imbalance within the myostatin—Smad2/3
pathway causes muscle atrophy, which, in the context
of most cancers, is called most cancers cachexia [6]. Naturally, muscle
loss happens from 35 years of age and ~30% loss happens between the ages of 50 and eighty
[7]. SM loss is the main attribute of growing older and illnesses
similar to obesity, diabetes, and cancer [8,9]. Interleukin-15 (IL-15) is highly
expressed in SM and has anabolic effects on SM protein dynamics
(Quinn et al., 2002). IL-15 mRNA expression is up-regulated throughout myoblast differentiation and its administration inhibits the white adipose tissue deposition in rodents (Quinn et al., 2005).
Spending cash on supplements that do not work will not only value you
money, it could also price you your health. Some low-quality
merchandise might comprise dangerous extracts or elements that may
cause allergic reactions and other untoward unwanted facet effects.
Wonderful outcomes from quite a few research
studies created an enormous curiosity in epicatechin. It
can indeed promote greater muscle gains, better blood flow and higher testosterone
ranges. Its most notable testosterone-supporting ingredient is patent KSM-66 extract of Ashwagandha (Withania somnifera).
This extract has been tested in quite a few studies to
be an effective natural testosterone booster, stress reducer,
and muscle and strength gainer. This supplement targets myostatin and
accommodates additional herbs to extend anabolic results, particularly well suited for bodybuilding.
The management group had a larger range and interquartile range in LOAD scores for all 3 time
factors compared with the treatment group (Table 2).
The resulting massive variance in the management group
compared with the remedy group likely is the rationale for a statistical difference within groups but not between teams.
Due To This Fact, this statistically important difference
throughout the treatment group could not mirror a clinically related change.
The failure of ACE-083 to meet scientific endpoints
ultimately led Acceleron to discontinue its improvement and shift its
focus of TGF-β focusing on therapeutics away from muscle-dystrophic illnesses.
Myostatin; also identified as development differentiation issue 8 (GDF8) has been nicely reported to negatively regulate
muscle progress and size (Carnac et al., 2007; Chen et al., 2021).
The putative involvement of MSTN in muscle atrophy has been documented
in several research, prompting interest in MSTN as a therapeutic target to counteract muscle loss in patients with a range of muscle-wasting conditions
(Baczek et al., 2020; Sartori et al., 2021).
For astronauts on board the International House Station (ISS), even high-volume resistance train doesn’t absolutely stop muscle atrophy and weakness2,four and might become infeasible if astronaut health had been compromised.
Pharmaceutical therapies that promote or preserve muscle mass and strength, alone or
in combination with train or dietary interventions, are
essential to take care of astronaut fitness
throughout long-duration spaceflight missions. An improved
understanding of mechanisms that underlie spaceflight-induced muscle loss is thus needed.
Fortetropin (Canine Muscle Method; Myos, Cedar Knolls, New Jersey, USA), a nonthermal-pasteurized,
freeze-dried, fertilized egg yolk product, was proven to have an abundance of proangiogenic and host-defense
proteins compared to unfertilized egg yolk (10).
Fortetropin is believed to advertise muscle development via
the reduction of serum myostatin through an undefined mechanism, but the measured impact on serum myostatin ranges has various in studies (11,12).
Nevertheless, a research in older women and men demonstrated no change in serum myostatin over 21 d of Fortetropin administration, regardless
of demonstrating an 18% improve within the fractional synthetic fee of
muscle protein in comparability to a placebo (13).
However, there are a quantity of potential downsides to myostatin inhibition in people looking for athletic enhancement.
Creatine and follistatin dietary supplements have not been approved by the FDA for medical
use. Regulations set manufacturing requirements for them but don’t assure
that they’re secure or effective. Some
scientists assume myostatin inhibition should be additional researched for probably preventing weight problems and diabetes [29, 26].
This impact has largely been seen in animal research on follistatin, a pure
hormone that inhibits myostatin [26, 27, 28].
Thus, Epi is the first compound ever famous, to favorably modulate both regulators of muscle growth and counsel will increase in energy.
From a biomedical perspective, myostatin inhibitors are a kind of drug
that target myostatin, a protein concerned in regulating muscle growth and
growth. Myostatin inhibitors work by blocking the exercise of
myostatin, which may lead to elevated muscle mass and energy.
These inhibitors have potential purposes in treating muscle-wasting
circumstances, corresponding to muscular dystrophy, and can also be used to reinforce muscle progress in athletes and bodybuilders.
By inhibiting myostatin, these drugs can promote muscle hypertrophy and probably improve
muscle function.
Presently, no analysis exists in CKD that elucidates the signaling
networks inhibiting NF-κB stimulating NRF2.
Nonetheless, it is posited that this effect is
mediated by way of the controlling of the enzymes MAFbx (atrogin-1) and MuRF1 throughout the ubiquitin-proteasome system.
These techniques are activated in response to oxidative stress and inflammation, thereby enhancing the
functioning of mitochondria [182,183,184]. Consequently, addressing
the NRF2 axis with strategically formulated nutraceuticals could
symbolize a viable treatment technique. Quite A Few investigations have sought
to elucidate the mechanisms of NRF2 stimulation by nutritional substances and to substantiate their
protective effects in skeletal muscle [185]. In a previous examine, inhibition of MSTN by
antibody found no change in fat mass in an animal mannequin [37].
References:
What Is Gear Steroids
ใช้แอป 205 – https://fzae4.com เพื่อเดิมพันเกม Metaverse ใหม่ล่าสุด พร้อมระบบการจ่ายเงินที่รวดเร็วและโปรโมชั่นพิเศษเฉพาะผู้เล่น VR สัมผัสโลกแห่งการเดิมพันเสมือนจริงและลุ้นรับรางวัลแบบที่ไม่เคยมีมาก่อน
Your writing style makes it easy to understand even complex topics. Thanks for putting this together!
This is a well-written and informative post. Thanks for taking the time to put this together.
This was very useful! I’ll be bookmarking this for future reference.
Thanks for sharing such valuable information. Your perspective on this topic is very insightful!
Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
medrol 16mg oral – cost of depo-medrol order triamcinolone 4mg pill
สนุกกับการเดิมพันกีฬาและ eSports ไปพร้อมกันในแอป bk7 – https://qtb29.com รองรับการเดิมพัน NBA 2K และ Madden NFL พร้อมระบบสถิติอัจฉริยะที่ช่วยให้คุณวิเคราะห์เกมและเดิมพันได้อย่างแม่นยำ
ดาวน์โหลดแอป w69คาสิโนออนไลน์ – https://ldyv5.com แล้วเล่นคาสิโนสดพร้อมกับเกมสล็อตธีมแนว Monster Hunter และ Diablo รับรางวัลพิเศษทุกวัน พร้อมกิจกรรมพิเศษที่แจกโบนัสฟรีสำหรับผู้เล่นที่เข้าร่วมล่ามอนสเตอร์
Chăm Sóc Khách Hàng ibet888 – https://ibet888-vn.com – Hỗ Trợ Nhanh, Giải Đáp Mọi Lúc
Dịch Vụ CSKH Tận Tâm kubet77 – https://kubet77-vn.com – Luôn Đồng Hành 24/7
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.info/it/join?ref=S5H7X3LP
order clarinex – buy desloratadine 5mg purchase dapoxetine generic
bk7 – https://ksi34.com อัปเกรดแอปให้มีระบบแจ้งเตือนอัตโนมัติ ให้คุณไม่พลาดทุกโอกาสทำเงิน
ดาวน์โหลดแอป w69thai – https://jius5.com เพื่อเข้าถึงระบบแจ็คพอตแบบเรียลไทม์ พร้อมเกมใหม่จากซีรีส์ Resident Evil และ Silent Hill สัมผัสความตื่นเต้นของเกมสล็อตธีมสยองขวัญ ที่จะทำให้คุณลุ้นทุกการหมุน
Dịch Vụ CSKH mig8 – https://mig8-vn.com – Tư Vấn 24/7, Nhanh Chóng, Chính Xác
Instale o Aplicativo [bet365](https://bet-365-br.com) e Jogue Seus Jogos Favoritos com Interface Otimizada e Rápida
I visited several blogs but the audio feature for audio songs present at this website is
truly superb.
[7kbet](https://7k-bet-br.com): Como Baixar e Instalar o Aplicativo Para Aproveitar Jogos e Bônus de Forma Eficiente
Nền Tảng Cờ Bạc Công Bằng onebox63 – https://onebox63-vn.com – Tiền Thưởng Hấp Dẫn Đang Chờ Bạn
Đăng Ký Tài Khoản oxbet – https://oxbet-vn.com Thành Công – Nhận Ngay 100$
Cờ Bạc Công Bằng Tại s666 – https://s666-vn.com – Đăng Ký Ngay Để Nhận Thưởng Lớn
Como Baixar e Instalar o Aplicativo [rivalry](https://rivalry-br.com) e Transformar Sua Experiência de Jogo Online
refuel – https://refuel-in.com App: The Ultimate Mobile Casino Experience is Just a Download Away
Na esportivabet, o atendimento ao cliente está disponível 24/7 para garantir que você tenha o suporte necessário a qualquer momento. Com uma equipe de profissionais altamente treinados, você pode esperar soluções rápidas para todas as suas questões, sejam elas sobre pagamentos, bônus ou qualquer outra dúvida. A plataforma prioriza a satisfação do cliente e garante que sua experiência de jogo seja sempre positiva, sem atrasos ou problemas para resolver.
Woah! I’m really loving the template/theme of this blog.
It’s simple, yet effective. A lot of times it’s difficult to get that “perfect balance” between user friendliness and
visual appearance. I must say you’ve done a fantastic job with this.
Also, the blog loads super fast for me on Chrome. Outstanding
Blog!
Saque Rápido e Seguro no betleao: Aprenda Como Retirar Seus Fundos de Forma Eficiente!
order cytotec 200mcg – diltiazem over the counter buy cheap generic diltiazem
Get the bizzo App on Your Phone for a Smooth and Fast Casino Gaming Experience
ดาวน์โหลดแอป w69 – https://rebe0.com วันนี้ รับโปรโมชั่นพิเศษมากมาย
ใช้งานสะดวก ปลอดภัย และรองรับทุกอุปกรณ์
ดาวน์โหลดแอป w69 login
วันนี้ รับโปรโมชั่นพิเศษมากมาย ใช้งานสะดวก ปลอดภัย และรองรับทุกอุปกรณ์
ติดตั้งแอป w69 ทางเข้า – https://rwho3.com อย่างรวดเร็ว รองรับทั้ง iOS และ Android สัมผัสประสบการณ์เดิมพันที่ลื่นไหลและสะดวกสบายกว่าเดิม
Bônus, Jogos Populares e Diversão Garantida na [brxbet](https://brx-bet-br.com)
Blackhatlinks.com Backlinks
pclfwysxm lpktk dfturks lhdk ptibiluizjkojjn
Na [betleao](https://betleao-cassino.com), Jogos de Azar Populares e Bônus Atraentes Esperam Por Você
Se você precisar de ajuda a qualquer momento, a [cbet](https://cbet-br.com) oferece suporte ao cliente 24/7. Com um time altamente treinado e pronto para solucionar qualquer dúvida ou problema que você possa ter, a plataforma garante que sua experiência de usuário seja tranquila e sem obstáculos. Seja para questões de pagamento, bônus ou navegação no site, a equipe de suporte está sempre pronta para ajudar, com respostas rápidas e soluções eficientes, tudo disponível online a qualquer hora do dia ou da noite.
ดาวน์โหลดแอป y8 – https://y8-th.com เพื่อเข้าถึงระบบแจ็คพอตแบบเรียลไทม์ พร้อมเกมใหม่จากซีรีส์ Resident Evil และ Silent Hill สัมผัสความตื่นเต้นของเกมสล็อตธีมสยองขวัญ ที่จะทำให้คุณลุ้นทุกการหมุน
70918248
References:
how to get real steroids (Rocky)
w69 ทางเข้า อัปเดตแอปใหม่ให้รองรับการเดิมพันแบบเรียลไทม์ เชียร์ทีมโปรดของคุณได้แบบไม่มีสะดุด
Aproveite a oferta exclusiva do bet7k para novos usuários e receba 100$ de bônus ao se registrar!
Este bônus de boas-vindas permite que você experimente uma vasta
gama de jogos de cassino online sem precisar gastar imediatamente.
Com o bônus de 100$, você poderá explorar
jogos como roleta, blackjack, caça-níqueis e muito mais, aumentando suas chances
de vitória desde o primeiro minuto. Não perca essa chance única de começar com um valor significativo – cadastre-se agora!
w69 asia ปรับปรุงฟังก์ชันแอปใหม่ ใช้งานง่ายกว่าเดิม สนุกกับคาสิโนสดและเกมสล็อตได้ทุกที่ทุกเวลา
How to Register at unobet
and Begin Winning with $100 Bonus
โหลดแอป w69 android app รับประสบการณ์การเล่นเกมที่สมจริงกว่าเดิม ด้วยระบบถ่ายทอดสดแบบ HD
โหลดแอป w69 เครดิตฟรี
188 (https://avf05.com/) รับประสบการณ์การเล่นเกมที่สมจริงกว่าเดิม ด้วยระบบถ่ายทอดสดแบบ HD
เล่นเกม w69oi – https://ndq17.com ผ่านแอป สนุกได้ทุกที่ พร้อมอัปเดตเกมใหม่ให้คุณได้สัมผัสก่อนใคร
อินเทอร์เฟซใหม่ของแอป w69 vvip ช่วยให้การนำทางลื่นไหลขึ้น
ไม่ต้องเสียเวลาค้นหาเกมโปรดของคุณ
เล่นเกม w69 casino login – https://pxpz2.com ผ่านแอป สนุกได้ทุกที่ พร้อมอัปเดตเกมใหม่ให้คุณได้สัมผัสก่อนใคร
ใช้แอป w69เข้าสู่ระบบ
เพื่อเดิมพันได้ทุกที่ทุกเวลา รองรับทั้งสมาร์ทโฟนและแท็บเล็ต
เกม สล็อต w69 อัปเดตแอปใหม่ให้รองรับการเดิมพันแบบเรียลไทม์ เชียร์ทีมโปรดของคุณได้แบบไม่มีสะดุด
Rút Tiền w88 Không
Giới Hạn – Thao Tác Nhanh Gọn
Looking for an online casino with exciting rewards?
At leon, new users can enjoy
a $100 bonus just for registering! With this bonus, you’ll be able to explore a wide range of games, including slots, poker, blackjack, and more.
Don’t miss out on this exclusive offer—sign up now and claim your $100
bonus to get your gaming experience off to a fantastic start!
http://site2.aesa.pb.gov.br/aesa/news/?id=tali-bet
http://xn--l1acbdfo1f.xn--p1ai/br/index.php?id=goceng-bet
http://sila-zerna.com/br/index.php?id=kapak-bet
http://magdalenahoffmann.com/br/index.php?id=bet-365-live
http://xn--l1acbdfo1f.xn--p1ai/br/index.php?id=kelana-bet
http://hornoscasaemilio-valoriani.com/br/index.php?id=lambang-bet
jasabola-bet
bwin-365-bet
manjur-bet
http://site2.aesa.pb.gov.br/aesa/Sports/?id=spin-bet-99
https://gvis.tramandai.rs.gov.br/web-console/Sports/?id=top-bet-99
http://hornoscasaemilio-valoriani.com/br/index.php?id=taxi-bet-88
http://pribehyfotek.cz/br/index.php?id=an777-bet
ติดตั้งแอป w69 slot ทาง เข้า เพื่อสนุกกับการสตรีมสดการแข่ง eSports พร้อมตัวเลือกเดิมพันอัจฉริยะในเกม Rainbow Six และ Overwatch
mcp-bet-login
w69 slot พัฒนาแอปให้รองรับเกมมากขึ้น มีตัวเลือกหลากหลายให้คุณเดิมพันได้อย่างอิสระ
http://sila-zerna.com/br/index.php?id=bet-365-login
เล่นบาคาร่า รูเล็ต และเกมไพ่อื่นๆ ผ่านแอป w69 mobi – https://rbyl4.com ด้วยระบบที่ลื่นไหลและภาพคมชัดระดับ HD
http://xn--l1acbdfo1f.xn--p1ai/br/index.php?id=air-bet
70918248
References:
real steroids for sale online; http://git.chilidoginteractive.com:3000/avdblair327978,
order generic acyclovir 400mg – zovirax 400mg generic buy crestor 20mg generic
70918248
References:
steroid pills
70918248
References:
Anabolic steroids online (https://gitea.createk.pe/merlincourtney)
http://xn--l1acbdfo1f.xn--p1ai/br/index.php?id=lk777-bet
order domperidone online cheap – buy cyclobenzaprine generic flexeril 15mg
70918248
References:
Which of the following conditions is often associated with the abuse of anabolic steroids?
http://www.hydraulik-tuchola.pl/br/index.php?id=arti-bet
http://mail.crn-nieruchomosci.pl/br/index.php?id=mujur-bet
http://magdalenahoffmann.com/br/index.php?id=jepang-bet
แอป w69 vip อัปเดตใหม่ โหลดเร็ว ใช้งานง่าย
และรองรับภาษาไทยเต็มรูปแบบ
There’s rather more to know in regards to the unwanted facet effects of Anavar and all anabolic steroids, so go to my primary side effects information here.
Anavar, unlike the opposite oral steroids, really places larger
stress on the kidneys than on the liver. While you probably can count
on an increase in liver enzymes whereas utilizing Anavar, for most people, this might be quite gentle and
will return to normal once you cease utilizing the steroid.
Facet effects attributable to rising estrogen levels come about when a steroid
causes the conversion of testosterone into estrogen (also called aromatization).
One of the most interesting things about Anavar is that it does
NOT aromatize and, therefore, does not trigger estrogenic unwanted facet effects.
We asked our sufferers what the “best steroids to get ripped”
are and obtained completely different answers. These
cycles are appropriate for someone who desires to get ripped but doesn’t wish to inject.
Primobolan is just like Anavar in regard to its facet impact severity, posing notably
less toxicity compared to steroids corresponding to Anadrol, trenbolone, and Winstrol.
Equipoise is a useful addition to most stacks as it’ll improve results.
Nonetheless, someone looking for dramatic outcomes would hardly ever take it
by itself. Testosterone doesn’t notably have an result
on the liver, with it being injected straight into the bloodstream.
This could be attributed to Winstrol drying out the
body, leading to much less cushion for the joints.
Overall, Anavar can present quite a few advantages for males
who want to enhance their athletic efficiency, build muscle,
burn fat, and improve overall health and well-being.
However, you will want to use Anavar responsibly and under the guidance of a healthcare skilled to attenuate the risk of side effects.
Nevertheless, there are much better pure alternate options to Anavar for girls.
It is far safer and simpler to select different choices if you want to enhance your athletic efficiency, retain your muscle mass or just boost your
vitality ranges. Trenbolone and Anavar could be stacked together during bulking or slicing
cycles, leading to appreciable fat loss and large features in muscle mass.
However, as a result of presence of trenbolone, we consider this to be a harsh cycle and never appropriate for novices.
Individuals carry various ranges of response some may display symptoms no matter
responsible use and should discontinue use instantly so as to shield
their femininity. In order to acquire the optimistic effects of anavar while minimizing
the unwanted aspect effects most males will need a big dose as a end result
of its extraordinarily mild nature to be able to acquire athletic
enhancement. Virilization refers to the promotion of
masculine sexual characteristics but thankfully anavar carries the lowest virilization ranking of any
anabolic steroid. For most ladies as long as they keep throughout the realm of
accountable doses and durations of use no virilization will occur.
Wholesome males can avoid these side-effects
with proper preventative measures coupled with accountable supplementation. Anavar can suppress
pure testosterone production however solely slightly because
it has a gentle effect on SHBG and LH and
no impact on FSH.
This is as a result of anavar reduces the fat which is covering your veins, and it fills your muscular tissues with extra
glycogen, giving them more fullness. The leaner you get, the more vascularity you’ll be capable of showcase to
your mates. Elevated ranges of testosterone at all times leads to extra energy, dimension and efficiency throughout exercises.
When it comes to combining Anavar with different substances, caution is suggested.
Anavar is understood to be a comparatively delicate
steroid with low potential for unwanted aspect effects, but it can still be dangerous when used irresponsibly or in combination with sure substances.
If you do experience any unwanted aspect effects, it’s essential to reduce your dosage or stop taking
Anavar altogether.
Ladies, on the other hand, might acquire a significant quantity of mass following an Anavar cycle.
As for a large energy enhance, which oxandrolone is
well known for producing (18), that is also very likely to stay.
Take a have a look at this thread, where customers talk about a few of their Anavar results and the way a lot of the muscle/strength features they kept.
Whereas Anavar is mostly thought-about a safe drug for men, it could nonetheless cause undesirable unwanted effects.
Frequent unwanted aspect effects of Anavar include acne, hair loss, decreased libido, and decreased
testosterone manufacturing. By stimulating the synthesis
of phosphocreatine within your muscles, Anvarol
works just like the anabolic steroid Anavar to extend
energy and vitality. Throughout cutting cycles, you’ll shred
fats whereas retaining lean muscle, making you look lean and minimize.
In truth, some research have proven that Anavar can result in adjustments in liver enzymes and elevated ranges of
liver fats. When taken in excessive doses, it can result in an increase in sebum manufacturing, which might
clog pores and result in breakouts. In addition,
Anavar can even trigger the body to retain more water than ordinary, which can also contribute
to the event of acne. It additionally helps to protect muscle mass
when you’re cutting calories, so that you don’t have to worry about losing the progress you’ve
made.
It’s advisable to consider options to safeguard liver well-being.
For newcomers to the bodybuilding panorama, an introductory Anavar cycle could
be a standalone expertise. Getting familiarized with a single compound before branching out
into stacks is vital.
It is essential to assess individual tolerance and carefully monitor for any
potential unwanted effects. It is essential to begin with a decrease dosage vary, corresponding to 10mg per day, and gradually improve it to
20mg per day if well-tolerated. Beginners should carefully monitor their body’s response
to the steroid and assess any potential unwanted side effects.
Furthermore, Anavar stimulates the production of
red blood cells through a course of called erythropoiesis.
This enhance in red blood cells enhances oxygen delivery to the muscular tissues, bettering endurance
and efficiency during bodily activities.
Making Certain regular well being monitoring and following a healthcare provider’s pointers provides a safer setting for Anavar use.
Oxandrolone dosage varies depending on the user’s bodily condition, goals, and tolerance degree.
Nevertheless, excessive dosages exceeding these
levels considerably elevate the danger of unwanted effects.
Anavar can be cycled as a standalone steroid and it can be stacked with different steroids too.
Listed under are some of the most typical Anavar cycles used by bodybuilders, each new and advanced, to realize their fitness objectives.
Anabolic steroids are man-made versions of testosterone,
the male sex hormone. Testosterone is liable for the development of masculine traits, corresponding to a deep voice
and facial hair, and can additionally be concerned in muscle
progress.
While Anavar is safer for women, excessive dosages can result in masculinization. Anavar (Oxandrolone) presents a variety of
benefits for both men and women in bodybuilding.
In terms of active duration, Anavar stays energetic in the physique for roughly 8-12 hours as well.
So taking a dose within the morning will present results that final
throughout the day and into the early night. Nitric oxide (NO) sports
vitamin has turn out to be the largest sports diet product category.
Customers usually appreciate its mild nature, translating to minimal undesirable outcomes and comparatively simpler post-cycle restoration.
For ladies, the dynamics modifications as they’re more delicate to the results
of steroids. Dosage recommendations for them are much less,
usually ranging between 5-10mg per day. Some tools users may push this up
to 15-20mg, however this steep rise considerably
escalates the chance of virilization. That’s
why even the slight adjustments in voice, increased body hair development, or some other abnormal indicators ought to be a sign to halt or modify
the consumption. In general, beginning with the lowest potential dose and observing how the
body reacts is a safer wager. This convenience
characteristic makes it well-liked among users, saving
them from injections, discomfort, and potential pitfalls.
References:
benefits of taking steroids
http://site2.aesa.pb.gov.br/aesa/Tech/?id=sports-bet
สมัครสมาชิกผ่านแอป w69com login – https://rwwa3.com วันนี้ รับสิทธิ์เข้าร่วมโปรโมชั่นพิเศษที่มีเฉพาะบนมือถือ
http://hydraulik-tuchola.pl/br/index.php?id=spot-bet
bookmarked!!, I like your site!
Everyone loves what you guys are up too. Such clever work and exposure! Keep up the awesome works guys I’ve included you guys to blogroll.
Its like you read my mind! You seem to know so much approximately this, like you wrote the book in it or something. I think that you could do with some p.c. to force the message home a little bit, however instead of that, this is great blog. A great read. I’ll definitely be back.
It’s perfect time to make a few plans for the future and it is time to be happy. I have read this submit and if I may just I wish to recommend you some interesting issues or suggestions. Maybe you could write next articles referring to this article. I want to learn even more issues approximately it!
I visited many sites except the audio feature for audio songs present at this web page is actually excellent.
bookmarked!!, I love your blog!
Aproveite a oferta exclusiva do lottoland
para novos usuários e receba 100$ de bônus
ao se registrar! Este bônus de boas-vindas permite que você experimente uma
vasta gama de jogos de cassino online sem precisar gastar
imediatamente. Com o bônus de 100$, você poderá explorar jogos como roleta,
blackjack, caça-níqueis e muito mais, aumentando suas chances de vitória desde o primeiro minuto.
Não perca essa chance única de começar com um valor significativo – cadastre-se agora!
Aposte no brapub e Receba 100$
de Bônus ao Se Registrar!
Bônus de 100$ ao Registrar-se no aviator aposta – Comece a Apostar Já!
O novibet oferece uma
excelente oportunidade para quem deseja começar sua experiência no cassino online com um bônus de 100$ para novos jogadores!
Ao se registrar no site, você garante esse bônus exclusivo que pode ser utilizado em diversos jogos de cassino, como slots, roleta e poker.
Esse é o momento perfeito para explorar o mundo das apostas
com um saldo extra, aproveitando ao máximo suas apostas sem precisar investir um grande valor logo de
início. Não perca essa oportunidade e cadastre-se já!
Ganhe 100$ ao se Registrar no casadeapostas
e Aposte de Forma Fácil!
Registre-se e Receba 100$ de Bônus no brdice
para Apostar!
Bônus de 100$ ao Registrar-se no bet esporte – Aproveite Agora!
dobrowin Oferece 100$ de Bônus
para Novos Jogadores – Registre-se Já!
Bônus de 100$ ao Registrar-se no brlwin – Aproveite Agora!
It’s also a hunger representation, meaning that customers can better
stick with any diets and cuts they’re going via to
increase muscle mass without risking additional fats being placed on. Trenbolone
steroids mimic the pure anabolic hormones in your body and are essentially an artificial alternative for testosterone.
This male intercourse hormone regulates every little thing from muscle mass
and growth to sexual well being. Trenbolone exerts its effects by binding to androgen receptors,
resulting in increased protein synthesis and nitrogen retention in muscle tissue.
This leads to accelerated muscle progress, improved feed effectivity, and
enhanced total performance. Moreover, Trenbolone has
progestogenic exercise, which can affect various physiological processes.
We observe that stacking trenbolone with other anabolic steroids will increase its risks.
In conclusion, Trenbolone stands as one of the most potent and controversial anabolic steroids in existence.
Its highly effective effects on muscle progress, power enhancement,
and body composition have made it a sought-after compound in bodybuilding and athletic circles.
However, these advantages include significant risks and authorized implications that
can’t be missed. For these seeking authorized alternatives, the world of supplements
presents a variety of choices, though it’s important to note that their effects are usually a lot
milder in comparability with anabolic steroids. Creatine monohydrate
is considered one of the most well-studied and efficient legal
supplements for increasing muscle mass and power.
It works by rising the body’s capability to provide ATP, the first
power currency of cells, leading to improved efficiency and muscle
progress.
These may include increased lean muscle mass, improved power and endurance, and enhanced fat-burning talents.
It also can assist to enhance total body composition,
giving girls a extra outlined and toned body.
Additionally, it has been shown to increase vitality ranges, cut back restoration occasions, and enhance mental focus and readability.
With these advantages, ladies can obtain their fitness goals
faster and more effectively. Trenbolone Acetate is an extremely potent anabolic steroid, and
consequently, customers may notice visible changes of their body kind.
Nonetheless, these modifications will solely take place if
the user adheres to an applicable food plan plan and engages in constant bodily activity (including cardio
and weight training). Trenbolone Acetate additionally has the ability to extend vascularity and hardness of the muscles.
This timing is crucial as it permits the supplement to be adequately absorbed and utilized
by your physique throughout your exercise. Nettle leaf extract is derived from the
leaves of the stinging nettle plant, scientifically known as Urtica dioica.
It has a protracted history of use in conventional medication for its numerous
therapeutic properties. The extract is wealthy in bioactive compounds
similar to nutritional vitamins, minerals, and plant chemicals that contribute to its potential health
benefits. Our readers must also concentrate on the potential risks of taking steroids, especially
when not beneath the supervision of a medical doctor and using underground lab products.
But you’ll look incredible, and people shall be in awe on the fast change in your physique.
With that stated, if you’ve carried out a couple of Anadrol cycles and
have a great handle on the way you reply at specific
doses, then you might select to be much less worried about getting blood done so often. Most
Anadrol tablets are available 50mg dosages, making it handy to consume the
optimal dosage of Anadrol, which is either 50mg or 100mg every day.
Studies have proven that you could hit peak positive aspects with a dosage of round 100mg every
day, with features falling after this amount whereas side effects increase16.
A normal cycle can have you placing on 25-30lbs, and although a few of this might be soon misplaced as water, even retaining
15lbs of muscle is a physique-changing outcome.
Large pumps are one other related facet, and customers will typically
describe them as the best pumps they’ve ever had.
Enclomiphene for six weeks, starting two weeks after your
final injection.
This happens as a end result of it causes a major rise in blood
pressure, which decreases the blood circulate to the
center, which means that deeper breaths are needed to maintain the right oxygen provide.
There are multiple benefits of Trenbolone, which is why it turned such
a preferred steroid in the first place. Be Part Of 15,000+ readers preserving knowledgeable and staying
updated on all the newest Peptide, TRT, and SARMs news, in solely 5 minutes per week.
I just feel that ancillaries like cabergoline should have been talked about,
as prolactin/progesterone gyno and Tren dick are very real.
To maximize the benefits of Trenbolone for chopping,
it’s essential to follow a rigorous exercise regimen that includes each strength coaching and
cardiovascular train. Trenorol is a secure and legal different to Trenbolone, produced
from natural ingredients that assist to mimic the results of Trenbolone with none dangerous unwanted
effects. It is a wonderful alternative for individuals who need to obtain the identical results as Trenbolone with out
risking their well being and well-being.
It Is really helpful that only experienced steroid customers ought
to try to use Trenbolone. This can be particularly
problematic for individuals who’re already susceptible
to breakouts.
Alternatives embody other anabolic steroids like testosterone or Nandrolone, legal
dietary supplements like creatine and protein, and pure methods
corresponding to optimized food regimen and training. Trenbolone is a
potent anabolic steroid recognized for its robust muscle-building and performance-enhancing results.
It’s not approved for human use and is primarily utilized in veterinary drugs.
Most intermediate users shall be seeking to
move on from an Enanthate-only cycle and start reaping the massive advantages of stacking testosterone with different powerful anabolics.
A 12-week testosterone cycle consisting of Dianabol at 25mg weekly just for the first four weeks boosts this bulking and strength stack.
Spanning the entire 12 weeks is Testosterone Enanthate at 500mg
weekly, thought of a really efficient dose for any person level, and Deca-Durabolin at 400mg per
week. A low 10mg dose will have women seeing vital changes to their physique, with muscle features being made much sooner.
Nonetheless, females won’t “turn right into a man” on this steroid, however they’ll
develop what we might outline as a extra masculine physique.
Some girls utilizing testosterone enanthate will be seeking to reduce physique fat to acquire
elevated definition, and this is potential at very low doses of 5mg/week.
If you want to construct muscle, Testosterone could be the
higher possibility as a end result of its capability to extend muscle mass and strength.
A PCT plan is crucial after a Tren cycle to restore pure testosterone levels.
PCT merchandise such as Clomid or Tamoxifen might help the
physique recuperate, preserve hormonal stability, and support long-term health.
For first-time customers, beginning with a lower dose can help the physique modify to Trenbolone’s efficiency.
Skilled customers may gradually improve the dose, however it’s essential
to monitor any side effects closely. I hereby conform to assume and accept
any and all risks of harm or dying associated to stated health activities.
But as the steroid is just out there for medical use, you can expect Trenorol as your best option as its legal
steroid different for muscle development. Trenorol, a fast-acting and versatile alternative to Trenbolone, delivers equally highly
effective and fast leads to as little as two weeks.
References:
winstrol steroid before and after (Leif)
Cadastre-se no aposte e ganhe – https://aposte-br.com e Receba 100$ de Bônus ao Criar
Sua Conta!
Aposte no winzada e Receba 100$ de Bônus ao Se Registrar!
O stake oferece
uma excelente oportunidade para quem deseja começar sua experiência no cassino online com
um bônus de 100$ para novos jogadores! Ao se registrar no site, você garante esse bônus exclusivo que pode ser utilizado em diversos jogos de cassino, como slots, roleta e poker.
Esse é o momento perfeito para explorar o mundo das apostas com um saldo extra, aproveitando ao máximo
suas apostas sem precisar investir um grande valor logo de início.
Não perca essa oportunidade e cadastre-se já!
Cadastre-se no bwin e
Ganhe 100$ de Bônus de Boas-Vindas!
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.
Unlock Your $100 Bonus by Registering on netbet Today
Earn a $100 Bonus Instantly – Join tsars Now!
Get Your $100 Registration Bonus When You Log In to
rivalry
Sign Up at casumo and Get a $100 Bonus Instantly!
Looking to join unibet?
Sign up now and claim your $100 bonus! The process is easy and quick,
allowing you to register, log in, and get your bonus within minutes.
With the $100 bonus, you can explore a wide range of casino games.
Don’t miss out on this special offer for new
users. Register now and start playing with extra funds!
Join mrrex Now and Claim Your
$100 Bonus in Just a Few Steps!
Looking for an online casino that rewards new players right
from the start? bluechip has
you covered! Register now and receive a $100 bonus to explore
all the games you love. Whether it’s poker, live casino games,
or sports betting, your bonus will give you the boost you need to maximize your chances of winning.
Sign up now and take advantage of this limited-time offer—your $100 bonus is waiting!
Get a $100 Bonus Just for Signing Up at leonbet!
Join betobet Now and Claim Your $100 Bonus in Just
a Few Steps!
Log In and Claim Your $100 Bonus After Registering at
pino
Looking to join mirax?
Sign up now and claim your $100 bonus! The process is easy and quick, allowing
you to register, log in, and get your bonus within minutes.
With the $100 bonus, you can explore a wide range of casino games.
Don’t miss out on this special offer for
new users. Register now and start playing with extra funds!
Looking for a way to boost your online casino experience?
21prive has just the solution! Register
as a new user and claim a $100 bonus to start playing right away.
Whether you’re into sports betting or exploring the latest slots, this bonus
gives you the perfect opportunity to get familiar with
the platform and its offerings. Don’t miss out—sign up today and start playing with your
$100 bonus in hand!
Register on buumi and Start Playing with a $100 Bonus
lottoland Login and Registration Made Easy – Claim Your
$100 Bonus!
Start Playing at gamdom with
a $100 Bonus for New Users!
Start with a Bang! $100 Bonus Awaits You at ivibet!
Looking for an online casino that rewards new players right
from the start? winny has you covered!
Register now and receive a $100 bonus to explore all the games you love.
Whether it’s poker, live casino games, or sports betting, your bonus will give
you the boost you need to maximize your chances of winning.
Sign up now and take advantage of this limited-time offer—your $100 bonus is waiting!
Get Started with a $100 Bonus at maneki
– Register Now!
Join 12bet – https://12bet-in.com Now and Claim Your $100 Bonus in Just
a Few Steps!
Start your journey at goslot with an exclusive $100 bonus!
New users can instantly claim this offer when they register, giving them a head start on exploring the diverse range of online casino games,
slots, and sports betting options available.
Don’t miss out on this exciting opportunity—sign up today and
take advantage of this amazing $100 bonus to boost your chances of winning big!
Join nyspins today and claim a
$100 bonus when you register! New users can easily sign up, log
in, and get their bonus right away. This is the perfect way to start your casino journey with extra funds to
play. Don’t miss out – sign up now and get your $100 bonus today!
Start Playing at mrbit with a $100 Bonus for New Users!
Welcome to alexander!
New users receive a $100 bonus upon registration. The process is
straightforward: create your account, log in, and your bonus will be instantly credited.
This offer is designed to give new players a head start.
With your $100 bonus, you can enjoy a variety
of games, including slots, poker, and more. Don’t miss out on this fantastic opportunity to maximize your
gaming experience. Register today and grab your bonus!
Unlock a $100 Bonus When You Register at vave Today!
Exclusive Offer: $100 Bonus at slotbox for New Users!
Complete Your casigo Registration and Get
a $100 Bonus to Play!
Join 1xslots today
and get your $100 bonus as a new user! The registration process is quick and
easy. After signing up and logging in, you’ll receive your $100 bonus immediately.
Use the bonus to explore a range of games, from slots to live dealer options.
Register now and enjoy extra funds!
Unethical suppliers have been the cause for customers experiencing terrible unwanted
effects, by promoting substances which weren’t steroids.
It’s necessary to note that virilization unwanted side effects are rare in women (who use
average doses of Anavar). And even when they did happen, they aren’t everlasting so as soon as you cease taking
Anavar; your hormones will balance out and these male traits are more
probably to disappear. So many ladies use Anavar right now,
which is why considered one of its nicknames is – the ‘girl steroid’.
This is as a end result of no other steroid produces such delicate
unwanted effects in females. Everyone’s genetics are totally different, thus it might be a good idea to watch
your liver enzymes on any steroid cycle.
Loopy Bulk is our recommended source for authorized steroid alternatives, based mostly on thousands of optimistic critiques on verified platforms such as Trustpilot and Feefo.
Alternatively, they might decide to stack the above steroids in conjunction with
Anavar. Oxandrin remains to be bought right now, however
beneath the current company name Savient. Generic Anavar is now produced
and sold, with the orphan drug designation expiring, dismantling BTG’s monopoly.
Nonetheless, due to this previous elevation in value,
in addition to excessive demand for Anavar and just a few labs
on the planet producing it, Anavar still stays costly right now.
We know it to be the highest-priced pharmaceutical steroid, along with Primobolan. BTG was granted orphan drug designation for treating uncommon muscle-wasting ailments
and circumstances similar to AIDS, Turner syndrome, and muscular dystrophy.
In fact, testosterone can be an excellent male sex hormone; it usually happens in ladies as well, though very much smaller
in amounts. There are a variety of legitimate medical uses you present in steroids for 50 years
aged or more, as an example treating osteoporosis.
Nevertheless, keep in mind that particular person reactions to steroids can differ, and
what works properly for one particular person might not essentially work as properly for another.
Furthermore, growing your dosage may improve the danger of side effects.
It is important to notice that higher dosages do
not essentially equate to extra important outcomes
and can probably enhance the danger of unwanted effects.
Subsequently, it is crucial to search out the right stability between dosage
and results.
It is necessary to notice that longer cycles might enhance the chance of side effects and suppress natural hormone manufacturing.
Whereas Anavar is wanted for its muscle-building benefits, it’s important to pay attention to
the potential side effects, together with the danger of erectile dysfunction. The decision to use Anavar must be made with an intensive understanding of
the dangers and advantages, and ideally, beneath the guidance
of a healthcare professional. If you are experiencing ED or different side effects associated to Anavar use, looking for medical advice is crucial to addressing these issues safely
and successfully. All steroids work extraordinarily
well when stacked with Testosterone, and Anavar is not any different.
This combination can be used for slicing, recomping,
bulking, and even for pure energy.
(Personally, I’ll use the drug for no much less than 6–8
weeks.) Spreading out my dose all through the day on the identical pace each time (20 mg/20
mg/20 mg) yields the greatest outcomes for me.
Use 50 mg of clomid daily during the post-cycle therapy section, and you should recuperate quickly.
This happens in each men and women, despite
the very fact that males have a lot larger testosterone ranges than females.
Despite these variations, testosterone is critical to a woman’s need, energy,
and general health. These authorized steroids take longer to work, but within a couple of months,
you need to have the ability to boost your testosterone production safely and naturally and see much better muscle growth.
Anavar’s enchantment to athletes lies in its vital influence on muscle growth, energy,
and endurance.
Sure, smaller doses can be used but 30mg will prove to be the minimum and for many
is not going to be that efficient; 50mg per actually should be
your commonplace. While 50mg will work 80mg will show to be far
simpler and in nearly all males usually side-effect free.
It ought to be noted, whereas girls will usually receive stable advantages from
this steroid alone most males will find it higher served
as part of a stack and never as a foundational anabolic steroid.
Anavar may be dosed at around 20 – 40mg per day, whereas Winstrol can be dosed
at 20 – 60mg per day. Private numbers will depend on sex, age, expertise, objective, and other exposures to Anabolics.
Both Winstrol and Anavar are Anabolic Steroids and can be used in a fat-loss or muscle-gain phase.
Females will nonetheless use less than males and can use solely 20 – 40mg per day earlier than experiencing serious unwanted effects.
It is decided by how much they will handle earlier
than seeing debilitating unwanted effects.
As a outcome, your body enters survival mode and
begins to make use of muscle as fuel as a substitute of physique fats.
Anavar is very popular amongst bodybuilders since it’s seen as a reasonably innocuous substance.
Though there are a variety of unwanted effects, the overwhelming majority of them can typically be avoided as a
result of the chemical is neither robust nor harmful. Anavar
was designed for short-term use, and medical resources,
corresponding to WebMD, level out that abusing this drug with high doses and extended intake may also
cause cardiovascular points [8].
Additionally, B-AET lowers total stress,
enhances immune function, prevents muscle loss throughout calorie
restriction, and has anti-inflammatory properties.
To prevent joint issues when using wet AAS compounds, it is essential to use the appropriate AI dose (not too high) to manage estradiol ranges and stop excessive water retention. Stacking must be accomplished cautiously,
contemplating particular person targets, tolerance, and safety.
Always consult a healthcare skilled before combining any steroids.
Stacking Anavar with other steroids entails combining it with extra anabolic compounds to enhance overall
results.
Anavar additionally has a fat-burning effect, as it can enhance
metabolic fee and target visceral fat. By growing metabolism, it promotes the breakdown of stored fats,
aiding in weight loss and contributing to a extra defined, leaner physique.
A clinical-strength nighttime formulation for testosterone
help, deep sleep, and hormonal restoration. Correct PCT
after Anavar ensures that you maintain your hard-earned positive aspects, normalize hormone ranges,
and shield long-term health. Decaduro is a protected yet powerful Deca Durabolin different designed to maximise your muscle & power positive aspects.
Combining 5 of our strongest muscle building and fats burning formulation for wonderful, fast-acting results.
For those that are more advanced, an Anavar and Test cycle
may be a good option.
While they may look related and share very similar effects some could be
more potent than others and side effects do range
depending on dose, frequency, cycle size, and so on. As i’m sure you’re aware there are hundreds
of various sorts of steroids on the market aside from Anavar.
This is the protein naturally found in milk (alongside casein),
and the most popular protein powder amongst weight lifters.
Thus even when soy protein was insanely efficient
for building muscle (which it isn’t), the dose is so tiny
– it’s going to virtually certainly do nothing.
The results are promising showing features in muscle, strength and fat loss are evident in untrained males, and these results could presumably be expedited with a excessive protein diet, training and cardio program.
We don’t suggest using Anavar alone and never training, however as a substitute consume a calorie surplus for more muscle mass, or calorie deficit for eager to lose fats mass.
Promotes muscle progress and fat loss, although it requires careful
monitoring as a result of potential side effects. Boosts lean muscle mass and strength without the chance of respiratory
irritation. HGH may be mixed with just about any anabolic steroid and used for any objective, together with bulking.
References:
dbol legal steroids (Belle)
brand domperidone – purchase tetracycline sale cyclobenzaprine ca
?Hola fanaticos del casino
Jugar online sin licencia en EspaГ±a es cada vez mГЎs comГєn. https://casinossinlicenciaenespana.guru Miles de jugadores eligen estas plataformas por su facilidad de acceso y rapidez en los pagos.
Los pagos en casinos sin licencia a veces tienen lГmites mГЎs altos. Esto es Гєtil para jugadores de alto nivel. Revisa los montos mГЎximos antes de solicitar tu retiro.
Mas detalles en el enlace – п»їhttp://casinossinlicenciaenespana.guru
?Que tengas excelentes premios!
propranolol generic – clopidogrel 150mg us oral methotrexate 10mg
Aposte no b1bet e Receba 100$ de Bônus ao
Se Registrar!
Faça Seu Cadastro no 20bet e Ganhe 100$ de Bônus Agora Mesmo!
Cadastre-se no ktobet – https://ktobet-88.com e Receba 100$ de Bônus ao Criar Sua Conta!
Ao se cadastrar no leao – https://leao-88.com -, você ganha um bônus de 100$ para
começar sua jornada no cassino com o pé direito! Não importa se você é
um novato ou um apostador experiente, o bônus de boas-vindas é a oportunidade perfeita para explorar todas as
opções que o site tem a oferecer. Jogue seus jogos favoritos, descubra novas opções
de apostas e aproveite para testar estratégias sem risco, já que
o bônus ajuda a aumentar suas chances de ganhar.
Cadastre-se hoje e comece com 100$!
No blaze, novos usuários podem aproveitar um bônus de 100$
ao se registrar no site! Isso significa mais chances de ganhar e explorar uma grande
variedade de jogos de cassino, desde slots emocionantes até
clássicos como roleta e blackjack. Com o bônus de boas-vindas, você começa
com um saldo extra, o que aumenta suas chances de sucesso.
Cadastre-se agora e use os 100$ de bônus para experimentar seus jogos favoritos com mais facilidade.
Aproveite a oferta e comece sua aventura no cassino agora mesmo!
Aproveite a oferta exclusiva do dj bet para novos usuários e receba 100$ de bônus ao se registrar!
Este bônus de boas-vindas permite que você experimente uma
vasta gama de jogos de cassino online sem precisar gastar imediatamente.
Com o bônus de 100$, você poderá explorar jogos como roleta,
blackjack, caça-níqueis e muito mais, aumentando suas chances
de vitória desde o primeiro minuto. Não perca essa chance
única de começar com um valor significativo –
cadastre-se agora!
The addition of Winstrol in this stack will amplify total anabolism and lipolysis.
Anavar doesn’t aromatize or enhance progesterone, so there is no extra risk
of gynecomastia. Testosterone suppression is going to
be significant post-cycle, requiring a strong PCT.
In this resourceful, easy-to-follow dialogue, we are going to make clear the important know-how required to maximise the
influence of an Anavar cycle for ladies in reaching a strong, awe-inspiring physique.
It’s also important to see how your body fares
all through your cycle and track your health markers – even should you feel nice.
Plus, when you do that and see that your physique is
coping nicely on a certain dose, it will present you with the option of
increasing the dose.
Trenbolone causes essentially the most hypertrophy will increase of androgen-sensitive muscle teams, such because the trapezius and deltoid muscles.
Testosterone enanthate or cypionate are common esters, as they are
slow-acting and thus require rare injections (2).
Linda, an avid fitness lover, had at all times envisioned reaching a
toned and muscular physique. After conducting extensive research and seeking
advice from an expert coach, she selected to include Anavar in her health
regimen. With steadfast dedication, Linda committed to a rigorous workout plan and paid close consideration to her nutrition.
Now we’ve taken a take a look at the assorted components that influence Oxandrolone dosage, it’d be
clever to ‘plug’ this data in and use it for a few real-world examples.
In conclusion, Anavar could be a valuable tool for athletes, powerlifters, and endurance
athletes seeking to improve their performance. By following the beneficial
dosages, monitoring your progress, and taking security precautions, you’ll find a way to expertise the
benefits of Anavar whereas minimizing the risks. Earlier
Than beginning an Anavar cycle, it’s important to consult with a healthcare skilled to find out the suitable dosage and to
observe your progress throughout the cycle.
This will assist be positive that you’re using the steroid
safely and successfully. When it involves utilizing Anavar
to boost athletic efficiency, powerlifting,
or endurance, it’s essential to grasp the suitable dosage on your
specific wants and targets. While Anavar is usually considered
a secure and effective steroid, it could nonetheless pose risks if not used responsibly.
The optimal Anavar dosage for endurance athletes ranges from 20 to 80 milligrams per day, relying on your experience degree and
objectives.
However, it typically causes virilization unwanted effects, inflicting
girls to look and sound extra masculine. Though AST/ALT enzymes
will rise, this is unlikely to cause any lasting damage to the liver, due to its self-healing attributes.
Thus, a consumer is only prone to experience severe
liver damage if Winstrol is abused and is taken for several months at a time (without biking off).
This creates an even more enhanced look, with increased
muscle tone and definition. Oil-based Winstrol is stronger
than the water-based or oral type of the drug. However, this isn’t to say it’s only utilized by girls,
with a quantity of male powerlifters and bodybuilders additionally using Anavar to good impact.
Do your personal due diligence, listen to your physique and don’t comply with any of the on this page advised products
or doses blindly. This website is not going to be held responsible for any injury
carried out to your body. When embarking on a Take A Look At Anavar cycle, it’s crucial to acknowledge
that optimum positive aspects and results are not solely depending on the utilization of steroids.
If you are not conscious, Anavar is an unlawful
substance until prescribed by a medical professional.
Not only that, but it does have some unwanted effects most would need to keep
away from. Testosterone isn’t used by ladies and is used by men no matter their objectives.
Anavar is also known as a 17-Alpha Alkylated DHT
dihydrotestosterone by-product Steroid, meaning it’s
an oral of the DHT sort.
If you are healthy sufficient to be used, maintaining a wholesome lifestyle will be crucial.
This ought to embrace a cholesterol pleasant diet rich in omega fatty acids, as
well as plenty of cardiovascular activity.
All who complement with Anavar are inspired to limit saturated fats and
simple sugars, think about a cholesterol antioxidant supplement and to maintain a close eye on their ranges.
Anavar represents one of the well-liked oral anabolic
steroids of all time, and that is largely due to its well-tolerated nature.
These weeks were principally a minimize however I am quite positive I put on fairly an amount of muscle as well, just primarily based on how I
look and feel. However tbh greatest thing for me wasn’t the
bodily gains however quite the mental upside.
I enjoyed feeling nice all day long, but it might have
been due to the stark contrast with the darkish days I was in before that.
I felt better than ever after the cycle ended, nevertheless it might’ve been due
to weight loss as nicely. Testosterone is a versatile hormone appropriate for each bulking and chopping cycles because of
its simultaneous anabolic and fat-burning effects.
However, you’ll experience such androgenic unwanted side effects as pimples hair loss and possibly an antagonistic effect on cholesterol levels.
There isn’t much difference in Anavar dosage for
bodybuilding purposes whether you’re a man or woman. For instance,
if you are stacking Anavar and Testosterone – we advocate beginning with 50mg of Anavar and 250mg of Testosterone per week.
If you’ll stack Anavar, we advocate utilizing it with
other chopping steroids like Winstrol, Clenbuterol, and
Testosterone. Your total expertise with Anabolic steroids issues when it comes to your Anavar dosage.
Anavar (oxandrolone) is a man-made steroid, much like the naturally occurring steroid testosterone.
Anavar has also been proven to be extremely efficient for treating over or extended exposure to corticosteroids, as well as for treating osteoporosis by the promotion of bone density.
However, such uses are rare in the U.S. at present because of strict laws despite
this steroid’s tremendously successful and constructive observe document.
Anavar has additionally proven to be efficient for treating
hepatitis, as nicely as promoting growth and improvement in kids who lack the mandatory hormone manufacturing.
However, that is subject to them taking a small dose for a shorter cycle.
References:
pro steriods [http://www.pesscloud.com]
Ao se cadastrar no betpix, você ganha um bônus
de 100$ para começar sua jornada no cassino com o pé direito!
Não importa se você é um novato ou um apostador experiente, o bônus de boas-vindas é a oportunidade
perfeita para explorar todas as opções que o site tem a oferecer.
Jogue seus jogos favoritos, descubra novas opções de apostas e aproveite para testar estratégias sem risco, já que o bônus ajuda a aumentar suas chances de ganhar.
Cadastre-se hoje e comece com 100$!
Comece no codbet com 100$ de Bônus de Boas-Vindas!
Cadastro Rápido no john bet – https://john-bet.com e 100$ de Bônus de Boas-Vindas!
Aposte com 100$ de Bônus no luck 2 – Cadastre-se e Aproveite!
100$ de Bônus para Apostar no flames!
Cadastre-se Agora!
Aproveite 100$ de Bônus ao Se Registrar no b2xbet – https://b2xbet-88.com – Cadastre-se Já!
Faça Seu Cadastro no mmabet e Ganhe 100$
de Bônus Agora Mesmo!
O 166bet oferece uma
excelente oportunidade para quem deseja começar sua experiência no cassino online com um bônus de 100$ para novos jogadores!
Ao se registrar no site, você garante esse bônus
exclusivo que pode ser utilizado em diversos jogos de cassino, como
slots, roleta e poker. Esse é o momento perfeito para explorar
o mundo das apostas com um saldo extra, aproveitando ao máximo
suas apostas sem precisar investir um grande valor logo
de início. Não perca essa oportunidade e cadastre-se já!
Registre-se no dobrowin – https://dobrowin88.com Agora e
Receba 100$ para Suas Apostas!
The ensuing visible impact is a more chiseled and outlined physique
form. One of essentially the most evident outcomes of an Anavar
and Take A Look At Enanthate cycle is the increase in muscle size and fullness.
Testosterone Enanthate provides the body with a slow-releasing type of testosterone, which promotes muscle hypertrophy and
elevated strength. Anavar, however, helps lean muscle retention and supplies additional hardness to the muscular tissues, making them visibly denser.
After a accomplished cycle, one is likely to see a big change in muscle definition and high
quality. The muscles could have a harder, denser look and
sharp definition, giving the physique a more sculpted appearance.
Finally, this leads to quicker fats burning and is the first cause
we embrace Cardarine on this stack. This cycle makes use of Clenbuterol within the 2-week on and 2-week off cycle format.
If you want to proceed utilizing Clen after the 8-week cycle (such
as throughout PCT), it’s attainable, because the
cycle solely contains 4 weeks of Clenbuterol.
It has long been the oral of selection for pre-competition bodybuilders and in newer years is a favorite summer drug for regular gym-goers.
If you’re looking for a protected and efficient method to get
the same outcomes as Anavar, with out putting your health at
risk, I would think about the above supplements. Clenbutrol is another pure various to
Anavar that’s made by CrazyBulk. Clenbutrol is similar to Anvarol in terms of its fat-burning
and muscle-preserving results.
In scientific research, when ladies take megadoses of Anadrol for very lengthy periods of time, masculinization doesn’t occur.
These are two of probably the most efficacious bulking steroids
combined in a single cycle. It replicates the muscle-building and strength-enhancing results
of Anadrol, but without the undesirable side effects. Women may even go for
the dose of 20 mg however it’s going to significantly
enhance their price of Virilization, therefore it’s recommended not to eat greater than 10 mg maximum.
Equipoise is used among veterinarians to stimulate urge for food and bulk
up horses after weight loss (3). Gynecomastia is a priority when biking testosterone
as a end result of its high aromatization, which means
a significant amount of exogenous testosterone will
convert into estrogen. Though not deleterious in nature, manboobs can have a negative
psychological impact in addition to being physically undesirable for some users.
In our testing, trenbolone is not particularly liver poisonous (being an injectable steroid).
Anavar additionally has diuretic results, removing extracellular fluid that obscures muscle definition. Under are 7 steroids to get
ripped—and the professionals and cons of each.
Most bodybuilders opt for an Anavar-only cycle so as to
burn fat, increase lean muscle mass and enhance their power ranges.
Such a cycle is extra in style among novices or first-timers who don’t have prior
expertise of utilizing steroids. This leads to the development of lean muscle mass and elevated strength.
In addition, Anadrol additionally inhibits glucocorticoid hormones, that are answerable for
muscle breakdown. This makes Anadrol an effective steroid for each
bulking and slicing cycles. Anavar cycles for girls ought to
ideally last 4-5 weeks to attenuate the danger of unwanted effects.
Prolonged cycles or higher dosages can improve the likelihood of experiencing adverse
effects.
Because Anavar will increase power dramatically,
it’s suited to this function properly in both men and women.
He is not just interested in bodybuilding however is a superb soccer player too.
When he isn’t writing for his web site or training at the fitness center, he loves to spend his time with this spouse
and youngsters. I know that Anavar (being an oral steroid) is metabolized in the liver, however
the pathway appears to be somewhat different from Dianabol etc.
and so carries a lower risk. The extra cycles an individual completes
and the more years they proceed to be on steroids, the larger the
risk of cardiac and hepatic complications. Dr. Ziegler
created Dianabol, a compound that’s more anabolic
than testosterone and less androgenic. Thus, prostate issues have been much less of a concern, as have been male pattern baldness and pimples vulgaris on Dianabol.
When used correctly, Anavar may help you put together for a contest, burning by way of fat whereas constructing lean muscle.
Experienced users develop accustomed to the drug, constructing
a tolerance. Giving their body some time to regulate to the results of the medicine.
Relying on the competition guidelines, earlier
wins might be stripped.
For seasonal bodybuilders, it serves as a non-bloating drug that can help
them in weight loss. And for some bodybuilders, it may give slightly enhance to their journey with minimal suppression. You should determine if it’s one thing
that resonates together with your health objectives.
Anavar is said with the dihydrotestosterone also referred
to as DHT derived from the anabolic steroid Oxandrolone.
Anavar will worsen testosterone suppression post-cycle,
requiring a extra advanced PCT compared to a
testosterone-only cycle.
Any extension beyond this timeframe or improve
in dosage demands careful monitoring for indicators of virilization in women or liver
stress in all customers. As with any anabolic
steroid cycle, customers should prioritize safety by conducting research,
consulting healthcare professionals, and frequently checking their well
being markers all through the cycle. This proactive strategy allows bodybuilders to get
pleasure from the benefits of the Check and Anavar cycle while minimizing potential dangers.
Oxandrolone can providedifferent outcomes depending on the individual’s degree of expertise in usinganabolic steroids.
Whether Or Not they are newbies, intermediate users, or advancedindividuals, Anavar can provide numerous
benefits similar to muscle growth, strengthgains, fats loss, and improved athletic efficiency.
Nevertheless, the specificresults may differ based mostly on components corresponding to genetics, dosage,
period, andoverall adherence to correct utilization.
Staying hydrated also can help with some headaches, but every consumer will discover their response
totally different. Often, these unwanted effects will subside as quickly as
two days after starting Clenbuterol, but in some instances,
it may possibly extend up to one week. Of the 2, I would consider
Clen the better muscle preserver and one that gives
you a greater minimize. Albuterol can be a respiratory treatment however is considered milder than Clen. Many in the
fitness neighborhood prefer Albuterol to Clen as a end result of it doesn’t trigger the same anxiety and jittery effects at lower
doses. This is a recipe for disappointing outcomes; women ought to be comparatively fit and experienced with sticking with a restrictive
diet whereas using Clenbuterol.
References:
Anabolic Vs corticosteroids
Bônus de 100$ para Novos Jogadores no bet7 – Cadastre-se Agora!
No stake (stake-br.com),
novos usuários podem aproveitar um bônus de 100$ ao se registrar no site!
Isso significa mais chances de ganhar e explorar uma grande variedade de jogos
de cassino, desde slots emocionantes até clássicos como roleta
e blackjack. Com o bônus de boas-vindas, você
começa com um saldo extra, o que aumenta suas chances de sucesso.
Cadastre-se agora e use os 100$ de bônus para experimentar seus jogos favoritos com mais facilidade.
Aproveite a oferta e comece sua aventura no cassino agora mesmo!
No dobrowin [dobrowin55.com],
Você Começa com 100$ de Bônus ao se Registrar!
4-Androsterone merchandise are great stackers, and could be stacked with virtually any compound.
Both experimental and anecdotal evidence helps 4-Androstenolone’s capacity to raise testosterone ranges and enhance
efficiency. Anavar® also incorporates 1-Androstenolone that has a novel structure which makes
it favorable to many people who want to stability their hormones.
IJOHMR Journal is an Open-access, Peer Reviewed,
Listed, Bi-monthly journal publishing analysis articles from numerous
sub-disciplines of Drugs and Dentistry. The journal serves as a
healthy platform for Undergraduates/ Post Graduates students in addition to different researchers to share
their data, expertise and findings with the world. The worth of Anavar can exhibit substantial
variations depending on the geographical location by which it’s purchased.
These variations are pushed by a myriad of things, together with regional demand and provide dynamics.
Understanding these worth variations is imperative when planning
a finances for Anavar supplementation.
It is also a preferred selection amongst athletes as a result of it does not trigger
the identical degree of unwanted effects as different anabolic steroids.
When shopping for Anavar, it’s essential to find a reliable supply to ensure you’re getting an genuine product.
The online market is flooded with counterfeit or under-dosed Anavar, so selecting a reputable seller
is essential.
All attainable measures have been taken to ensure accuracy,
reliability, timeliness and authenticity of the data; however Onlymyhealth.com does not take any liability for a similar.
Utilizing any data provided by the net site is solely on the viewers’
discretion. Staying hydrated and maintaining a balanced food regimen rich in vitamins helps the effectiveness of
any supplementation cycle and promotes general health.
The handiest method to make use of L-arginine to extend nitric oxide manufacturing is to give consideration to inhibiting the Arginase enzyme,
which breaks down arginine, thus stopping nitric oxide production. Hi-Tech Prescribed Drugs in Anavat used ABH and BEC-arginine
inhibitors, which help a excessive L-arginine dose within the
described product.
Clients who take Anavar report extra muscle fullness and muscle pumps, and elevated
protein synthesis. Anavar is the oral tablets containing the steroid Oxandrolone, which
has confirmed to successfully burn fats with out lowering muscle mass.
Therefore, athletes apply it for slicing cycles ― both mono and combined.
Remember, Anavar helps with muscle retention and fats burning, but results will be
maximized with the right nutrition and training. It is
essential for anyone interested in utilizing Anavar
in Mexico to understand and adjust to the legal regulations surrounding its use.
This not solely ensures compliance with the law but also promotes the security and ethical usage of the drug.
There have been circumstances of individuals shopping for steroids that have
been counterfeit or of low quality, and this can be dangerous.
This is especially advantageous throughout slicing cycles,
where the goal is to minimize back body fat without sacrificing hard-earned muscle.
By bettering nitrogen retention in the muscular tissues, Anavar creates an anabolic environment
that supports tissue preservation. Anavar, also recognized by its generic name Oxandrolone, is
a well-liked anabolic steroid that has gained recognition for its numerous advantages in the world of health and bodybuilding.
In this complete guide, we are going to delve into numerous aspects of
Anavar, together with its availability, pricing, and where to obtain it legally
and safely.
This naturally evokes the search for a simpler different to artificial
steroids. Most people asking for Anavar at present may not medically require the steroid, so medical doctors might not prescribe
or allow such individuals entry to the treatment. Nonetheless, you can nonetheless purchase Anavar from reputable pharmaceutical
corporations.The most viable possibility for purchasing the medication would be
from its producers. Most manufacturers ship as little
as 5 packages worldwide; they distribute the product principally through their websites or retail shops.
Oxandrolone isn’t an especially potent androgenic steroid,
but androgenic exercise does exist. Such activity can result in zits, accelerated hair loss in these
predisposed to male sample baldness and body hair progress.
However, most will not have an issue with these effects as the entire androgenic nature
stays very low.
For instance, liver values might rise quickly when taking anavar — as a end result of
it being a c-17 alpha alkylated steroid. Though anavar is a greater tolerated compound compared to other steroids, it still has
some drawbacks. Anavar can also be utilized by athletes who aren’t looking to enhance their bodily performance but quite simply need to
burn fat and do away with cellulite or ingrown hairs for aesthetic purposes.
Anavar could work together with many medicines,
including medicines to deal with diabetes, hypercalcaemia, hypertension and other situations.
In addition, Anavar may enhance the risks of bleeding when taken concomitantly with anticoagulants.
Nevertheless, earlier than you begin taking Anavar,
you want to always seek the guidance of your physician and perform the required medical exams to rule out possible unwanted effects and
assess the appropriate dosage.
Testicles could shrink in dimension, absence of testicular capabilities, testicular atrophy and decreased sperm depend.Clitoral enlargement, oligomenorrhea in females.
This is as a end result of of the fact that creatine phosphate synthesis is excited in the muscle cell and doesn’t accumulate
fluid. Weight lifters and different who don’t need
to transfer into the next class are using this,
because the drug gives them the chance to turn out to
be stronger with out gaining weight. These who supplement with
Anavar in the course of the cutting phase will also burn fats at a
extra environment friendly fee. Regardless of how powerful
the direct lipolysis trait is or isn’t, the metabolic price will
still be greatly enhanced. Once lean, the person may also find he appears
harder and more outlined. This is commonly accompanied by enhanced vascularity, and an total tighter look.
References:
safe steroid cycle; Darryl,
Receba 100$ ao Criar Sua Conta no omgbet – Bônus Exclusivo!
This is my first time pay a quick visit at here and i am truly impressed to read all at one place.
Very descriptive blog, I liked that bit. Will there be a part 2?
Hi there! I know this is kinda off topic nevertheless I’d figured I’d ask. Would you be interested in trading links or maybe guest authoring a blog article or vice-versa? My blog goes over a lot of the same subjects as yours and I think we could greatly benefit from each other. If you happen to be interested feel free to send me an e-mail. I look forward to hearing from you! Awesome blog by the way!
Novo no esportenet – https://esportenetbet-br.com? Faça o
Registro e Ganhe 100$ Imediatos!
Bônus de 100$ ao Registrar-se no roleta online – Comece a Apostar
Já!
Ganhe 100$ no imperador bet – https://imperadorbet-br.com ao Se
Registrar – Comece a Apostar Agora!
Receba 100$ de Bônus no betleao e
Comece a Apostar Agora!
Registre-se no codbet – https://www.codbet-br.com e Comece com 100$ de Bônus
para Apostar
This is gold, thank you!
70918248
References:
three risks of using anabolic steroids
Aproveite a oferta exclusiva do jqk bet para novos
usuários e receba 100$ de bônus ao se registrar!
Este bônus de boas-vindas permite que você experimente uma vasta gama de jogos de cassino
online sem precisar gastar imediatamente. Com o bônus de
100$, você poderá explorar jogos como roleta, blackjack,
caça-níqueis e muito mais, aumentando suas chances de
vitória desde o primeiro minuto. Não perca essa chance única de começar com
um valor significativo – cadastre-se agora!
Brilliant article!
Hey there! I just wanted to ask if you ever have any problems with hackers? My last blog (wordpress) was hacked and I ended up losing many months of hard work due to no data backup. Do you have any methods to prevent hackers?
purchase medex for sale – purchase losartan pills buy generic losartan over the counter
Loved the points you made here.
Appreciate the content you put out!
O moverbet oferece uma excelente oportunidade para quem
deseja começar sua experiência no cassino online com um bônus
de 100$ para novos jogadores! Ao se registrar no site, você garante esse bônus exclusivo que
pode ser utilizado em diversos jogos de cassino, como slots, roleta e poker.
Esse é o momento perfeito para explorar o mundo das
apostas com um saldo extra, aproveitando ao máximo suas apostas sem precisar investir um grande valor logo de início.
Não perca essa oportunidade e cadastre-se já!
No onebra, novos usuários podem aproveitar um
bônus de 100$ ao se registrar no site! Isso significa mais chances de ganhar e explorar uma grande variedade de jogos de cassino, desde slots emocionantes
até clássicos como roleta e blackjack. Com o
bônus de boas-vindas, você começa com um saldo extra, o que
aumenta suas chances de sucesso. Cadastre-se agora e use os 100$ de bônus
para experimentar seus jogos favoritos com mais facilidade.
Aproveite a oferta e comece sua aventura no cassino agora mesmo!
Seu Registro no betfury Vale 100$ de Bônus Imediato!
No bet7k, novos usuários podem
aproveitar um bônus de 100$ ao se registrar
no site! Isso significa mais chances de ganhar e explorar uma grande
variedade de jogos de cassino, desde slots emocionantes até clássicos como roleta e blackjack.
Com o bônus de boas-vindas, você começa com um saldo extra, o que
aumenta suas chances de sucesso. Cadastre-se
agora e use os 100$ de bônus para experimentar
seus jogos favoritos com mais facilidade. Aproveite a oferta
e comece sua aventura no cassino agora mesmo!
Yes, it is generally well-tolerated, making it a suitable choice for these new
to using performance-enhancing supplements. Ideally, you should dedicate just as a lot
time to your PCT as you did your cycle. The idea is
to kick off your PCT soon after the final Anavar intake.
For occasion, if your cycle lasted eight weeks, start your PCT round days later.
If you have any questions relating to this product, please feel free to
contact our customer service staff for help. Professional sportspeople and amateurs alike are increasingly inquiring about
using legally out there anabolic steroids.
For them, sports activities pharmacology isn’t a new notion,
however it is still unknown and untested. You won’t ever know, for sure,
whether or not doping is a viable different to simply coaching alone till you
study all of the features.
In Australia, you’ll find ample sources for the performance-enhancing supplement
Anavar. With an abundance of on-line sellers on the market, your focus should stay on deciding on credible
shops that uphold quality requirements. For advanced customers, Trenbolone is one other potent companion for
Anavar. Collectively, they will substantially enhance muscle definition and
energy. Trenbolone is understood for its energy,
so caution and low dosages are advised – usually starting around 50mg every different day.
There is a standard notion that women don’t require post-cycle therapy.
Nevertheless, in practice, we find ladies experience a number
of indicators of clinically low testosterone ranges following anabolic steroid use.
Anavar’s producers will all the time label it to be used as directed by
your physician; nonetheless, most people using it do not verify into the doctor’s workplace.
Two tablets a day remain our recommendation, some people have been observed to take up to four tablets
a day. This could be a type of abuse; however, dosage ought to tally with the bodybuilding objective.In the case of Anvarol, the producer prescribes three capsules a day.
We suggest that when you resolve to use it, you have
to stick with the dosage.
In 2024, it’s important to decide out suppliers who prioritize quality, transparency, and customer satisfaction. By following the
following pointers, you probably can improve your chances of
shopping for Anavar safely and obtaining a genuine, high-quality product.
Accountable buying practices and thorough analysis are key to safeguarding your health and maximizing the benefits of Anavar utilization. Using Anavar responsibly ensures optimal results while defending your health,
permitting you to realize your health objectives safely.
In the USA, Anavar is legally out there solely with a prescription from a licensed healthcare
supplier.
The world of anabolic steroids, including Anavar (Oxandrolone), presents important advantages for muscle development, fat loss, and enhanced
bodily performance. However, it’s important to prioritize safety, legality, and high quality when looking for Anavar for sale in the USA or trying to
find dependable sources to find Anavar for
sale online. All The Time seek the assistance of healthcare professionals earlier than beginning any
steroid regimen to make sure it aligns along with your well being goals
and to mitigate potential dangers. By taking these precautions, you can safely and effectively improve your bodily efficiency and achieve your fitness
aspirations. As one could possibly easily see, Anavar is quite a flexible compound by means of its makes use of.
It is known that anabolic steroids show a really poor
proportion of survivability through liver metabolism when ingested orally.
Our products are vacuum sealed to ensure safety, sterility, and
especially incomparable discretion. We ship the merchandise with their authentic packaging and
instructions. It’s potential to retain the features made during the
cycle with a correct post-cycle regime and a disciplined
food regimen and exercise routine. Bear in mind that confirming the legality, guaranteeing authenticity, and prioritizing quality are surefire methods to safe a safe and fruitful experience with Anavar
in Australia. Like every drugs, the use of Anavar isn’t devoid of potential unwanted aspect effects.
For intermediate customers, the dosage range could be elevated to 20-30mg per day,
whereas superior users could go for 30-50mg per day. It
is essential to evaluate particular person tolerance and carefully
monitor for any potential unwanted effects. By following a
structured cycle, users purpose to maximize the benefits of Anavar while minimizing
potential risks and unwanted effects.
Hydration is also emphasised to support kidney well being,
given Anavar’s potential to extend creatinine ranges.
Navigating the world of anabolic steroids can be daunting,
particularly in phrases of purchasing them safely. Anavar, a popular alternative amongst health enthusiasts and athletes,
is not any exception. A few of our patients have experienced insomnia or issue sleeping on anabolic steroids,
including Anavar. This can persist for the primary few weeks of
a cycle, and then sleep patterns usually enhance. The main objective of post-cycle remedy is to restart endogenous testosterone production. This aids in normalizing hormone levels for optimum physiological
and psychological health, in addition to retaining outcomes from
a cycle.
This is indicative of the product being underdosed, as 20 mg is
more than enough to expertise important modifications in body composition. A widespread scam
we have been made aware of is dealers labeling merchandise as Anavar, but the uncooked ingredient is Dianabol.
Dianabol is a really inexpensive oral to produce; thus, by
deceiving people in this way, sellers can dramatically increase
their revenue margin. Anavar’s half-life can improve beyond this vary,
depending on the age of the consumer. For instance, its half-life can be as excessive
as 13.three hours within the elderly (23). Thus, if we state the half-life
as 10.four hours, a post-cycle therapy protocol ought to begin fifty seven hours after the ultimate dose.
With Anavar’s brief half-life of 9.4–10.four hours,
we find it increasingly effective to split up doses all through the day, maintaining high concentrations
of oxandrolone within the physique.
References:
what is the best steroid to use (Foster)
Since both Anavar and Dianabol are taken orally, they’re prone to strain the liver resulting in a spike in AST/ALT enzyme levels in your body exhibiting liver toxicity.
In other words, this stack is more likely to trigger considerable
hepatic injury. This cycle shouldn’t be utilized by newbies and is just for advanced bodybuilders with prior expertise of getting steroids since
Trenbolone is extremely poisonous. This is an Anavar Testosterone cycle that is apt for novices who want to get good results while maintaining the unwanted effects at the minimal possible.
I should mention right here that the dosage performs an important function in preserving the unwanted effects low.
Increasing the abovementioned dosage can result in dramatic modifications in your lipid profile finally resulting in an elevated threat
of myocardial infarction.
At this dose, we’ve had ladies avoid virilization unwanted facet
effects, that are generally skilled at doses of 10 mg or extra
per day. Gym-goers and bodybuilders looking for even bigger
muscle positive aspects commonly take larger doses, starting from 30 to 50 mg per day.
Elite bodybuilders (IFBB pros) might take up to 100 mg; nevertheless,
the danger of creating unwanted side effects is excessive with
such mega doses. Gynecomastia happens when a man’s hormones turn into imbalanced and estrogen ranges (the
female sex hormone) rise excessively. This is
relatively common in AAS (anabolic-androgenic steroids) use, notably Dianabol,
because of its estrogenic nature.
In the Usa, for example, it’s categorized as a Schedule III
controlled substance, which means that it’s illegal to purchase, promote,
or possess without a valid prescription. In places like the UK,
it’s a Class C drug, which additionally requires a prescription for use.
It has been shown to provide spectacular leads to users trying
to obtain a lean and toned physique. It is normally a useful addition to
the fitness routine of each women and men who goal to improve their bodily appearance and performance.
While real anabolic steroids are neither secure nor authorized, we extremely recommend exploring authorized and secure options like D-Bal
and Anvarol from reputable brands like CrazyBulk.
Two drawbacks to Proviron are that it’s a DHT-derived steroid (44), thus, we have
seen cases of acne and hair recession or loss. Moreover, research shows Proviron to have a adverse impact on cholesterol levels, elevating blood pressure.
Can you’re taking Anavar and Winstrol together with out anything within the mix?
Yes, you possibly can, but taking Testosterone (even if it’s simply TRT dosage circa 150mg per week) is all the time
advisable. One Other possibility, for experienced bodybuilders only (!),
is to add clen to this cycle, leading to an Anavar Winstrol
Clenbuterol cycle. Even for skilled customers we check with our article on the method to decide the right
Anavar dosage. On the other hand, Dianabol isn’t recommended for women as they’ve very
low ranges of testosterone, and anything greater than that
could give rise to major unwanted effects.
For novices in bodybuilding, Anavar could be a gentle and efficient
starting point. It helps kickstart their muscle progress
journey with a decrease dosage and a shorter cycle, sometimes lasting for six to eight weeks.
This initial experience acquaints novices with the consequences of the compound, and likewise permits them to adjust the cycle primarily based
on their targets and particular person reactions. Dianabol and Testosterone work equally; Dbol
has the sting in muscle constructing, whereas testosterone has the sting in fat
loss. The major difference between them is that Dianabol is an oral steroid,
whereas testosterone is an injectable. Overall, the Sustanon Anavar cycle is a strong combination that can help you to
achieve your desired outcomes. Whether Or Not you wish to build muscle, burn fat, or enhance
your energy, this cycle may help you to succeed in your
objectives.
Regardless Of such a notion, users can administer this stack in the offseason to achieve remarkable leads
to hypertrophy. Dianabol and trenbolone ought to be perceived as a more potent and
severe stack than Dianabol and testosterone. Based Mostly on patient liver operate tests (LFTs), we’ve determined Dianabol to be
among the most deleterious steroids regarding hepatic well being.
Consequently, the inclusion of Deca Durabolin doesn’t cause any further liver pressure,
which is essential given the hepatotoxic nature of Dianabol.
The excellent news is that we now have authorized, safe options that provide
many of the advantages of Anavar. Dianabol, being a Testosterone spinoff,
will convert into Estrogen.
These varied types of testosterone possess distinct esters,
which decide their absorption price and length of presence in the
body. The normal types of testosterone are enanthate and cypionate, attributed to their affordability and ease of administration. These testimonials present
a real-world lens into Anavar’s effectivity, underscoring its recognition within the health
group. Delving into the realm of Anavar outcomes, we find a plethora of person testimonials that supply real-world insights.
These consumer stories paint a vivid image of the results and advantages that Anavar brings
to the table. We’d strictly recommend not exceeding
the prescribed dosage to keep away from any main unwanted side effects.
However, the problem is that consuming Winstrol or Anavar in larger dosages can enhance the
chances of virilization. So except you might be competing and wish it threat your feminity for it, I would not recommend utilizing this stack.
This is as a end result of Winstrol is a harsher compound and can lead
to virilization in women. ACut is the top-rated legal Anavar various that mimics
all the advantages of Anavar without any of its adverse
unwanted effects. While Anavar is appropriate
for women in low and moderate dosages, combining it with testosterone could enhance the probabilities of virilization, making it unsuitable for girls.
Like if we cycle anyhow, we will do dbol + every little thing we would stack with check anyhow.
You can always simply do dbol as a base, then add
var or winny like OP wished to. Yea okay, i can agree
with this.My downside was that when i stated “any different steroid”
i routinely assumed those i’ve heard people utilizing as solo.
But yea, definetly, even tho solo Deca was a
thing i wouldnt wager my money on that. And there was this saying that if deca and dbol doesnt bulk you, nothing will.
Plain and easy it’s a big threat, and also you won’t be proud of the results, particularly should you can’t even get an erection. Thanks again mnben87 there more I
read the needle seems the safest means any perhaps to run a correct cycle I may need to get my head
spherical that. I assume the pct is worse
than the precise cycle, and that’s saying something.
Im pleased with my exercises and my diet hasn’t been too unhealthy whereas injured just being taking
on more protein now again training day by day and extra clean carbs than just
carbs. I looked at doing an Anavar only cycle but the more I read mentioned this ought to be
run with Take A Look At which isn’t an oral so began taking a look at Dianabol.
Been reading for weeks and the extra I read I really feel the much less I perceive.
Long-term dangers of using both Dianabol or Anavar could be mitigated to some
extent with accountable usage and understanding of their pharmacological actions.
References:
pros and cons of performance enhancing drugs (healthcarestaff.Org)
Registre-se no cnc bet – https://cnc-bet-br.com e
Comece a Apostar com 100$ de Bônus!
Registre-se no pixbet – https://pix-bet-br.com e
Comece a Apostar com 100$ de Bônus!
Comece no brlwin com 100$ de Bônus de Boas-Vindas!
Novo no betway – https://betway-88.com? Cadastre-se
e Receba 100$ de Bônus ao Fazer Login!
No bggbet, https://bgg-bet-br.com,, novos usuários podem aproveitar um bônus
de 100$ ao se registrar no site! Isso significa mais chances de ganhar e explorar uma grande variedade de
jogos de cassino, desde slots emocionantes até clássicos como roleta e blackjack.
Com o bônus de boas-vindas, você começa com um saldo extra, o que
aumenta suas chances de sucesso. Cadastre-se agora
e use os 100$ de bônus para experimentar seus jogos favoritos com mais facilidade.
Aproveite a oferta e comece sua aventura no cassino agora mesmo!
While its not a necessity for any feminine athlete Anavar for girls
can ship them beyond what they may ever do with out it.
When taken accurately, Anavar can present a spread of benefits, primarily focused on muscle development, power enhancement, and fats loss.
Many people choose Anavar above other anabolic steroids as
a outcome of it doesn’t trigger important water retention, resulting
in a leaner, extra outlined look. Oxandrolone was bought in the Eighties and have become a success, current amongst many gyms because of its muscle progress.
The advantages are a huge plus for bodybuilders, although it stays an unlawful steroid.
If purchasing reliable Oxandrolone and never the synthetic sort,
there are three noted pluses customers will find.
Winstrol is far harsher on the liver compared to Anavar, even though they’re both oral steroids.
This aspect effect alone might be enough for many women to
steer the selection to Anavar over Winstrol. There is a common notion that women don’t require post-cycle remedy.
Anvarol is a legal and protected various to
the anabolic steroid Anavar. It helps to increase your strength, energy, and power ranges while
also serving to to burn fats. Anvarol is made with a mix of natural ingredients which were proven to be just as effective as Anavar however without nasty unwanted effects.
We do not advocate utilizing Anavar or any kind of steroids – obviously, they’re illegal and banned by nearly every major athletic organization worldwide.
But if you completely need to use Anavar, you have to be aware of the potential dangers.
Additionally, should you’re a man with low testosterone ranges,
Anavar is often a good possibility. When these ranges are elevated, your sebaceous glands
produce extra sebum. A steroid different with the perks of Anavar, with out the unwanted
effects. Usually, we find that the more steroids a user stacks collectively, the
higher the unwanted side effects. However, a PCT may be utilized to
speed up this process, which additionally applies to female customers.
If we detect ALT/AST levels rising notably, bodybuilders at our
clinic have had success taking TUDCA, which is a bile acid that has been shown to attenuate stress on the liver (3).
It is advised not to stack Winstrol with some other oral steroids to stop excessive hepatic damage.
Anavar (Oxandrolone) is an anabolic steroid that may have some impression on libido, however its
results on sexual desire can range from individual to individual.
While some users might expertise a rise in libido whereas utilizing Anavar, it isn’t a assured effect for everyone.
Pure supplements, for instance, can present a boost to your coaching
routine.
Estrogenic related problems such as Gynecomastia and water retention are of no concern when the Oxandrolone hormone is
being used. The use of anabolic steroids similar to Anavar could cause injury to the liver and spleen and result in liver tumors.
It can also improve ‘bad cholesterol’ and reduce ‘good cholesterol’, subsequently rising
the danger of coronary heart disease or stroke. It may trigger enlargement of breasts in both men and women, adjustments in sex drive or capacity
to have sex, and problem sleeping. These who take steroids by also experience temper swings, increased aggression, and suicidal ideas.
Regardless Of Anavar being the commonest steroid utilized by girls – based on our anabolic steroids statistics – most Anavar available on the market is faked or cut with different medicine.
However if Anavar continues to be used, it could be harder to reverse or treat virilization effects the extra they’re allowed to develop.
Some users have reported experiencing anxiety-type symptoms when utilizing Anavar.
This is likely to be an individual response to the steroid and
not something that impacts everybody. Relying on your objectives,
you might add one other compound to increase the cycle for several weeks
after stopping Anavar. Note that this doesn’t necessarily imply it’s
authorized to import or sell AAS in such countries – legal guidelines
differ. While personal possession won’t cause you legal points,
you would end up in bother if you’re caught attempting to promote Anavar to somebody.
Most folks would find that the value of pharmaceutical-grade Anavar would just not be
worth it, as it’s significantly more expensive than most other, more broadly out there steroids.
Hence, the decrease in SHBG is still highly helpful regardless of your testosterone
levels when using this steroid. It can dry out your physique, promote unbelievable muscle hardening, and
allow for a really dry, lean, and shredded physique perfect for
contests or private objectives. Ideally, you’ll be at
a low physique fat stage earlier than using Anavar
to enjoy its maximum physique enhancement results. Anavar enhances metabolic rate and lipolysis15; this makes Anavar an extremely highly
effective fat-burning steroid the place energy and stored physique fat are effectively utilized as energy.
Your metabolic fee will increase, and you can see burning
fat faster and extra efficient. Naturally, your
food plan should assist fats loss, which will all the time be
the case on a chopping cycle.
Oxandrolone is used that will help you regain weight
lost after surgical procedure, extreme trauma, or persistent infections.
Oxandrolone is also used in people who can not achieve
or maintain a wholesome weight for unknown medical
reasons. A descriptive study of adverse occasions from clenbuterol misuse and abuse for weight reduction and bodybuilding.
(2) Schimrigk, Häusler, G., Blümel, P., Plöchl, E., Waldhör,
T., & Frisch, H. If a person’s physique fats
proportion seems to have elevated on Anavar and they haven’t been overeating, then the energetic substance could also be
Dianabol. We have found that valerian root supplements could additionally be efficient for
gentle insomnia, lowering the time taken to fall
asleep and the standard of sleep (36, 37). In one study, individuals reached sleep 36% sooner after a single dose of valerian (38).
Significant decreases in pure testosterone manufacturing are a certainty when taking any steroid.
In our expertise, dosages over 10 mg/day will enhance the chance of undesirable effects.
Anavar is a light steroid that remains FDA-approved for medicinal purposes.
It is usually prescribed to sufferers affected by bone ache as
a end result of osteoporosis and people needing to achieve weight
shortly (as a consequence of trauma, an infection, or surgery).
There are a few reasons why testosterone doesn’t negatively affect blood pressure significantly.
It’s easy to overlook that to effectively end a period of steroid use you’ll have to run a bout of post-cycle remedy (PCT),
which suggests using one or two more medication. Getting off on the right
foot and utilizing a safe, authorized various such as Anvarol is the best way to maintain on track for that summer
season body. If you might have been prescribed Anavar—or if you’ve been taking it illegally—it’s
necessary to look for indicators of habit in addition to signs that could possibly
be signs of major health concerns. If you consider you might be having negative health issues because of your Anavar utilization, talk to your doctor immediately.
While Anavar is an artificial compound designed for particular medical functions, Anvarol is made from natural ingredients.
These components are designed to mimic the anabolic and fat-burning
results of Anavar without the dangerous side effects and legality points.
The key parts in Anvarol embody soy protein, whey protein, BCAA, Yam root, and ATP.
The superb factor is that outcomes from Anavar may be
astounding in that one may even see seen changes in muscle definition, physique fat share, and total physique.
References:
Steroid Weight Loss (Medicalrecruitersusa.Com)
brapub Oferece 100$ de Bônus para Novos Jogadores –
Registre-se Já!
However, if doses are too high or the particular person doesn’t respond well, we find it generally decreases
urge for food. We have not come throughout a trio of steroids that produce the
same stage of strength and mass as these. Equally, it is amongst the most
compromising cycles by way of side effects. Due to Anadrol’s short esters, its effects could be skilled within the early levels of
a cycle.
This makes Dianabol a versatile steroid that may fit right
into any cycle, whether or not you’re teaming it up
with just one other steroid or multiples in a extra advanced stack.
Dianabol is certainly one of the solely AAS men who can run as
a sole compound and not using a testosterone base when you do things properly.
Dianabol IS suppressive, but at a moderate dose and short
cycles, it’s possible to run Dbol alone and never undergo from low testosterone.
It’s the estrogen crash of suppressive AAS that causes the problems for men and Dianabol aromatizing into a considerably weaker model of
estrogen.
Injectable Anavar is a well-liked performance-enhancing substance utilized by athletes and
bodybuilders to promote muscle growth, improve strength, and improve
physical efficiency. The table consists of data corresponding to brand name, concentration, beneficial dosage, and availability.
This comparison goals to help people make informed choices when deciding
on a liquid Anavar product that aligns with their particular wants and goals.
To maximize the advantages of injectables, it’s essential to follow
a balanced food plan that supports your health targets.
First – Anvarol is authorized within the Usa for
everybody, Anavar can only be bought by folks
with a prescription and is one method or the other illegal within the States.
In males, a large portion of Libido is definitely decided by Estrogen – ask any male who has
used Letrozole and they will tell you that they lose erections within three days.
The similar is true in women, however they’re prone to androgen Testosterone.
As A Result Of Anavar is a compound recognized to have relatively few
side effects, it is the excellent Steroid for beginner feminine
athletes to start out off with.
A well-structured workout routine is essential for optimizing Anavar’s results.
Incorporating a combine of weightlifting, cardiovascular train, and stretching
can help improve its effectiveness. These include liver toxicity,
cardiovascular toxicity, and gynecomastia (development of feminine breasts in men).
Additionally, the one oral that does not effect my markers (20 to 40 MG ED 4-6 weeks).
It is important to notice that both Anavar and Anadrol are
prescription medicines, and they should only be taken beneath the supervision of a doctor.
It can additionally be essential to weigh the dangers and advantages of
taking these medications earlier than deciding to make use of them.
It is really helpful to take Anavar dosage about minutes before
understanding. This will enable sufficient time for
the steroid to take impact and give you an additional enhance of
vitality during your lifts.
Due to those cosmetic/strength benefits, Anavar
has turn out to be quite popular amongst bodybuilders. These advantages are solely enhanced by the truth that oxandrolone has few androgenic unwanted side
effects (acne, hair loss, liver disease) whereas still remaining anabolic.
The anabolic results have been confirmed by way of a big body of research, including one examine that
showed Anavar can help recover lost muscle mass as a result of burn-induced catabolism (1).
This drug has also been proven to assist HIV sufferers
regain vital lost muscle mass when 20-80mg of Anavar are taken daily (2).
The Witnessing Take A Look At and Anavar cycle is gaining recognition amongst health fanatics.
This visual journey showcases the remarkable transformations earlier than and after the cycle.
Anadrol, also called A-bombs or Oxy’s, is predominantly used by bodybuilders
in the low season (when bulking), considerably rising muscular dimension and strength.
They can assess your particular person circumstances, hormone
ranges, and health issues to discover out if it is applicable for you and create a
tailored plan. The mixture of Anavar with TRT has intrigued many, because it offers the chance of synergistic results on muscle growth and performance.
Long-term use of Anavar can lead to liver harm, and it is suggested to limit the utilization of this compound to not more than 8 weeks at a time.
Girls have been identified to use Anavar to either acquire muscle, lose fat, and even simply achieve pure strength.
That said, your dosage will not only depend on your goal but in addition in your experience degree.
If you might be looking for a safer various, I suggest making
an attempt a pure supplement like CrazyBulk’s Anvarol.
Primarily Based on our sphygmomanometer tests, the cardiovascular pressure of Anavar is marginally
higher than that of testosterone. This can be attributed to Anavar being
an oral drug, hence inhibiting estrogen conversion and subsequently activating hepatic lipase.
Anavar will end in an imbalance in HDL and LDL levels, which
is able to affect a user’s cholesterol profile. Although Anavar is
much less cardiotoxic compared to most anabolic steroids,
it still has the potential to induce hypertension.
Edema is a standard aspect effect because of testosterone rising aromatization. During
this process, estrogen ranges rise, inflicting water retention in customers.
This hormonal shift often decreases muscle definition whereas growing the risk of bloating and gynecomastia.
References:
what happens when you stop taking steroids
Seu Registro no fezbet Vale 100$ de Bônus Imediato!
Cadastre-se no obabet – https://obabet-88.com e Receba 100$ de Bônus ao Criar Sua Conta!
No cbet, novos usuários podem aproveitar
um bônus de 100$ ao se registrar no site! Isso significa mais chances
de ganhar e explorar uma grande variedade de jogos de cassino,
desde slots emocionantes até clássicos como roleta
e blackjack. Com o bônus de boas-vindas, você começa com um saldo
extra, o que aumenta suas chances de sucesso. Cadastre-se agora
e use os 100$ de bônus para experimentar seus jogos favoritos com mais facilidade.
Aproveite a oferta e comece sua aventura no cassino agora mesmo!
O tvbet oferece uma
excelente oportunidade para quem deseja começar sua experiência no cassino
online com um bônus de 100$ para novos jogadores! Ao se registrar
no site, você garante esse bônus exclusivo que pode ser utilizado em diversos jogos de cassino, como slots, roleta e poker.
Esse é o momento perfeito para explorar o mundo das apostas com um saldo extra, aproveitando ao máximo
suas apostas sem precisar investir um grande valor logo de início.
Não perca essa oportunidade e cadastre-se já!
Some individuals additionally use other dietary supplements or
drugs in the course of the cycle to enhance the results or to help with recovery afterward.
However, biking with out correct medical guidance can be harmful and lead
to harmful unwanted effects. It is an artificial type of testosterone, the male
hormone answerable for muscle development and other masculine traits.
Doctors typically prescribe oxandrolone to individuals
who have to regain weight after a protracted
illness or surgical procedure.
This kind of look isn’t everyone’s aim, so it comes right
down to your aesthetic preferences. Winstrol is among several revered and
broadly used, primarily chopping or contesting prep steroids.
All one of the best chopping PEDs have their
execs and cons, and each provides you with a unique result.
So it’s well worth evaluating Winstrol to two of the most effective chopping steroids, DHT derivatives – Anavar and Masteron. Although Anadrol causes fluid
retention, this stack is superb as a pre-competition combination as a
end result of outcomes shall be full, dry, and ripped with mass added.
In addition to muscle and power enhancements, Anavar has been reported to extend bone density and help
in restoration. These elements contribute to its
recognition among athletes looking for a competitive edge.
In addition, this versatile steroid has proven promising
ends in girls and children dealing with osteoporosis,
as it aids in promoting bone density. Due to
its gentle nature, Anavar has been a most well-liked alternative for medical functions because it poses fewer risks when compared to more
potent steroids.
Subsequently, Anavar supplies a unique benefit by helping to enhance each bone density and muscle.
Powerlifters can profit from using Anavar, but solely when used responsibly and
with caution. It is essential to comply with the recommended Anavar dosage and cycle tips and monitor the body’s response to the drug closely.
Consultation with a medical professional earlier than use is very
beneficial. It is worth noting that Anavar utilization can lead to unwanted
effects corresponding to liver damage, hair loss, zits,
and changes in temper and behavior. Powerlifters ought to monitor their health closely and search medical consideration if any antagonistic results arise.
If you’ve by no means used Anavar earlier than, it’s beneficial that you start
with a decrease dosage to assess your tolerance and response to the
drug.
The high quality and purity of the product are sometimes questionable in these eventualities.
To minimize such risks, it is essential to discover a trustworthy and dependable source
when on the lookout for Anavar. I will point out
once again that Anvarol just isn’t a steroid, it’s a protected substitute that mimics the impact of Anavar with none dangerous chemical compounds or unwanted facet effects.
One study 2 showed an improvement in low peak torque when working out
and fewer muscle fatigue.
Females typically use Anavar as a result of it’s considered
one of the milder steroids. It’s less more probably to trigger severe unwanted aspect effects in comparability with different anabolic steroids and is effective in lowering physique fats.
Anavar’s medical uses are various, reflecting its potent anabolic properties
and delicate side effect profile. One of its earliest scientific functions
was in the treatment of extreme burn victims.
Anavar may cause other unwanted effects of a milder nature which embrace, headache, swelling in the arms and legs, insomnia, and mild to severe zits.
We ought to note that clitoral enlargement and deepening of the voice are unwanted aspect effects that may turn into permanent.
Anavar is a managed substance and is in opposition to the law to make use of and not using
a prescription in many nations.
This has allowed Anavar to maintain up a loyal consumer base, from skilled athletes to health enthusiasts, who search the benefits of anabolic steroids with out the cruel consequences.
Primobolan (Metenolone enanthate) is a well-liked anabolic
steroid for both women and men. For girls, it is typically used as a means to improve muscle mass
and power while minimizing the danger of masculinization.
And the most well-liked injectable steroids will all the time be cheaper – often less expensive than Anavar.
Unexpected water retention is one other occasional
unfavorable remark users make about Anavar – but these
people are virtually definitely victims of purchasing counterfeit Anavar.
Optimistic reviewers will state that Anavar is essentially the most
well-tolerated steroid they’ve used. Nonetheless, it’s
essential to take a look at what dosage they’ve used so you can determine how
the dose might influence your results and (lack of) unwanted
facet effects. As you possibly can see, estimating a easy lack of fat in kilos is nearly unimaginable.
If you’re already very lean and are just attempting to
shred those previous few cussed pounds, you will be shedding lower than someone
doing their first chopping cycle.
Another key facet of Anavar’s fat-burning potential lies in its capacity to protect and even build lean muscle
mass whereas in a caloric deficit. This is particularly necessary for women,
who often wrestle with dropping muscle mass together with fats when weight-reduction plan. By sustaining or increasing muscle tissue, Anavar helps
to maintain the metabolism elevated, as muscle tissue is extra metabolically energetic than fat tissue.
This muscle-preserving impact permits ladies to maintain a
better calorie burn at the same time as they shed weight,
making the fats loss process more efficient and sustainable.
Extra skilled female customers or these competing at a excessive level might
steadily improve their dosage to mg per day. However, it
is essential to notice that larger doses significantly improve
the danger of virilization and different unwanted effects.
By stimulating the synthesis of phosphocreatine inside your muscles,
Anvarol works similar to the anabolic steroid Anavar to increase energy and
power. During slicing cycles, you’ll shred fat whereas retaining lean muscle,
making you look lean and cut. Whereas Anavar is usually utilized
by males during chopping phases, ladies can achieve significant advantages from it in each slicing and bulking cycles.
Anavar helps women construct lean muscle while simultaneously reducing body fats.
When combined with a balanced food regimen and consistent exercise, it could result in rapid enhancements in physique composition, enhancing muscle tone
and total physique. Anavar is often referred to as the “female-friendly” steroid, largely as a result
of its reputation amongst girls using performance-enhancing substances.
Cardio may be boring, but it’s a good way of burning calories and serving to to burn fats and maintain you good and lean. Whereas lifting is important, especially if you wish to enhance your lean mass, to be able to burn fats you will want to make certain that you keep on high of your cardio.
Consuming junk will cancel out the fats burning results of winny, that means you won’t
burn fat, and in all honesty, it means you just about ought to have just saved your money.
For men, with particularly powerful steroids, food regimen and training are literally not all that necessary.
Some bodybuilders will put an excellent percentage of physique fats on in the process.
Ladies use steroids as well as men, and we want to be sure that they use
them safely, healthily, and as successfully as possible.
References:
best weight loss steroid (Micheal)
buy cheap nexium – buy imitrex no prescription buy imitrex medication
Brilliant article!
Aproveite 100$ de Bônus no betobet ao Criar Sua
Conta!
I’ll definitely try this out.
Aposte com 100$ de Bônus no betcris – Cadastre-se e Aproveite!
buy levaquin medication – buy generic dutasteride order zantac 150mg
?Hola aventureros del azar
Empieza a jugar sin preocuparte por cuГЎnto debes ingresar.
Una casa de apuestas espaГ±ola puede ser una excelente opciГіn, pero no descartes explorar otras con licencias extranjeras. Comparar te darГЎ mГЎs beneficios.
Mas detalles en el enlace – http://casasdeapuestassinlicenciaespana.xyz/
?Que tengas excelentes partidas!
Helpful read! I’ll share it with my friends. Found more info at https://580-bet.com too.
futebol gratis ao vivo -(https://f7ypw9h7.com)
seubet:
100$ de Bônus para Novos Jogadores – Cadastre-se
Já!
Ganhe Agora com os Jogos do Cassino nine casino!
Si quiere saber más sobre los esteroides, por favor lea el resto del artículo y
otros disponibles en el sitio net. Solía estar presente bajo el dominio .com, pero debido
a problemas legales tuvieron que suspender su actividad por unos años.
Muchos medicamentos (PCT, Inhibidores de Aromatasa, Cabaser, etc.) provienen de farmacias, así que puedes estar
seguro de que funcionarán como deben. El resto viene de los mayores fabricantes europeos, así que la calidad también debería ser buena.
Esta sustancia contrarresta, entre otras cosas, la atrofia de los testículos, facilitando así el PCT.
En caso de un ciclo basado en la testosterona y que dure menos de 20 semanas, no
hay necesidad de hacerlo.
Una búsqueda rápida en Web permite acceder a cientos de páginas webs en las que, teóricamente,
puede comprarse de forma sencilla casi cualquier
sustancia. El uso simultáneo de drogas que se metabolizan a través del
hígado (la más importante es el alcohol) puede incrementar los niveles de toxicidad
hepática. En Canadá, los investigadores han concluido que el uso de esteroides
entre los estudiantes atletas está muy extendido.
Un estudio realizado en 1993 por el Centro Canadiense para el
Deporte Libre de Drogas encontró que casi 83,000 canadienses entre las edades de eleven y 18 años usan esteroides.
Los AAS también son ilegales sin receta en Australia,
Argentina, Brasil y Portugal, y están catalogados como Medicamentos Controlados de Clase C en el Reino Unido.
Los AAS están disponibles sin receta en algunos países como México y Tailandia.
Sinembargo, se torna dif�cil de atribuir estas alteraciones solo a los anab�licosporque en muchos casos estos se combinan con otras drogas como las anfetaminas.
La educaci�n e informaci�n sobre el uso de los esteroides se debe tratar aescala escolar,
programada, dosificada y dentro de las mallas curriculares quelos programas deportivos incluyan.
Institucionalizarse y convertirse en pilaresque sustenten los modos de actuaci�n no solo de atletas, entrenadores o equiposdeportivos sino de
naci�n debe ser pr�ctica com�n, por lo que la educaci�nes un eslab�n fundamental a todos los niveles.
Pero algunos atletas han admitido haber usado esteroides, que son unas hormonas artificiales
que mejoran las fuerza y la masa muscular. Pero algunos niños,
algunos adolescentes y algunos adultos siguen teniendo
ganas de probarlos. Por lo que realmente se utilizan en los deportes y
en el culturismo en specific. Muchos entran en bioquímica y fisiología, no lo haremos, pero
caminan a través de la “superficie”. Los esteroides son sustancias de origen animal o,
más raramente, de origen vegetal, que poseen una alta
actividad biológica. Por ejemplo, los esteroides anabólicos de cortico alivian la inflamación y si no fuera por ellos, te retorcerías de
dolor.
Su uso prolongado puede causar efectos secundarios como aumento de peso, osteoporosis y supresión del sistema inmunológico.
Los esteroides sexuales, como los estrógenos y la testosterona,
están involucrados en el desarrollo sexual y la reproducción. En resumen, los esteroides tienen usos médicos legítimos, pero su
uso indebido puede tener consecuencias graves para la salud.
En este caso son drogas más versátiles que, combinadas correctamente con fármacos de los otros grupos y junto a una dieta adecuada, pueden servir para ambos
propósitos. Entre los más populares de este grupo se encuentran el
Winstrol (estanozolol), Primobolán y Anavar, drogas que
se emplean básicamente en ciclos de definición. Si bien todos
los esteroides son derivados de la Testosterona de forma genérica,
la clasificación que se suele hacer de éstos es en tres clases.
Las hormonas peptídicas solubles en agua no pueden penetrar la membrana de las células grasas y solo afectan indirectamente al núcleo de
las células diana a través de su interacción con los receptores de la
superficie celular. Sin embargo, como hormonas liposolubles,
los AAS son permeables a la membrana e influyen en el núcleo de las
células por acción directa. La acción farmacodinámica de AAS comienza cuando la hormona exógena penetra la membrana
de la célula diana y se une a un receptor de
andrógenos (AR) ubicado en el citoplasma de
esa célula. Desde allí, el compuesto receptor de hormonas se difunde hacia
el núcleo, donde altera la expresión de genes o activa procesos que envían señales a
otras partes de la célula.Diferentes tipos de AAS se unen al AAR con diferentes afinidades, dependiendo de
su estructura química. El consumo de AAS interrumpe el eje hipotalámico-pituitario-gonadal (eje
HPG) en los hombres. En el eje HPG, la hormona liberadora de gonadotropina (GnRH)
se secreta desde el núcleo arqueado del hipotálamo y estimula la hipófisis anterior para que
secrete las dos gonadotropinas, la hormona estimulante del folículo (FSH) y la
hormona luteinizante (LH). En los machos adultos, la LH estimula las células de Leydig en los
testículos para que produzcan testosterona, necesaria para formar nuevos espermatozoides a través de la espermatogénesis.
De hecho, la DHT tiene menos del 1% de la afinidad de la
testosterona por ZIP9, y la metribolona y la mibolerona AAS sintéticas son competidores ineficaces para el receptor de manera
related. Estas mujeres tienen poca o ninguna producción de sebo, incidencia de acné o crecimiento de vello corporal (incluso en las áreas púbica y axilar).
Además, las mujeres CAIS tienen una masa corporal magra que es regular para las mujeres pero, por supuesto, está muy reducida
en relación con los hombres. Estas observaciones sugieren que el AR es principal o exclusivamente responsable
de la masculinización y la miotrofia causada por los andrógenos.
Sin embargo, se ha descubierto que los mAR están involucrados en algunos de los efectos
de la testosterona relacionados con la salud, como
la modulación del riesgo y la progresión del cáncer de próstata.
De la misma forma que una cerradura está construida para una
sola llave, también estas células admiten una única molécula geométrica.
Cuando el fármaco llega a su receptor; se inician una
serie de reacciones químicas (muchas de las cuales no se
conocen) y se produce una respuesta biológica. La capacidad
de ser metabolizado por la 5α-reductasa y la actividad AR de los metabolitos resultantes parece ser
uno de los determinantes principales, si no el más importante,
de la proporción androgénica-miotrófica para un AAS dado.
Pueden ocurrir una serie de efectos secundarios graves si los adolescentes usan AAS.
El aumento del acné es usual en ambos sexos; la libido puede aumentar o, con menor
frecuencia, reducir; pueden incrementarse la agresividad
y el apetito. En varones, es posible observar ginecomastia, atrofia testicular y disminución de la fecundidad.
Los efectos virilizantes (p. ej., la alopecia,
aumento de tamaño del clítoris, hirsutismo, voz grave)
son comunes entre las mujeres. Asimismo, puede disminuir el
tamaño de las mamas, atrofiarse la mucosa vaginal y cambiar o detenerse la menstruación. El uso indebido de anabolizantes es común en el ámbito deportivo y
en el culturismo. Algunos atletas los utilizan con la esperanza de mejorar su rendimiento y obtener ventajas
competitivas.
Los andrógenos o AAS son uno de los tres tipos de agonistas de hormonas sexuales, los
otros son estrógenos como el estradiol y progestágenos como la progesterona.
Los esteroides anabólicos son hormonas sintéticas elaboradas para
imitar la testosterona, un tipo de hormona
masculina. Ciertos tipos de esteroides anabólicos son recetados por profesionales médicos
para tratar una serie de problemas de salud tanto en hombres como en mujeres, pero tienen mala reputación debido a la forma
en que han sido abusados por algunos culturistas
y atletas. Los diferentes esteroides, según la forma
en que se administran, son líquidos inyectables, pastillas orales y parches cutáneos.
Los esteroides anabólicos son sustancias sintéticas relacionadas con las
hormonas sexuales masculinas (andrógenos). Provocan el crecimiento del músculo esquelético (efectos anabólicos),
el desarrollo de características sexuales masculinas (efectos androgénicos) y también tienen algunos otros efectos.
References:
how to buy steroid online
Existen en el mercado diversas opciones que, aunque no proporcionan los mismos efectos
que los esteroides anabólicos, pueden ser útiles para alcanzar los objetivos deseados sin infringir la
ley. Algunas opciones populares incluyen suplementos nutricionales y programas
de entrenamiento adecuados. Estas alternativas legales
pueden ayudar a los individuos a alcanzar sus objetivos sin correr riesgos legales o para la salud.
En este artículo analizaremos las consecuencias jurídicas que podría acarrear para un sujeto la
venta, suministro y consumo de esteroides, anabolizantes y sustancias ilegales
que busquen mejorar el rendimiento deportivo. El uso de esteroides sin supervisión médica puede
tener graves consecuencias legales para aquellos que deciden utilizarlos.
En muchos países, el uso de esteroides sin prescripción médica es ilegal y está considerado como un delito.
Después de usar el suplemento todos los días durante 60 días, debe tomar 10 días
de descanso y reiniciar el ciclo para obtener los mejores resultados.
Winsol puede producir resultados aún mejores cuando se utiliza junto con D-Bal.Un programa de entrenamiento sensato
puede ayudarte a conseguir los resultados que buscas más
rápidamente. Tome three cápsulas por la mañana durante los 60 días
que debe utilizar el suplemento. Aunque Winsol es otro gran suplemento de CrazyBulk que puede funcionar solo, es
mejor utilizarlo junto con D-Bal. Cuando se utiliza de esta manera, trabajan juntos
para ayudarle a mejorar su musculatura y lograr el crecimiento muscular al mismo tiempo.Winsol es un gran suplemento para aquellos que buscan mejorar los niveles de energía
y la resistencia. Debido a estas propiedades, es considerado por muchos como un producto
imprescindible para los culturistas.
Las hormonas sexuales, el colesterol, los ácidos biliares y algunos medicamentos son ejemplos de
esteroides. CrazyBulk es considerado por muchos como el mejor fabricante
y distribuidor de esteroides legales. La testosterona baja, cuando no se trata, puede provocar problemas
graves, como una elevada sensibilidad emocional, altos niveles de estrés, poca confianza en sí mismo y, en common,
una peor salud. Las tensiones a las que se enfrentan los hombres una vez superados los 30 años o a principios de los 40 debido al aumento de las responsabilidades también pueden tener un gran efecto en sus
niveles de testosterona y, por tanto, en su vitalidad.
TestoPrime es uno de los mejores suplementos
para el aumento de la testoterona en el mercado. A medida que
los hombres envejecen, pueden notar ciertos cambios, como menos
energía, menor deseo sexual y otros síntomas.
Además, el envejecimiento puede conducir a la acumulación de grasa en el cuerpo causada por un metabolismo
que se ralentiza.
Es recomendable consultar a su médico antes de comenzar cualquier régimen de suplementos.
En la mayoría de los casos, se pueden pedir esteroides de origen sintético.
Suelen ser derivados artificiales de hormonas naturales y sirven para mejorar rápidamente la condición atlética.
Estos incluyen Turinabol, Methandrostenolone,
Parabolan, Methandienone, Clenbuterol, y así sucesivamente.
De hecho, es bien sabido que la metandrostenolona mejora el rendimiento atlético mientras esculpe el cuerpo del atleta.
Pero además de la importante función que Dianabol desempeña en el cuerpo,
hay muchos usos terapéuticos para este producto.
Sin embargo, si usted tiene acceso a este medicamento en algunos países, las regulaciones siguen siendo muy estrictas (si no prohibitivas) tanto en Francia como en Europa.
En esta sección, discutiremos algunos factores que debe considerar al comprar alternativas de esteroides naturales y
legales en línea. Dosis Comprobamos los niveles de dosis
de estas alternativas de esteroides naturales y legales antes
de recomendárselas. Sin duda, vienen con dosis altamente
confiables y seguras, y no tendrá ningún problema para adherirse a ellas.
Además de mejorar la vascularización, Winsol también aumentará sus niveles de fuerza y resistencia.
Está repleto de poderosos ingredientes naturales como L-carnitina, colina, DMAE, raíz de ñame
silvestre y aceite de cártamo en polvo.
Una estrella puede crecer en semanas para desempeñar un papel que
requiere un individuo definido. Para una ganancia muscular extrema o una pérdida de
peso, se necesita un esteroide superior. Envío & Devoluciones Antes de realizar su pedido en línea,
verifique si la marca authorized de esteroides alternativos enviará su producto a su ubicación.
Esto le ahorrará cualquier inconveniente durante la entrega o
devolución de productos. TestoPrime está repleto de ingredientes 100%
naturales y altamente efectivos como panax ginseng, ácido D-aspártico, extracto de té verde, alholva, ashwagandha y zinc.
El propósito de esta combinación es ayudar a perder grasa y eliminar el agua retenida en tu cuerpo durante el ciclo de volumen muscular.
Las sales biliares poseen esteroides con esqueletos de colano, compuestos por 24 átomos de carbono y que poseen 5 átomos de
carbono en la cadena lateral del carbono 17. En los insectos, las aves y los anfibios se
encuentran esteroides tanto en sus membranas como en las estructuras de muchas de sus hormonas y en algunos venenos.
Los esteroides también forman parte de la estructura de varios venenos
producidos por hongos. A partir de la estructura básica del
esterano con cuatro anillos fusionados, tres ciclohexanos
nombrados con las letras A, B y C y un ciclopentano nombrado con la letra D,
se forman cientos de estructuras esteroideas naturales y sintéticas.
Pueden obtener esteroides reales, siempre existe la posibilidad de que los esteroides
estén por debajo del estándar requerido o completamente por debajo del estándar en muchos casos.
El uso de esteroides farmacológicos también está muy extendido entre los
aficionados. Se trata de una solución excelente en caso de que el cuerpo haya alcanzado el límite de su rendimiento fisiológico y ya no pueda crecer tan rápido como antes.
Dianabol también puede causar daño al hígado, cáncer de
hígado y coloración amarillenta de la piel y
los ojos (ictericia). En los adolescentes, su efecto secundario
más común es el retraso del crecimiento, mientras que en los adultos, Dianabol puede reducir la libido y la
actividad sexual. Mareos, dolor de cabeza y náuseas también son efectos secundarios conocidos del uso de la
tableta. Y el tramadol es un analgésico autorizado que actúa sobre el sistema
nervioso central y hace que el dolor sea más soportable en los deportes de alta exigencia.
“Están los que podríamos denominar esteroides naturales, presentes de forma pure en las plantas y en los animales formando las hormonas sexuales, el colesterol o los ácidos biliares. Así se fabrican, por ejemplo, algunos medicamentos”, explica Laura García Iruretagoyena, dietista-nutricionista,
periodista y farmacéutica. Que sin duda será
como cincelada como un dios griego dentro de los treinta días simplemente con la
CrazyBulk corte Montón. Ya sea que usted está obteniendo la competencia todo listo, listo costa, o simplemente listo para bajar
unas mandíbulas, que sin duda triturar un poco de grasa corporal grave sin derramamiento de su masa muscular ganado duro.
Aumento de la fuerza de núcleo difíciles y niveles
de potencia por supuesto, tendrá sus entrenamientos hasta
el extremo. Winstrol es sólo uno de los esteroides más eficaz para el corte que podría impulsar y aumentar su masa muscular y la resistencia.
Está hecha de ingredientes activos bien conocidos en el barrio
clínica y se preocupa por su seguridad y la seguridad, así como
la eficiencia.
De todos modos, la idea detrás de la invención de esta droga es que los atletas pueden evitar el tabú de la inyección de esteroides.
Los creadores simplemente tomaron testosterona
y agregaron un enlace doble a las posiciones de carbono 1 y 2, así como un grupo metilo 17 de
la posición de carbono para hacerlo hepatotóxico (para que el hígado no destruya
la droga). El término «androgénico» se refiere a los cambios físicos experimentados
por un macho durante la pubertad. Efectos androgénicos se experimentaron de
manera similar en una hembra. Esta propiedad es responsable de la mayoría de los
efectos secundarios del uso de esteroides. Es fácil que el peso se salga de control, especialmente si lleva un estilo de vida sedentario y come comidas rápidas con regularidad.
Con ejercicio regular y una buena dieta, controlará fácilmente su peso.
References:
D ball Steroid Results (vertexinc.ca)
Los céridos más comunes son la lanolina (grasa de lana de oveja), la cera de abeja y el cerumen del conducto auditivo externo en los seres humanos.
Los Medicamentos Antiinflamatorios No Esteroides, también conocidos como AINE, son una excelente opción si quieres aliviar la inflamación y la fiebre.
Su fórmula actúa rápidamente reduciendo
la inflamación sin necesidad de contener esteroides en su composición química.
Las gotas para los ojos con esteroides se pueden usar para
aliviar la inflamación, la picazón o los ojos rojos secos.
Cuando los corticosteroides alivian el dolor, se debe a que tienen una inflamación reducida que podría causar dolor.
Las inyecciones epidurales también pueden ocasionalmente provocarle
un dolor de cabeza fuerte que solo se alivia al acostarse.
Esto debería mejorar por sí solo, pero infórmeselo a
su especialista si lo obtiene.
En contraste, la vida media de un esteroide como el-Medrol (un tipo
de esteroide inyectado en los músculos) es mucho más larga, alrededor de los
21 días. Esto significa que el cuerpo tarda unas tres semanas en eliminar la mitad
de la dosis del medicamento, y tardará aún más en librarse de que todo el medicamento
se aclare del cuerpo. Incorporar diferentes tipos de ejercicios, como pesas libres, máquinas y entrenamiento funcional, es clave para evitar el estancamiento.
Cambiar las rutinas regularmente mantendrá los músculos en constante crecimiento.
La mayoría de los principiantes, cuando se inician en el gimnasio,
tienen como objetivo inmediato conseguir un cuerpo comparable al de los atletas profesionales.
Pero conseguir ese resultado no llevará meses, sino años de entrenamiento intensivo.
Piensa en el receptor androgénico como una cerradura y la testosterona es la
llave. Cuando la testosterona no está enlazada a un receptor se le llama “Testosterona libre”.
Sólo alrededor del 2% de toda la testosterona en el sistema es realmente “libre” en cualquier momento dado.
Se observa que durante los three primeros días posteriores a
la inyección, la concentración sanguínea de testosterona period
muy superior al rango alto de normalidad
del hombre sano regular (cercano a 30 nmol.l-1).
Los esteroides inyectados son mucho más efectivos miligramo por miligramo ya que
no están sujetos al proceso de digestión y al primer paso del hígado.
Un ejemplo principal de esto es el cortisol esteroide, que se produce a partir de la corteza externa de las glándulas suprarrenales,
que se sientan encima de los riñones. Algunas de las funciones que sirven incluyen el mantenimiento de los niveles
normales de azúcar en la sangre y el equilibrio de electrolitos (sodio y potasio).
También se producen naturalmente en el cuerpo, pero a menudo se usan de fuentes
externas para proporcionar beneficios de una dosis mejorada mayor de la que el
cuerpo puede producir por sí mismo.
Viagra es el nombre patentado de sildenafil, un medicamento utilizado en el tratamiento de la disfunción eréctil.
Su acción principal es aumentar el flujo sanguíneo en los tejidos
del pene, lo que conduce a una fuerte erección. Se trata de un medicamento
eficaz, que se utiliza con mayor frecuencia para su uso ocasional o en terapias complejas para restaurar
la función eréctil. Son los lípidos más abundantes en las células,
y son una forma eficiente de almacenamiento energético.
Los carbohidratos y las proteínas pueden transformarse en lípidos, cuando la cantidad de calorías
que ingresan en un organismo es mayor que la requerida. Los lípidos o grasas son un conjunto de moléculas orgánicas, químicamente heterogéneas, insolubles en agua, pero solubles en solventes orgánicos no polares
como el cloroformo, el éter, el benceno, and so on.
Acostumbrarte a tu propia imagen corporal puede ser difícil si te sentís distinto a todos los demás.
Muchos adolescentes se inician en el físico-culturismo como una forma
de ayudar a mejorar esa imagen, y eso puede ser algo muy saludable.
Sin embargo, cuando un adolescente se obsesiona o
solamente esta atrás de objetivos a corto plazo como marcarse en 6 semanas, entonces
se puede volver un problema muy serio cuando las prohormonas/esteroides
entran en la mescla. Se recomienda tomar Clomid durante las primeras 2 semanas del submit ciclo y luego cambiar a Nolvadex durante las siguientes
2 semanas.
Esto puede ayudar a reducir los síntomas de asma y EPOC, como sibilancias y falta de aliento.
A veces se les llama “inhaladores preventivos” porque pueden ayudar a prevenir sus síntomas.
Los corticosteroides causan inmunosupresión principalmente
por el secuestro de linfocitos T CD4+ en el sistema reticuloendotelial y por la inhibición de la transcripción de
citocinas. La salud es un tema complejo, y cada uno de nosotros tiene
una historia diferente que contar. 👉 Algunos de
los esteroides más seguros que se recomiendan para los principiantes son Testosterona, Masterone, Turinabol, Anavar y Dianabol.
Si tu cuerpo no tiene suficiente calcio, tus huesos podrían debilitarse y
ser más susceptibles a fracturas. Algunas personas creen que tomar
suplementos de calcio puede ayudar a aumentar su altura al fortalecer los huesos.
Para fines clínicos como tratar la sarcopenia, hipogonadismo, bajo apetito sexual, and
so on.
Uno de los factores principales es la duración del ciclo anterior y los esteroides utilizados.
Si el ciclo anterior fue corto y los esteroides utilizados no son muy potentes, entonces el tiempo entre ciclos podría ser más corto.
Sin embargo, si el ciclo anterior fue más largo
y los esteroides utilizados fueron más potentes, entonces se recomienda
esperar un tiempo más largo antes de comenzar un nuevo
ciclo. Si eres un principiante en el mundo de los esteroides, es importante
que comprendas que no hay una respuesta única y common para la pregunta
de «¿Qué esteroides usar por primera vez? Considera tener una
conversación privada donde puedas expresar tus preocupaciones sin juzgar.
Utiliza un enfoque empático, preguntando cómo se
siente y si ha notado cambios en su salud o bienestar.
Los terpenoides se encuentran en muchos de los mismos organismos que producen y utilizan terpenos.
Si estás pensando en comprar esteroides ilegalmente, quizás debas leer nuevamente los
efectos secundarios y contraindicaciones.
Los daños de los esteroides anabólicos se hacen evidentes después de
unos años de uso. Las investigaciones han demostrado que no sólo aumentan el trabajo del corazón, sino que también pueden propiciar la formación de tumores cancerígenos, cambios de humor y trastornos de personalidad (2,3,4).
La función principal de los esteroides en el ámbito de la
salud es reducir la inflamación y suprimir el sistema inmunitario.
Este artículo trata de disipar algunos de esos mitos, a la vez que
te proporciona datos sobre los beneficios de la mayoría de los esteroides anabólicos.
Además, la eficacia de estos tratamientos puede verse limitada en algunos pacientes,
lo que ha generado la necesidad de buscar alternativas más seguras y eficientes.
Si eres un principiante en el mundo de los esteroides anabólicos, probablemente hayas oído
hablar de los ciclos y los post ciclos. Los ciclos son períodos en los que se toman esteroides para aumentar la masa muscular y mejorar el rendimiento físico,
mientras que los submit ciclos son el período posterior al
ciclo en el que se toman medidas para ayudar al cuerpo a recuperarse.
Además de estos efectos, el uso de esteroides puede provocar complicaciones en otros sistemas del cuerpo.
References:
winstrol steroid cycle, https://careervault.horizonbeam.com/employer/Efectos-secundarios-del-clembuterol,
kto bet: Ganhe Rápido
com Jogos Populares!
Ganhe no sao jorge bets com
Jogos Populares e Simples!
Ganhe Agora nos Jogos Populares do Cassino lendas bet!
jogos win: Onde a Sorte Encontra os Melhores Jogadores!
Cassino luck: Onde Jogadores
Conquistam Prêmios!
Ganhe Prêmios Rápidos e Simples no Cassino apostaganha!
f12 bet: Diversão e Grandes Ganhos com Jogos Populares!
Cassino Online aposte e ganhe: Jogos Populares, Grandes
Oportunidades!
Jogue Agora no john bet e Ganhe Grande!
Jogue e Vença Agora no Cassino premier bet!
Ganhe no pixluck bet
com Jogos Fáceis e Populares!
HU
bet 558: Vença com Jogos Populares e Rápidos!
Cassino vai da bet: O Melhor Lugar para Apostar e Ganhar!
Ganhe Agora com os Jogos do Cassino winzada 777!
Jogos Populares do Cassino pague bet para
Você Ganhar!
Ganhe Agora nos Jogos Populares do Cassino jogodeouro!
Ganhe Agora com os Jogos do Cassino esportenet bet!
Jogue e Vença Agora no Cassino simples bet!
Cassino 7755 bet: Onde Você Pode Ganhar
Facilmente!
order meloxicam 15mg pill – tamsulosin where to buy cost tamsulosin 0.2mg
bet ting: Jogue e Ganhe com Facilidade e Diversão!
?Hola seguidores del azar
ВїTe gustarГa ganar 20 euros por registrarte? Solo necesitas crear tu cuenta, reclamar tu bono y lanzarte a la aventura en slots, ruletas y mucho mГЎs. Los casinos online en EspaГ±a te ofrecen esta ventaja para que juegues sin preocupaciones.
La guГa definitiva para obtener 20 euros gratis sin depГіsito – casino20eurosgratissindeposito
?Que tengas excelentes victorias !
Aposte nos Melhores Jogos do Cassino Online 5500 bet!
Ganhe Prêmios Fantásticos com Jogos Populares no jack bet!
brx bet: O Cassino
Online Mais Fácil de Ganhar!
?Hola entusiastas de las apuestas
Apostar sin dni ya no es un problema para los jugadores espaГ±oles. Hoy en dГa existen muchas casas que operan legalmente fuera del paГs y permiten registrarse sin documentaciГіn. En casasapuestassindni.xyz puedes revisar cuГЎles estГЎn disponibles en este momento.
apostar sin dni sin problema – casas de apuestas sin verificacion
?Que tengas excelentes botes impresionantes!
?Hola fanáticos del juego
Las casas apuestas sin dni han ganado terreno frente a las tradicionales. Los usuarios valoran cada vez mГЎs la privacidad, la velocidad y la flexibilidad que ofrecen estas plataformas.
casas de apuestas sin verificacion top – apuestas deportivas sin dni
?Que tengas excelentes premios grandes !
Aposte nos Melhores Jogos e Vença no Cassino oba bet!
Diversão e Prêmios Fáceis no Cassino 522 bet!
Ganhe Agora com os Jogos Populares do bons casino!
Jogos Populares do Cassino estrela bets para Você Ganhar!
Cassino abc bet: Vença com Jogos Populares e Simples!
Cassino bgg bet: Grandes Vitórias Esperam
por Você!
Ganhe Rápido e Fácil no Cassino 777 casino!
Aposte e Vença Agora no 1win casino!
Ganhe Fácil no Cassino Online bet casino!
Jogue e Vença no Cassino Online win bet com Facilidade!
Jogue no mma bet
e Ganhe Prêmios Fantásticos!
Cassino bet sporting: Onde a Sorte Está
ao Seu Lado!
betanobet:
Apostas Fáceis, Grandes Chances de Ganhar!
Cassino 136 bet:
O Melhor Lugar para Apostar e Ganhar!
Descubra os Jogos Mais Populares no Cassino ir6 bet e Ganhe!
Ganhe Agora no geral bet com Facilidade nos Jogos Populares!
Jogue e Vença Agora no Cassino qqq bet!
Ganhe Fácil no 3y casino com Jogos Simples e Rápidos!
Cassino bet4: Aposte Agora e Ganhe Facilmente!
Ganhe Rápido nos Jogos do Cassino Online 667 bet!
Ganhe No Cassino aviator aposta:
Jogos Populares, Grandes Prêmios!
Aposte e Ganhe no 193 bet – Apostas Populares!
Aposte no Cassino 7k bet e Experimente a Diversão!
Ganhe Grande no Cassino zeroum bet!
Ganhe no Cassino Online kto casino com Jogos Simples e Populares!
Cassino nacional bets: Onde Você Pode Ganhar
Rápido e Fácil!
Jogos Populares e Grandes Premiações na 74 bet!
Aposte nos Jogos Populares do Cassino wj casino
e Vença!
Documentos e Procedimentos para Saque na futebol ao vivo vasco: Como Evitar Retardos
Com a futebol ao vivo g1,
o processo de saque é direto e sem complicação.
Envie os documentos corretos e você receberá seus fundos
rapidamente.
Como Retirar Seus Fundos da futebol ao vivo na globo de Forma Segura e Eficiente
globo play ao vivo futebol:
Como Garantir Agilidade no Processo de Saque
jogos futebol ao vivo: Como Realizar Saques Rápidos com Documentação Apropriada
futebol hoje ao vivo na tv e a Segurança de Seus Saques: Como Protegemos Seu Dinheiro
Como Realizar um Saque na futebol ao vivo gremio de Forma Simples e Ágil
A tv futebol ao vivo é confiável para saques rápidos.
Certifique-se de enviar os documentos corretamente, como identidade e comprovante de residência.
Processo de Retirada na jogo futebol ao vivo: Como
Evitar Problemas e Garantir Agilidade
Como Solicitar Saque de Forma Rápida na app de futebol ao vivo:
Evite Atrasos
sites de futebol ao vivo:
Como Garantir Agilidade no Processo de Saque
Saques rápidos, sem complicação, e com total segurança.
Tudo o que você precisa fazer é enviar os documentos
corretos para a rmc futebol ao vivo.
Como Retirar Seus Fundos da futebol ao vivo resultado de Forma Segura
e Eficiente
Segurança nas Retiradas da youtube futebol ao vivo: Como Evitar Problemas
futebol ao vivo resultados: Como
Retirar Dinheiro de Forma Rápida e Segura Sem Complicação
Tudo o que Você Precisa Para Solicitar o Seu Saque na futebol ao vivo no celular
маркетплейс аккаунтов соцсетей маркетплейс аккаунтов
?Hola entusiastas del entretenimiento
Con el casino 20 euros gratis sin depГіsito podrГЎs vivir la emociГіn de las apuestas online desde el primer momento, sin tocar tu cartera.
Tiradas gratis sin depГіsito: ВЎGira y gana desde EspaГ±a! – casino20eurosgratissindeposito
?Que tengas excelentes triunfos !
Agilidade e Segurança no Saque da g1 futebol ao vivo: Como
Funciona o Processo
продать аккаунт аккаунты с балансом
купить аккаунт с прокачкой услуги по продаже аккаунтов
Retirar seu dinheiro na futebol ao vivo apk
é simples! Apenas envie os documentos necessários e seu saque será processado rapidamente.
A tudo tv futebol ao vivo oferece uma plataforma segura para saques rápidos, sem complicação.
Basta enviar seus documentos corretamente.
магазин аккаунтов покупка аккаунтов
Saque Rápido e Seguro: Como a radio futebol ao vivo Protege Seus Ganhos
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
аккаунты с балансом маркетплейс аккаунтов
Retirada Simples na placar ao vivo futebol: Como Evitar Burocracias
площадка для продажи аккаунтов профиль с подписчиками
Your article helped me a lot, is there any more related content? Thanks!
перепродажа аккаунтов платформа для покупки аккаунтов
купить аккаунт продажа аккаунтов соцсетей
продажа аккаунтов https://magazin-akkauntov-online.ru/
биржа аккаунтов продать аккаунт
аккаунты с балансом продажа аккаунтов соцсетей
купить аккаунт продажа аккаунтов
заработок на аккаунтах магазин аккаунтов
Para retirar dinheiro da anime de aposta, tudo o que você
precisa fazer é enviar o seu CPF e um comprovante de residência.
Rápido e fácil!
A novibet aposta torna
o processo de saque fácil e seguro. Com documentos básicos, você terá acesso aos seus fundos rapidamente.
aposta app e a Retirada de Fundos:
Como Garantir Seu Dinheiro em Menos Tempo
Como Retirar Ganhos na paqueta aposta com Agilidade e
Segurança
Saques Rápidos e Seguros na aposta multipla: O Que Você Precisa Saber
A mr aposta oferece um processo
de saque simples e rápido. Basta fornecer os documentos exigidos e seus ganhos
serão transferidos para você.
Com a bbb aposta, seus saques são feitos rapidamente,
e você pode confiar que a plataforma oferece total segurança para suas transações.
Saque na sport aposta:
Como Enviar os Documentos Corretos para Evitar Retardos
Na 9game aposta, o processo de saque é tão simples quanto fazer um depósito, desde que você tenha seus
documentos prontos.
Com a 12bet aposta, o processo de
saque é direto e sem complicação. Envie os documentos corretos
e você receberá seus fundos rapidamente.
Passo a Passo para Retirar Seus Ganhos na crash aposta: Agilidade e Segurança
Na aposta ganh, seus saques são processados com agilidade e
você sempre sabe exatamente quais documentos são necessários.
aposta facil: Dicas para
Realizar Saques Rápidos e Sem Problemas
Para realizar saques rápidos e seguros na aposta best, basta enviar o seu
CPF e um comprovante de residência. É fácil e rápido!
betsbola aposta:
Como Garantir Agilidade no Processo de Saque
A aposta esporte
torna a experiência de retirada de fundos tranquila e rápida,
com a proteção total de suas informações bancárias.
A plataforma aposta maxbet é uma
das mais seguras do mercado, garantindo a segurança
dos seus saques com a exigência de documentos básicos.
Passo a Passo para Retirar Seus Ganhos na aposta loteria: Agilidade e Segurança
Sell accounts Marketplace for Ready-Made Accounts
Website for Buying Accounts Guaranteed Accounts
Na aposta paga,
seus saques são tratados com rapidez e segurança.
Apenas forneça os documentos necessários e você terá
acesso aos seus fundos.
Se você deseja sacar seus ganhos rapidamente,
a betspeed aposta é a escolha certa.
Só precisa enviar os documentos corretos.
Na aposta mr jack,
o processo de saque é tão simples quanto fazer um depósito, desde que
você tenha seus documentos prontos.
Com a 365 aposta, você pode
realizar saques de forma rápida, apenas enviando
os documentos necessários, como identidade e comprovante
de pagamento.
O Que A aposta jogos Precisa Para Realizar Seu Saque Sem Demoras
Retirar Seus Fundos na aposta jack de Forma Rápida: Dicas
e Truques
Account Trading Account Catalog
O Que A aposta pixbet Precisa Para Realizar
Seu Saque Sem Demoras
Saques seguros na filme de aposta?
Sim, basta enviar a documentação correta e pronto, você receberá seu dinheiro rapidamente.
Com a aposta bets, você pode retirar seus ganhos
com facilidade e sem preocupações. O processo de retirada é ágil e totalmente seguro.
Como Retirar Seus Ganhos da 7 games aposta: O Processo Explicado
Saques rápidos, sem complicação, e com total segurança.
Tudo o que você precisa fazer é enviar os documentos corretos
para a pin up aposta.
Website for Buying Accounts Buy and Sell Accounts
A allwin aposta oferece
a você uma maneira rápida e segura de retirar seus
fundos. Basta enviar seus dados pessoais e o comprovante de residência.
Se você deseja retirar seus fundos de forma rápida, a aposta ufc é a
escolha ideal. Com um processo simples, você só precisa enviar
os documentos corretos.
Você sabia que a aposta 1 saque oferece uma das maneiras mais seguras de retirar seus fundos online?
Só enviar seus documentos básicos.
Como Sacar Seus Ganhos na sssgame aposta de Forma Rápida e
Segura
A aposta tudo bet garante que você terá acesso ao seu dinheiro rapidamente.
Envie os documentos necessários e aguarde o processamento rápido.
Se você está buscando um processo de saque rápido e seguro, a f12 aposta oferece exatamente
isso. Envie seus documentos e pronto!
Saque Rápido na luvabet aposta:
Passo a Passo para Retirar Seu Dinheiro Sem Complicação
Saques Rápidos e Seguros na futebol aposta:
O Que Você Precisa Saber
grande aposta: Como Garantir
Saques Rápidos e Sem Complicações
A wingdas aposta garante total
segurança nas transações, permitindo que você retire seus fundos de
maneira rápida e sem complicações.
Retirar seu dinheiro na elite aposta é simples!
Apenas envie os documentos necessários e seu saque
será processado rapidamente.
Retirando Fundos na aposta popo:
O Que Fazer Para Garantir a Segurança do Seu Dinheiro
pag bet aposta: Como Fazer
Saque Sem Estresse e Com Garantia de Segurança
Se você busca uma maneira segura de retirar seus ganhos,
a aposta kto é a melhor
escolha. Envie os documentos solicitados
e pronto!
Você sabia que na aposta bet365, para realizar o saque,
tudo o que você precisa é um documento de identidade
válido e um comprovante de residência recente?
Como Realizar Saques na criar aposta com Facilidade e Segurança
rivery aposta: O
Que Você Precisa Saber Antes de Solicitar o Seu Saque
aposta porno: Como Garantir que Seu Saque Seja Processado Imediatamente
Retirando Fundos na aposta bbb: O Guia Completo de Segurança
e Agilidade
Você quer saber como fazer um saque rápido na casas da aposta?
Envie apenas seus dados pessoais e comprovantes, e a plataforma
cuidará do resto.
Passo a Passo para Retirada de Fundos na bonus aposta de Forma Simples
Fazer um saque na aaa jogo aposta é rápido e fácil, e a segurança dos seus dados
financeiros é totalmente garantida.
Para retirar dinheiro na casas aposta, tudo o que você precisa fazer é enviar alguns documentos simples, e pronto!
Retirar seu dinheiro na 1 aposta app é simples!
Apenas envie os documentos necessários e seu saque será processado rapidamente.
bolsa aposta: Como Realizar Saques Rápidos com Documentação Apropriada
Buy and Sell Accounts Sell accounts
Account Purchase Account Purchase
Saques seguros na h2bet aposta?
Sim, basta enviar a documentação correta e pronto, você
receberá seu dinheiro rapidamente.
Website for Buying Accounts Online Account Store
Saque na dupla aposta:
Como Garantir que Seus Ganhos Cheguem Rápido
à Sua Conta
Passo a Passo para Retirar Seus Ganhos na cssa de aposta: Agilidade e Segurança
Com a 1 aposta, você pode retirar
seu dinheiro rapidamente. Só precisa enviar os documentos certos e o saque será
processado de forma eficiente.
Quais São as Formas de Saque na aposta mix e Como Elas Garantem Sua Segurança?
Como Sacar Seus Ganhos na tigre aposta de Forma
Rápida e Segura
A tvbet aposta garante que seu processo de saque será feito rapidamente,
desde que você envie os documentos corretos.
Passo a Passo para Retirar Seus Fundos de Forma Segura
na aposta 10
Como Garantir Saques Rápidos e Seguros na aposta da sorte
Sell Account Secure Account Sales
A jogo aposta Protege Seu
Dinheiro: Descubra Como Garantimos Saques Sem Riscos
Saque Fácil e Seguro na banca de aposta: O Que Fazer Para Não Perder Seu Dinheiro
Como Realizar Saques na casa da aposta
Sem Enfrentar Problemas
Retirada de Fundos na smash aposta: Como
Solicitar Seu Saque de Forma Ágil
Retirada Simples na aposta caixa: Como Evitar Burocracias
Saque Seguro na luva bet aposta:
Como Evitar Fraudes e Garantir Seu Dinheiro
Documentos e Procedimentos para Saque na aposta blaze: Como Evitar Retardos
Agilidade e Segurança no Saque da app de aposta:
Como Funciona o Processo
Documentos Necessários para Saque na winmi aposta: Evite Atrasos
Retirando Fundos na sites de aposta: O Guia Completo de Segurança e Agilidade
Com a casa das aposta,
você tem a garantia de que seus saques serão processados rapidamente, desde que você forneça
os documentos solicitados.
Saque na aposta 1 real: Como Enviar os Documentos Corretos
para Evitar Retardos
Guia Completo de Saque: Como Evitar Complicações na aposta 24 horas
Na capa de aposta, a segurança dos seus fundos é garantida.
Apenas envie seus documentos e seus saques serão processados sem
demora.
Como Retirar Seus Fundos da bolsa de aposta de Forma Segura e Eficiente
Account Trading Platform Account Trading Platform
A aposta e ganhe assegura transações rápidas e seguras.
Basta enviar os documentos certos e você poderá sacar seus ganhos sem demora!
Sell Account Account Sale
Saques na aposta casada: O Que
Você Precisa Saber Para Retirar Seu Dinheiro com Facilidade
A aposta ganhar facilita o saque de seus ganhos
com um processo simplificado, garantindo a segurança dos seus dados
financeiros.
Retirando Dinheiro da aposta ganhe: O Que Fazer
Para Garantir Seu Saque Rápido
Sell accounts Gaming account marketplace
Com a rivalry, seus saques são processados rapidamente.
Envie apenas os documentos certos e receba seu dinheiro em breve.
Na esportenet,
seus saques são tratados com rapidez e segurança.
Apenas forneça os documentos necessários e você terá
acesso aos seus fundos.
Como Realizar um Saque Rápido na bet nacional:
Dicas e Procedimentos
Passo a Passo para Retirar Seus Fundos de Forma Segura na fresh casino
talon777: Como Realizar Saques Rápidos
com Documentação Apropriada
bet way: O Que Você Precisa Saber Antes de Solicitar o
Seu Saque
Dúvidas Sobre o Saque na supremo?
Veja Como Você Pode Retirar Seu Dinheiro Sem Complicação
Guia Completo de Saque: Como Evitar Complicações na spinbookie
Acelerando Seus Saques na flames bet: Como Tornar o Processo
Mais Ágil
Dúvidas Sobre o Saque na brapub?
Veja Como Você Pode Retirar Seu Dinheiro Sem Complicação
Para um saque rápido na poplottery, basta enviar seus
dados de identidade e comprovante de residência.
A plataforma cuida de todo o resto.
Retirar Seus Fundos na lottoland de Forma Rápida:
Dicas e Truques
onebra: Como Retirar Seus
Ganhos de Forma Simples e sem Erros
A bet esporte Protege Seu Dinheiro:
Descubra Como Garantimos Saques Sem Riscos
A esportesdasorte Protege Seu
Dinheiro: Como Garantir Saques Rápidos e Seguros
Retire seus fundos da mr jack aposta com facilidade, enviando apenas os documentos solicitados.
A plataforma garante total segurança.
Retirando Fundos na pgwin:
O Que Fazer Para Garantir a Segurança do Seu Dinheiro
Saque Sem Complicação: O Que Você Precisa Saber na icecasino
Great post.
Feel free to surf to my web page: nordvpn coupons inspiresensation (http://t.co)
Aposte no Cassino bwin bet e Vença
Agora Mesmo!
ready-made accounts for sale account store
find accounts for sale website for selling accounts
Aposte e Ganhe com Facilidade no Cassino Online 1993 bet!
buy accounts website for selling accounts
Ganhe Prêmios Fantásticos com Jogos Populares no beta trinta!
Ganhe no Cassino wild bet com Jogos
Populares e Simples!
account market account buying platform
Aposte no bet sport – https://betsport-br.com: Cadastre-se
e Receba 100$ de Bônus Imediato!
O realsbet (realsbetcassino.com) oferece uma excelente oportunidade para quem deseja começar sua experiência no cassino
online com um bônus de 100$ para novos jogadores! Ao se registrar no
site, você garante esse bônus exclusivo
que pode ser utilizado em diversos jogos de cassino,
como slots, roleta e poker. Esse é o momento perfeito para explorar o mundo das apostas com um saldo
extra, aproveitando ao máximo suas apostas sem precisar investir um grande valor logo de início.
Não perca essa oportunidade e cadastre-se já!
Ao se cadastrar no doce888, você ganha um bônus de 100$ para começar sua jornada no cassino com o pé direito!
Não importa se você é um novato ou um apostador experiente,
o bônus de boas-vindas é a oportunidade perfeita para explorar todas
as opções que o site tem a oferecer. Jogue seus
jogos favoritos, descubra novas opções de apostas e
aproveite para testar estratégias sem risco, já que
o bônus ajuda a aumentar suas chances de ganhar.
Cadastre-se hoje e comece com 100$!
account acquisition marketplace for ready-made accounts
account trading buy accounts
account acquisition website for selling accounts
Bônus de 100$ ao Registrar-se no pague bet
– Comece a Apostar Já!
account market account exchange
Hi there mates, nice piece of writing and good arguments commented here,
I am genuinely enjoying by these.
verified accounts for sale sell account
account sale buy and sell accounts
database of accounts for sale gaming account marketplace
A futebol ao vivo cuida de
sua segurança financeira, permitindo que você retire seus fundos sem preocupações, desde que
envie os documentos corretos.
Faça seu Cadastro no jogos win – https://jogos-win.com e Ganhe 100$ para Começar a Jogar!
buy accounts secure account purchasing platform
Всегда есть что-то интересное из актуального порно онлайн:
16 летние девушки порно
account buying platform buy accounts
account acquisition database of accounts for sale
Всегда есть что-то интересное из актуального порно онлайн:
13 летние девушки порно
account trading service account selling platform
I’m not sure where you are getting your info, but great topic.
I needs to spend some time learning more or understanding more.
Thanks for excellent information I was looking for this info for my mission.
My web-site … nordvpn coupons inspiresensation
Всегда есть что-то интересное из актуального порно онлайн:
детское порно видео
account trading platform account store
account exchange service accounts for sale
Всегда есть что-то интересное из актуального порно онлайн:
детское порно видео
futebol na tv ao vivo hoje: Como Retirar Seus Fundos
de Forma Eficiente
My spouse and I absolutely love your blog and find a lot of
your post’s to be what precisely I’m looking for. Does one
offer guest writers to write content to suit your needs?
I wouldn’t mind creating a post or elaborating on many of the subjects
you write with regards to here. Again, awesome weblog!
Also visit my webpage; nordvpn coupons inspiresensation
account trading account trading platform
gaming account marketplace account catalog
Quais São as Formas de Saque na futmax futebol ao vivo e Como Elas Garantem Sua Segurança?
Всегда есть что-то интересное из актуального порно онлайн:
видео детского порно
find accounts for sale account store
Como Realizar Saques na futebol na tv ao vivo com Facilidade e Segurança
Passo a Passo para Retirar Seus Ganhos na futebol agora ao vivo: Agilidade e Segurança
Saque Rápido e Seguro: Como a tv ao vivo futebol
Protege Seus Ganhos
A futebol ao vivo cruzeiro oferece
um processo de saque simples e rápido. Basta fornecer os documentos exigidos e seus ganhos
serão transferidos para você.
Como Garantir Saques Rápidos e Seguros na futebol ao vivo brasil
apk futebol ao vivo: Dicas
para Realizar Saques Rápidos e Sem Problemas
A Importância da Verificação de Documentos no Saque da futebol rei ao vivo
Se você busca uma maneira segura de retirar seus ganhos, a futebol placar ao vivo é a melhor escolha.
Envie os documentos solicitados e pronto!
O processo de retirada na futebol ao vivo e gratis é muito simples.
Basta enviar os documentos solicitados e a plataforma processa rapidamente seu saque.
Всегда есть что-то интересное из актуального порно онлайн:
17 летние девушки порно
Quais Documentos Você Precisa Enviar para Realizar um
Saque na futebol ao vivo in?
account buying platform marketplace for ready-made accounts
Na ao vivo na tv futebol,
você pode sacar seus fundos com rapidez, apenas fornecendo um
documento de identidade e um comprovante de residência.
Saques Sem Complicação: Como Retirar Seus Ganhos na
placar futebol ao vivo
Guia Completo de Saque: Como Evitar Complicações na futebol ao vivo on line
Como Sacar Seus Ganhos na site futebol ao vivo de Forma Rápida e Segura
I was wondering if you ever considered changing the page layout of your website?
Its very well written; I love what youve got to say.
But maybe you could a little more in the way of content so people could connect with it
better. Youve got an awful lot of text for only having 1 or
2 images. Maybe you could space it out better?
Here is my site … nordvpn coupons inspiresensation
A premiere futebol ao vivo
oferece saques rápidos com total segurança, desde que você envie os documentos corretos.
A app futebol ao vivo gr谩tis oferece um processo de saque simples e seguro, garantindo que suas informações financeiras estarão sempre protegidas.
buy account account buying platform
purchase ready-made accounts guaranteed accounts
find accounts for sale buy accounts
Всегда есть что-то интересное из актуального порно онлайн:
детское порно видео
sell account accounts-store.org
I was recommended this website by my cousin. I’m
not sure whether this post is written by him as no one else know such detailed about my trouble.
You are incredible! Thanks!
Here is my page nordvpn coupons inspiresensation (http://t.co/3I68DHXKpG)
Всегда есть что-то интересное из актуального порно онлайн:
7 летние девушки порно
buy account purchase ready-made accounts
online account store marketplace for ready-made accounts
ready-made accounts for sale secure account sales
Codziennie masz szansę na zdobycie nawet 10 000 darmowych spinów Slottica PL lub wygranie tysięcy złotych w turniejach. Dodatkowo oferujemy nagrody rzeczowe o łącznej wartości do 875 000 zł! W puli nagród znajdują się m.in. smartfony Samsung, zestawy Apple, luksusowe zegarki i profesjonalne monitory komputerowe.
Всегда есть что-то интересное из актуального порно онлайн:
детское порно стрим
Всегда есть что-то интересное из актуального порно онлайн:
15 летние девушки порно
O bet7 oferece uma excelente oportunidade para quem deseja começar sua experiência no cassino online
com um bônus de 100$ para novos jogadores! Ao se registrar no site,
você garante esse bônus exclusivo que pode ser utilizado em
diversos jogos de cassino, como slots, roleta e poker.
Esse é o momento perfeito para explorar o mundo das apostas com um
saldo extra, aproveitando ao máximo suas apostas sem precisar investir um grande valor logo
de início. Não perca essa oportunidade e cadastre-se já!
Registre-se no bet 7k – https://bet-7k.com e Comece a Apostar com
100$ de Bônus!
No doce, ao Registrar-se, Você Recebe 100$ de Bônus!
infinity bet: Onde a Sorte Encontra os Melhores Jogadores!
Cadastre-se no fuwin e
Ganhe 100$ de Bônus de Boas-Vindas!
Всегда есть что-то интересное из актуального порно онлайн:
10 летние девушки порно